NCCoE Buzz: Mobile Security Edition
The NCCoE Buzz: Mobile Security Edition discusses timely topics in mobile device cybersecurity and privacy from the NCCoE’s Mobile Device Security project team.
NCCoE Buzz: Mobile Security Edition Series
Browse all published issues of the NCCoE Buzz: Mobile Edition.
The NCCoE Buzz: Mobile Security Edition
Have you ever thought about having your driver’s license on your mobile phone?
In the last two decades, mobile devices have revolutionized the way we live, work, and connect with each other across the globe. From communication and information access to productivity and entertainment, the prevalence of mobile devices in our everyday lives is undeniable.
As the world rapidly evolves and technology redefines how we interact with our surroundings, a significant innovation that holds the potential to transform our daily lives is the Mobile Driver’s License (mDL). This digital evolution of the traditional physical driver’s license brings numerous benefits and conveniences to drivers but can also present security and privacy challenges that we must address.
mDL Definition
An mDL is a digital representation of a driver’s license on a mobile device. It contains all the essential information found on a physical driver’s license, including the driver’s name, photo, date of birth, and driving privileges. An mDL also has the capability to be updated in real time.

Learn More: mDL Project at the National Cybersecurity Center of Excellence (NCCoE)
Experts at the NCCoE are working with industry, government agencies, and academic institutions to research and implement international standards (ISO/IEC 18013-5 and ISO/IEC 18013-7) on mDLs. These standards are being developed to provide improved usability, convenience, and stronger security in digital identity management.
The mDL project will define and facilitate one or more reference architectures that protect privacy, provide secure implementation, enable equity, allow widespread adoption, and facilitate ease-of-use by:
- Building an open-source reference implementation that will retrieve digital driver’s license information from the mobile device
- Demonstrating different use cases to access the ID stored on the device
- Developing a practice guide that includes mDL design, architecture, and leading practices
If you would like more information on the Digital Identities - mDL project, consider joining the Community of Interest. Visit the mDL webpage for more information.
Did you know that mobile devices were initially only used as personal consumer communication devices? Today devices are used to access modern networks and systems that process sensitive data and are often integrated across organizations’ enterprises. With this in mind, organizations need strategies that holistically address mobile security concerns, including mitigations and countermeasures.
In an effort to assist organizations with these deployment strategies, the National Institute of Standards and Technology (NIST) recently released Revision 2 of NIST Special Publication (SP) 800-124, Guidelines for Managing the Security of Mobile Devices in the Enterprise. The publication provides a five-step enterprise mobile device deployment life cycle to help organizations build and manage the security of their deployment:
-
Identify Mobile Requirements. In the first stage of the life cycle, mobile mission needs and requirements are defined. Devices are inventoried, and the deployment model such as Bring Your Own Device (BYOD) or Corporate-Owned and Personally-Enabled (COPE) is selected.
-
Perform Risk Assessment. Risk is identified, estimated, and prioritized. Risk assessments should be performed on a regular basis since risks to enterprise systems are always evolving.
-
Implement Enterprise Mobility Strategy. Mobile technology is selected and installed; an Enterprise Mobility Management (EMM) system is deployed, policies and configurations are created and provisioned to enrolled devices, and system testing is employed. The implementation stage can include additional security- and privacy-enhancing technologies, such as a Virtual Private Network (VPN) or a Mobile Threat Defense (MTD) service.
-
Operate and Maintain. An initial set of controls is deployed and then periodic audits can evaluate the effectiveness of the security controls. This allows for adjustments to efficiently meet mission needs and improve security posture.
-
Dispose of and/or Reuse Devices. This step outlines how to prevent sensitive information stored on a mobile device from falling into the wrong hands when a device is no longer in use.
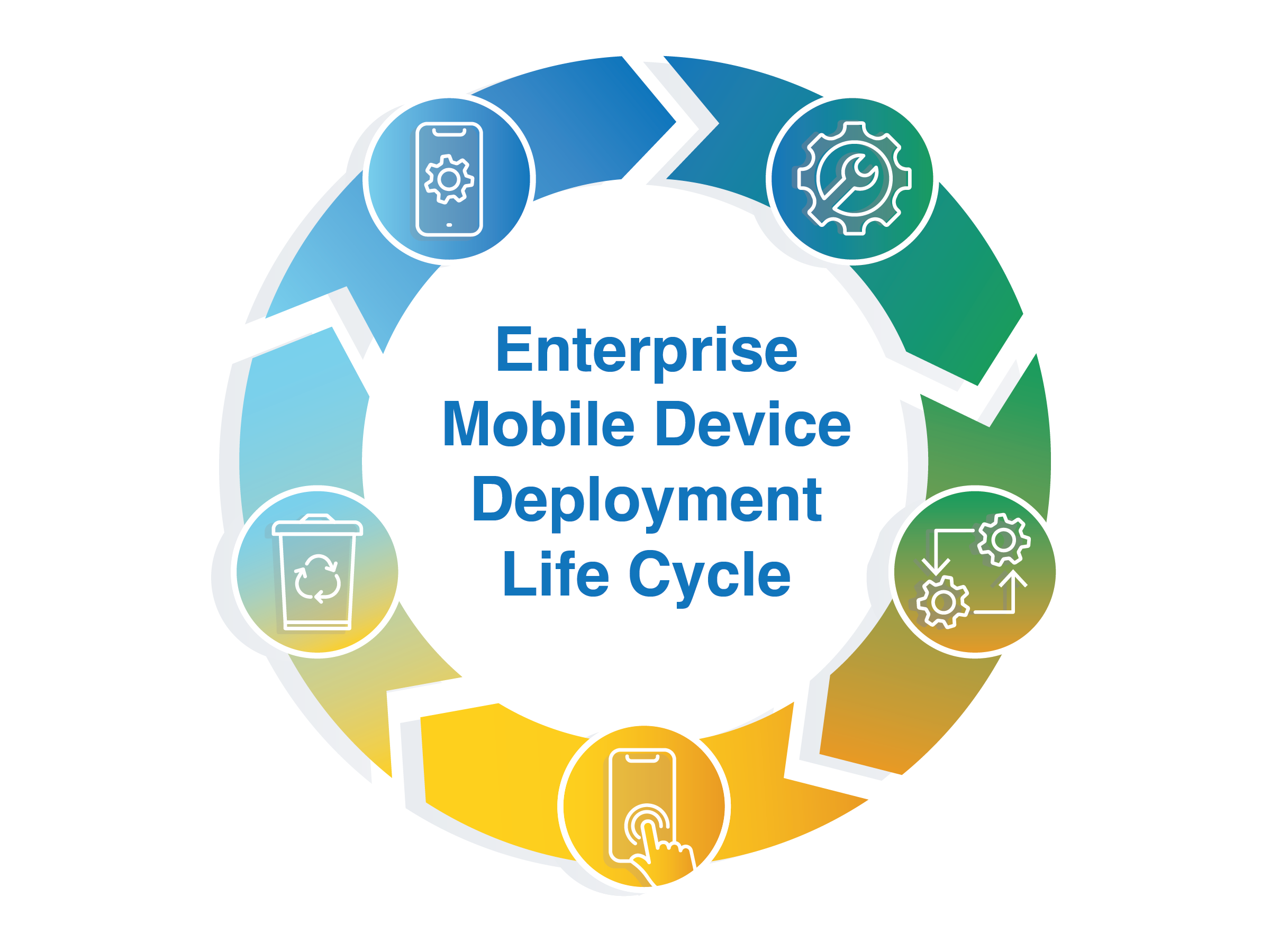
To learn more about NIST Special Publication (SP) 800-124, Guidelines for Managing the Security of Mobile Devices in the Enterprise or to download a copy of the guide, visit the publication page.
What is it?
Mobile devices allow employees to conveniently do their work from home, at the office, or on the go. While this provides flexibility and convenience, it could expose an organization to potential threats. Managing mobile devices’ security and device health is vital to minimizing an organization’s risk posture.
Mobile device management (MDM), sometimes included within a unified endpoint management (UEM) solution, is an enterprise tool that allows organizations to secure mobile devices that are used to access organizational resources. An employee’s personal or corporate-owned device can be enrolled into an MDM solution to apply enterprise configurations, manage enterprise applications, and enforce compliance with enterprise policies.
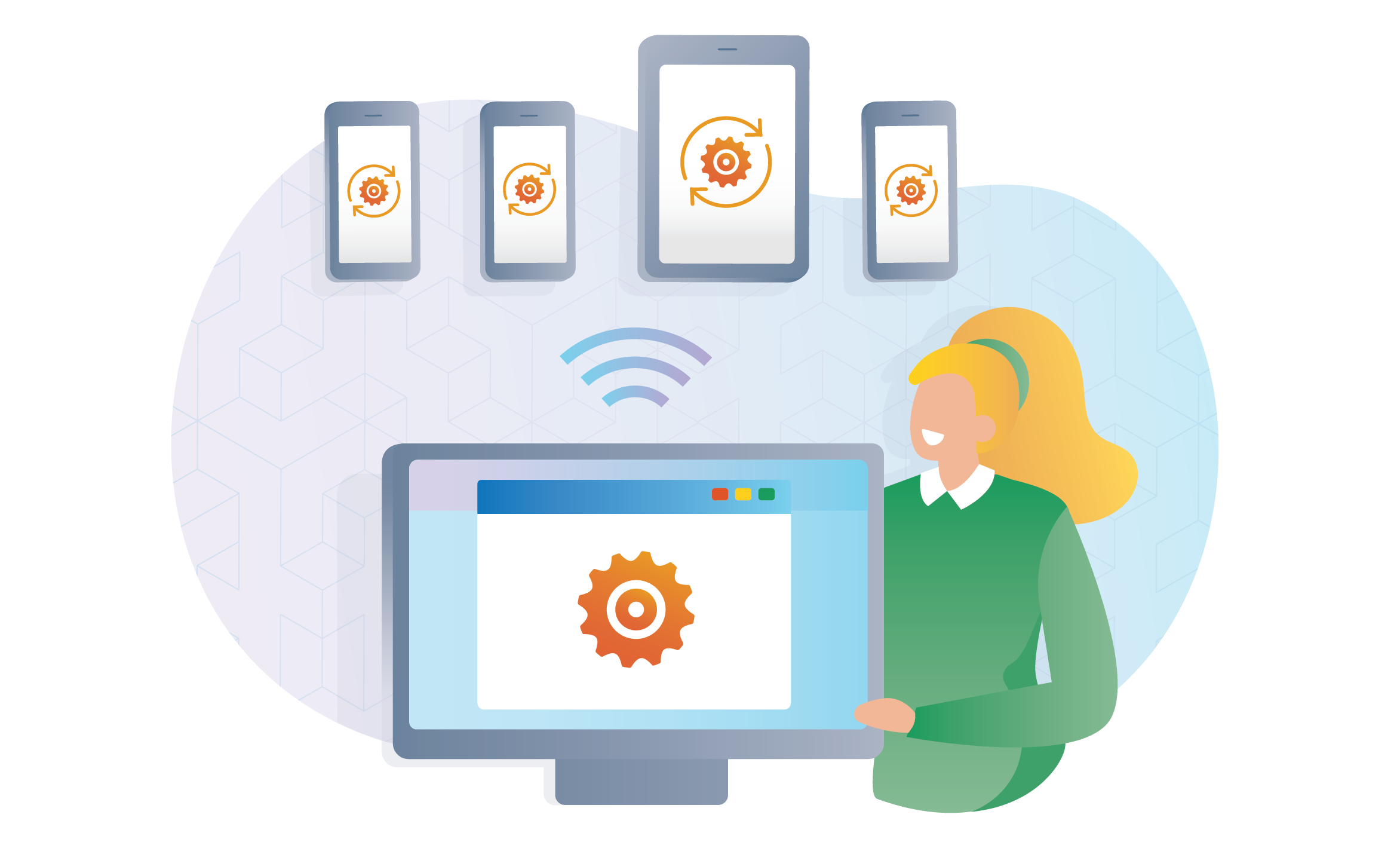
How does it work?
Mobile devices connect to the MDM solution via an application running on the device. Enterprise administrators use the MDM product to manage and enforce policies on connected devices. If a device is found out of compliance with a policy, an organization can enforce a compliance action.
Another common use for an MDM solution is installing and managing applications on the device that will be used for work. For example, the MDM can install an email application that is pre-configured with the user’s work login.
How does it address security and privacy concerns?
The main goal behind using an MDM solution is to ensure that devices are in a more secure state before allowing access to corporate resources. These policies can specify certain privacy- and security-enhancing configurations, such as requiring a passcode to unlock the device or preventing data loss by restricting copy/paste/screenshot capabilities.
In addition, privacy-preserving mechanisms are built into both the MDM and the devices themselves to limit unnecessary exposure of employees’ personal information. For example, when personal devices are used for work (i.e., bring your own device, or “BYOD”), the device has built-in mechanisms to ensure that personal and work data are completely separate, and that work applications cannot access any personal information on the device, such as pictures or SMS messages.
What can you do?
Download our SP 1800-21 and 1800-22 guides to learn more about mobile device management and other mobile device security and privacy capabilities, including how these solutions can strengthen the security and privacy of your enterprise environment.
What is it?
Imagine you’ve found “THE” mobile application to enhance your organization’s productivity. How do you know if the benefits outweigh the potential risks of installing the mobile app?
Mobile application vetting (MAV) services are used by enterprises to scan applications for potentially unwanted behavior. Application vetting can also be used to ensure that applications meet an organization’s security and privacy requirements.
How does it work?
MAV services use a variety of static, dynamic, and behavioral analysis techniques to determine if an application demonstrates any behaviors that pose a security or privacy risk. Once analysis is complete, the MAV tool generates a comprehensive report of the application’s security and privacy characteristics.

How does it address security and privacy concerns?
MAV services provide organizations with the information necessary to make risk-based decisions when selecting/developing mobile applications for the organization. The report from the application vetting service contains various findings, such as the use of in-app purchases, insecure network communications, or exposure of sensitive personal or device information. Based on these findings, enterprises can make informed decisions on whether to block problematic applications from being installed on company devices.
What can you do?
Download our SP 1800-21 and 1800-22 guides to learn more about application vetting and other mobile device security and privacy capabilities, including how these solutions can strengthen the security of your enterprise environment.
What is it?
Mobile threat defense (MTD) is an application that provides real-time information about a device’s risk level.
How does it work?
An MTD application is installed on a mobile device. The app then detects unwanted activity and informs users and/or system administrators so they can prevent or limit damage. MTD uses the device’s application programming interfaces (APIs) to obtain information about potential threats. These threats may include an adversary-in-the-middle attack or a phishing attempt.
MTD applications can provide enhanced security when integrated with a mobile device management system. These integrations allow the MTD to report any risks back to the management software. In response, the management system can then take action based on the identified risk and its impact to an enterprise security policy.
How does it address security and privacy concerns?
MTD software analyzes and informs the user or organization of a security threat or privacy risk. For example, MTD notifies individuals when they should update their operating systems. The app can also alert users when someone is eavesdropping on their internet connection. With this awareness, individuals or organizations are then able to resolve these threats.

What can you do?
Download our 1800-21 and 1800-22 guides to learn more about MTD and other mobile device security and privacy capabilities, including how these solutions can strengthen the security of your enterprise environment.
Our mobile devices today are powerful handheld computers in our pockets. Many of us store valuable personal information on our phones, turning these devices into attractive targets for hackers. With this in mind, how can we effectively protect ourselves from data leaks?
Data leaks happen when an organization or an individual loses control of their information. Control of the data may be lost due to unauthorized or unwarranted transmission of data to an external source. Mobile data leaks can also occur when mobile device privacy settings or applications are misconfigured.
To learn more about the different types of data leaks and how you can best protect your device, check out our recent guidance here.

It’s that time of the year again when we get on the road or head to the airport for a holiday vacation. It may be convenient to use public wireless networks while traveling. However, an ineffectively secured mobile device that establishes a connection to an open public Wi-Fi hotspot may expose an individual, employee, or entire organization to data loss or a privacy compromise.
The NCCoE wishes you a happy Thanksgiving and safe travels. To learn more about how you can protect your mobile device while using public Wi-Fi, access our article here.

With Halloween around the corner, the National Cybersecurity Center of Excellence (NCCoE) wants to share a few “tricks” and tips for mobile passwords that result in the “treat” of protecting your mobile device from compromise.

Potential Threats:
Below is a list of several potential mobile password threats that can impact you or your organization:
- Lost/Stolen Phone – If an unauthorized user obtains a lost or stolen mobile phone that has no password, they may have easy access to sensitive information on the device (e.g., messages, photos, or email)
- Brute-Force Attack – If a mobile phone has a weak password, a malicious attacker may be able to easily obtain the password and gain access to information on the mobile phone
- Phishing – If a password is captured by texting or emailing to convince a user or subscriber into thinking the attacker is a verifier or reliable party, the attacker can gain access to a user’s account(s) and access sensitive information
Password Protections:
To protect against mobile password threats, here are a few tips:
1. Apply multi-factor authentication.
If a password is compromised, requiring a second factor for authentication can help protect against threats such as phishing attacks.
Multi-factor authentication can be any combination of the following:
- Something you know – Password, pin, etc.
- Something you have – Authenticator app, hardware token, etc.
- Something you are – Biometrics (e.g., fingerprint or face recognition)
For example, if an attacker has acquired your password (something you know) through a phishing attack, but your account requires a password + your fingerprint (something you are) to grant access, then the attacker will not be able to access your account because they do not have access to the second factor.
2. Choose a password with a minimum length of 8 characters.
A common misconception is that complexity is the key to having a strong password. NIST SP 800-63B highlights that complexity can actually make it difficult for the user to remember their password and can deter them from developing a strong memorable password.
Instead, 800-63B recommends creating a memorable password that is at least 8 characters in length to help prevent against brute-force attacks, while also ensuring the user can remember their password/pin/passphrase.
We hope these mobile password tricks and treats were helpful.
Additional Resources:
- More information about how to use and apply specific authenticators can be found in NIST Special Publication 800-63B Digital Identity Guidelines: Authentication and Lifecycle Management.
- More information on how to protect against other potential mobile threats can be found in NIST SP 1800-22 Mobile Device Security: Bring Your Own Device.
Many professionals in the cybersecurity community are talking about zero trust architecture (ZTA), and although it is not a new concept, there is renewed interest in implementing zero-trust principles. This introduces challenges for an organization’s mobile administrators. But what does zero trust really mean for mobile?
Due to the pandemic, many employees have transitioned to remote/telework options to accomplish their daily work activities. The portability of mobile devices makes it easier to respond promptly to emails, attend virtual meetings, and use special work apps from anywhere, even in your own home. They also serve as backup devices when the primary computing devices are not functioning properly at remote sites.
In this new environment, mobile devices are now another endpoint connected to enterprise resources and can put the entire enterprise at risk if compromised or stolen. ZTAs can minimize this impact by applying cybersecurity practices that assume no implicit trust, constant monitoring, and restricted access to the enterprise resources based on the criticality of resources and user and device identity and posture.

So, how do you get started?
When considering implementing a ZTA, it helps to first clarify the fundamental tenets. Recently, NIST Computer Scientist Gema Howell published an article on the RSAC Blog clarifying the role of ZTA for the mobile device security community and how to implement a ZTA based on standard practices.
Want to learn more? Check out our resources below:
View full article on RSAC Blog
Read NIST Special Publication 800-207 Zero Trust Architecture
When organizations allow employees to use mobile devices for work (e.g., Bring Your Own Device/BYOD), there are potential privacy implications that can impact employees. Privacy and cybersecurity are commonly thought of as two distinct areas, but when considering the risks of each, they often intersect.
Below is a list of 7 privacy challenges for enterprise mobile deployments, some of which arise from cybersecurity-related risks:

View the full-sized infographic here.
From data leaks to phishing attacks, mobile security threats are on the rise. In a previous edition of the Buzz from the National Cybersecurity Center of Excellence (NCCoE), we provided insights into how to prioritize mobile threats using the NIST Mobile Threat Catalogue (MTC).

Did you also know…?
NIST’s MTC provides links to mobile threats highlighted in the Department of Homeland Security’s sponsored Common Vulnerabilities and Exposures (CVE®) database, which identifies, defines, and catalogs publicly disclosed cybersecurity vulnerabilities. This additional detail is likely to prove very useful in prioritizing mobile threats.
Joining forces: NIST Mobile Threat Catalogue and MITRE ATT&CK®
NIST collaborates with The MITRE Corporation on finding solutions to pressing cybersecurity issues. Thanks to this synergy, a crosswalk back to NIST’s Mobile Threat Catalogue can be found in MITRE’s ATT&CK® for Mobile. MITRE’s ATT&CK® for Mobile highlights adversarial tactics, techniques, and procedures to help secure mobile devices and detect adversarial behavior as part of the larger MITRE ATT&CK® knowledgebase. For administrators running two common phone types in their organization, they will be happy to know that MITRE ATT&CK® for Mobile documents both Android and iOS adversarial techniques.
How do you use these resources together?
NIST’s MTC identifies over 200 current threats, including carrier and application threats. The catalog also identifies physical device, supply chain, and additional threats that are cross-referenced in MITRE ATT&CK® for Mobile. The MTC’s links to the Common Vulnerabilities and Exposures (CVE®) database provide additional depth of information when needed.
We hope this information provides a great place to start as you develop your mobile device security strategy for a safer working environment.
Are you looking to protect your enterprise data from phishing? According to the Cybersecurity & Infrastructure Security Agency (CISA), most phishing attempts come by email, while other attacks—including text messages (SMS)—are also on the rise. Awareness of the different types of phishing attacks are key for implementing comprehensive mobile device security.

It is important to keep in mind that cybercriminals target a range of vulnerable actors: individuals, small and medium enterprises, and large organizations. Ultimately, any of us could be affected. Phishing attacks are not just limited to laptops or desktops; mobile phones can be the target of phishing attacks as well.
The National Cybersecurity Center of Excellence (NCCoE) has developed guidance to help protect mobile devices from phishing threats. We provide example solution architectures that organizations can use to help improve their information security and privacy. To learn more about how to protect your mobile device from phishing attacks, view our latest short form paper on phishing protection.
How do you prioritize your security approach when faced with hundreds of mobile threats? There are many types of mobile threats and they come from a variety of sources. From application-based threats to an adversary-in-the-middle, the possibilities can be overwhelming.
In response, the NCCoE compiled a list of the most common mobile device threats to help organizations prioritize their solutions according to the likelihood of an attack.
To learn more, check out our infographic here.
Are you looking to deploy mobile devices within your organization? We know that it can be challenging to comb the internet trying to figure out which threats you should be paying attention to when considering your deployment strategy.

To address this challenge, the NIST Mobile Threat Catalogue (MTC) describes, identifies, and structures the threats posed to mobile devices and their associated infrastructure. The MTC offers several uses and opportunities, including:
- the ability to review threats when performing a risk analysis or threat modeling
- correlation with ATT&CK for mobile
- the ability to contribute to the catalogue (e.g., suggest new threats or remove old threats)
The MTC was created to be a living catalogue that is regularly updated according to the latest threat landscape. We encourage the community to review the current contents and provide feedback or contributions to the catalogue.
Access the mobile threat catalogue here.
Let's face it, our mobile phones keep everything we hold dear...our photos, our financials, our contacts. We use them for everyday life, which can include our daily work activities. Privacy challenges can arise when personal and work data are stored on the same device.
Knowing where to start when considering privacy can result in increasing your employees’ trust in using their mobile devices for work purposes.
NIST offers several privacy tools that can be used to analyze, assess, manage, and mitigate your employee’s privacy concerns. With regards to mobile device solutions, NIST demonstrates how to use these privacy tools in two common mobile device use cases: Corporate-Owned Personally-Enabled (COPE) and Bring Your Own Device (BYOD).
To learn more about this topic, access our short-form article here.
