Appendix A List of Acronyms¶
ACA |
Attestation Certificate Authority |
AIC |
Attestation Identity Credential |
API |
Application Programming Interface |
BIOS |
Basic Input/Output System |
C-SCRM |
Cyber Supply Chain Risk Management |
CA |
Certificate Authority |
CDM |
Continuous Diagnostics and Mitigation |
CMSL |
(HP) Client Management Script Library |
CSR |
Certificate Signing Request |
DevID |
Device Identity |
DHCP |
Dynamic Host Client Protocol |
DICE |
Device Identifier Composition Engine |
DIMM |
Dual In-Line Memory Module |
DPD |
Direct Platform Data |
DTD |
Dell Trusted Device |
EFI |
Extensible Firmware Interface |
EK |
Endorsement Key |
ESP |
EFI System Partition Storage |
FIPS |
Federal Information Processing Standards |
FTP |
File Transfer Protocol |
GIDEP |
Government-Industry Data Exchange Program |
GRC |
Governance, Risk, and Compliance |
HIRS |
Host Integrity at Runtime and Start-Up |
HTTP |
Hypertext Transfer Protocol |
HTTPS |
Hypertext Transfer Protocol Secure |
IAK |
Initial Attestation Key |
ICT |
Information and Communications Technology |
IDevID |
Initial Device Identity |
iDRAC |
Dell Remote Access Controller |
IoT |
Internet of Things |
IT |
Information Technology |
JSON |
JavaScript Object Notation |
NCCoE |
National Cybersecurity Center of Excellence |
NIC |
Network Interface Card |
NIST |
National Institute of Standards and Technology |
NvRAM |
Non-Volatile Random-Access Memory |
OEM |
Original Equipment Manufacturer |
OS |
Operating System |
OT |
Operational Technology |
PACCOR |
Platform Attribute Certificate Creator |
PCR |
Platform Configuration Register |
PCVT |
Platform Certificate Verification Tool |
PXE |
Preboot Execution Environment |
REST |
Representational State Transfer |
RIM |
Reference Integrity Manifest |
SaaS |
Software as a Service |
SCRM |
Supply Chain Risk Management |
SCV |
Secured Component Verification |
SDA |
Secure Device Authentication |
SDLC |
System Development Life Cycle |
SecCM |
Security-Focused Configuration Management |
SFTP |
Secure File Transfer Protocol |
SIEM |
Security Information and Event Management |
SMBIOS |
System Management BIOS |
SOC |
Security Operations Center |
SP |
Special Publication |
SPDM |
Security Protocol and Data Model |
TCG |
Trusted Computing Group |
TFTP |
Trivial File Transfer Protocol |
TPer |
Trusted Peripheral |
TPM |
Trusted Platform Module |
TSC |
(Intel) Transparent Supply Chain |
UEFI |
Unified Extensible Firmware Interface |
UUID |
Universally Unique Identifier |
VAR |
Value-Added Reseller |
WMI |
Windows Management Instrumentation |
XML |
Extensible Markup Language |
XSLT |
Extensible Stylesheet Language Translation |
Appendix B References¶
- B1
T. Diamond et al., Validating the Integrity of Computing Devices: Supply Chain Assurance, National Institute of Standards and Technology (NIST), Gaithersburg, Md., March 2020, 14 pp. Available: https://www.nccoe.nist.gov/sites/default/files/library/project-descriptions/tpm-sca-project-description-final.pdf.
- B2
A. Regenscheid, Platform Firmware Resiliency Guidelines, NIST Special Publication (SP) 800-193, Gaithersburg, Md., May 2018, 45 pp. Available: https://doi.org/10.6028/NIST.SP.800-193.
- B3
J. Boyens et al., Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations, NIST SP 800-161 Revision 1, Gaithersburg, Md., May 2022, 326 pp. Available: https://doi.org/10.6028/NIST.SP.800-161r1.
- B4
Joint Task Force, Guide for Conducting Risk Assessments, NIST SP 800-30 Revision 1, Gaithersburg, Md., September 2012, 95 pp. Available: https://doi.org/10.6028/NIST.SP.800-30r1.
- B5
Joint Task Force, Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy, NIST SP 800-37 Revision 2, Gaithersburg, Md., December 2018, 183 pp. Available: https://doi.org/10.6028/NIST.SP.800-37r2.
- B6
*Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1*, NIST, Gaithersburg, Md., April 2018, 55 pp. Available: https://doi.org/10.6028/NIST.CSWP.04162018.
- B7
Joint Task Force, Security and Privacy Controls for Information Systems and Organizations, NIST SP 800-53 Revision 5, Gaithersburg, Md., September 2020, 492 pp. Available: https://doi.org/10.6028/NIST.SP.800-53r5.
- B8
*Trusted Platform Module Library Specification, Family “2.0,” Level 00, Revision 01.59,* Trusted Computing Group, November 2019. Available: https://trustedcomputinggroup.org/resource/tpm-library-specification/.
- B9
A. Johnson et al., Guide for Security-Focused Configuration Management of Information Systems, NIST SP 800-128, Gaithersburg, Md., August 2011, 99 pp. Available: https://doi.org/10.6028/NIST.SP.800-128.
- B10
Archer Platform Documentation, RSA. Available: https://community.rsa.com/t5/archer-platform-documentation/data-governance-design/ta-p/556139.
- B11
Introduction to Configuration Manager, Microsoft, June 2015. Available: https://help.archerirm.cloud/archer_suite_help/en-us/Content/portal_home.htm.
- B12
Host Integrity at Runtime and Start-up (HIRS): Attestation Certificate Authority (ACA) and TPM Provisioning with Trusted Computing-based Supply Chain Validation, 2020. Available: https://github.com/nsacyber/HIRS/.
- B13
TCG Platform Attribute Credential Profile, Specification Version 1.1, Revision 15, Trusted Computing Group (TCG), 2019, 61 pp. Available: https://trustedcomputinggroup.org/wp-content/uploads/IWG_Platform_Certificate_Profile_v1p1_r15_pubrev.pdf.
- B14
HP Secure Platform Management with the HP Client Management Script Library, HP Inc. Available: https://developers.hp.com/hp-client-management/blog/hp-secure-platform-management-hp-client-management-script-library.
- B15
Secure BIOS with HP Sure Admin and CMSL, HP Inc. Available: https://developers.hp.com/hp-client-management/blog/secure-bios-hp-sure-admin-and-cmsl-upd-292021.
- B16
HP Sure Start Whitepaper: Firmware Security and Resilience, HP Inc., 2021, 24 pp. Available: https://www8.hp.com/h20195/v2/getpdf.aspx/4AA7-6645ENW.pdf.
- B17
HP TamperLock: Protecting Devices from Physical Attacks, HP Inc., 2021, 6 pp. Available: https://www8.hp.com/h20195/v2/GetPDF.aspx/4AA7-8167ENW.pdf.
- B18
Transparent Supply Chain, Intel. Available: https://www.intel.com/content/www/us/en/products/docs/servers/transparent-supply-chain.html.
- B19
Platform Certificate Verification Tool, HPE. Available: https://github.com/HewlettPackard/PCVT.
- B20
TCG Credential Profiles For TPM Family 1.2; Level 2, Specification Version 1.2, Revision 8, Trusted Computing Group (TCG), 2013, 64 pp. Available: https://trustedcomputinggroup.org/wp-content/uploads/Credential_Profiles_V1.2_Level2_Revision8.pdf.
- B21
TPM 2.0 Keys for Device Identity and Attestation, Version 1.00, Revision 12, Trusted Computing Group, 2021, 71 pp. Available: https://trustedcomputinggroup.org/wp-content/uploads/TPM-2p0-Keys-for-Device-Identity-and-Attestation_v1_r12_pub10082021.pdf.
- B22
Symington et al., Trusted Internet of Things (IoT) Device Network-Layer Onboarding and Lifecycle Management, NIST Cybersecurity White Paper (Draft), Gaithersburg, Md., September 2020, 88 pp. Available: https://doi.org/10.6028/NIST.CSWP.09082020-draft.
Appendix C Project Scenario Sequence Diagrams¶
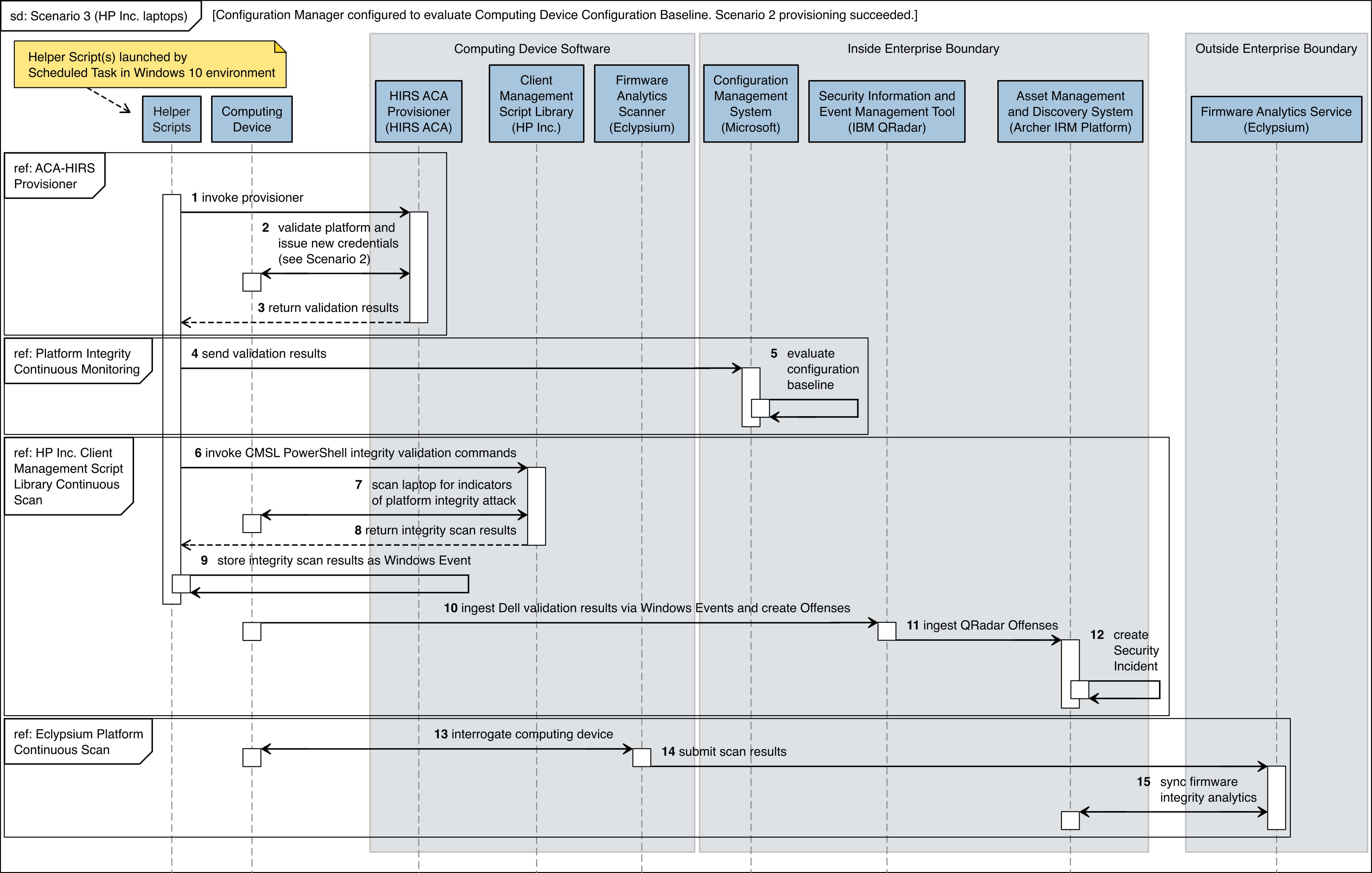
The figures in this appendix detail the flow of scenario interactions between a demonstration computing device and the supporting software/services. Note that not all scenarios were supported by every manufacturer. We have represented the software that is installed on the computing device and the platform integrity/provisioning services as blue boxes across the top. Steps that are part of a larger process are bounded by black boxes.
Figure C‑1 Dell and HP Inc. Laptop Scenario 2 Part 1
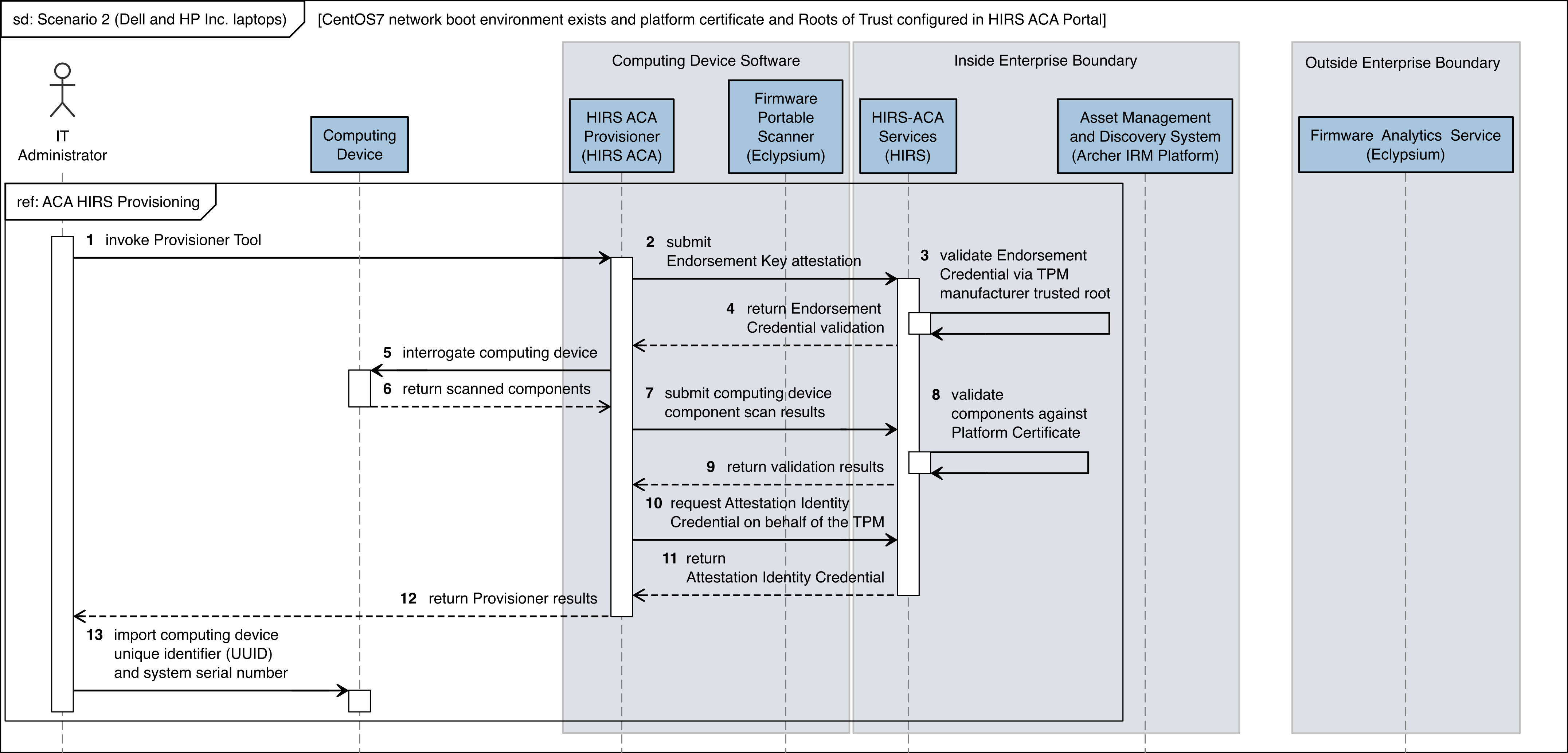
Figure C‑2 Dell and HP Inc. Laptop Scenario 2 Part 2
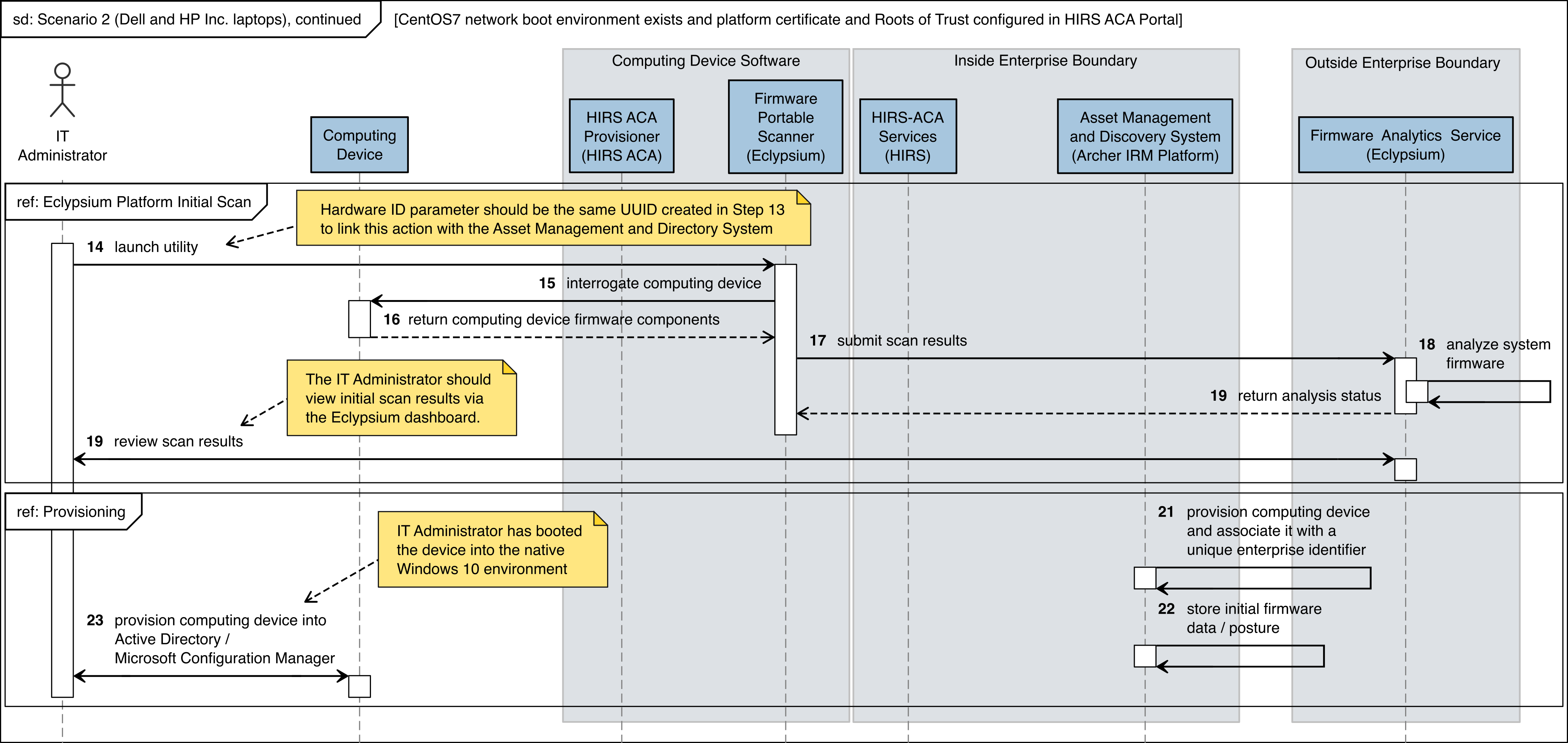
Figure C‑3 Intel Laptop Scenario 2 Part 1
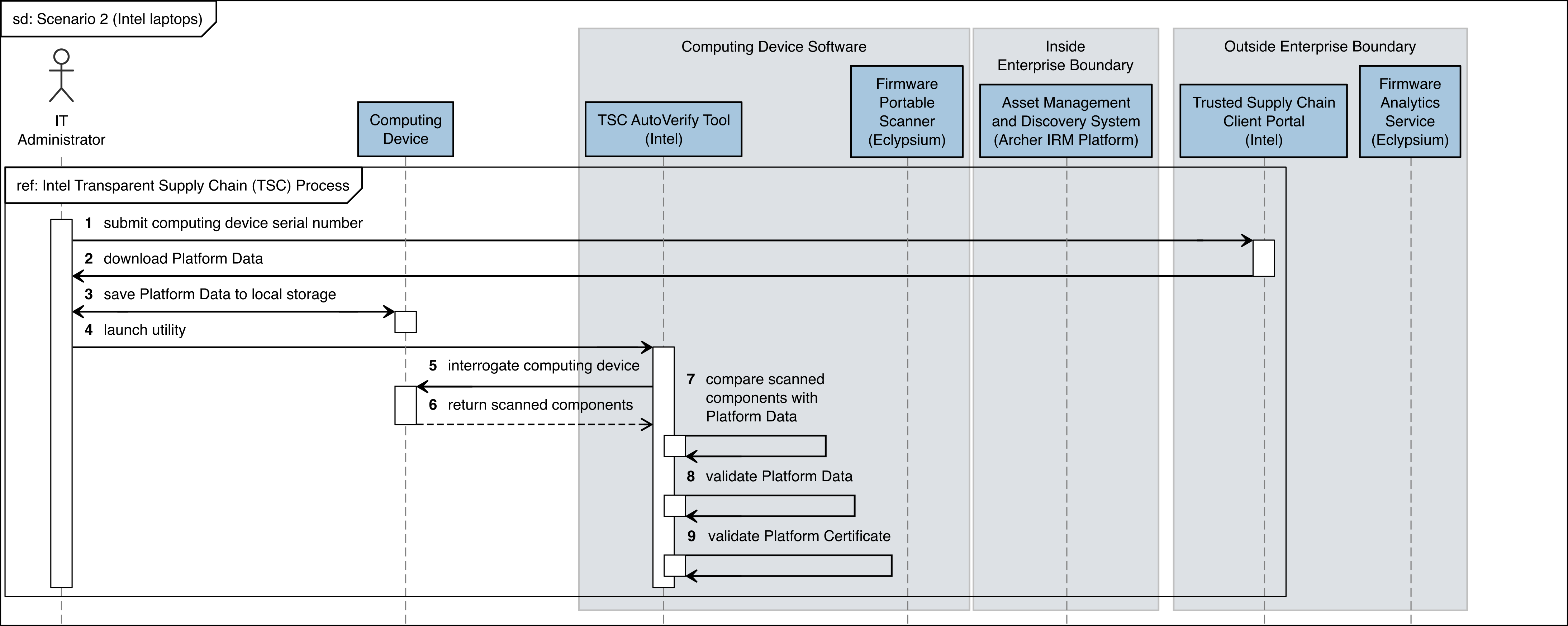
Figure C‑4 Intel Laptop Scenario 2 Part 2
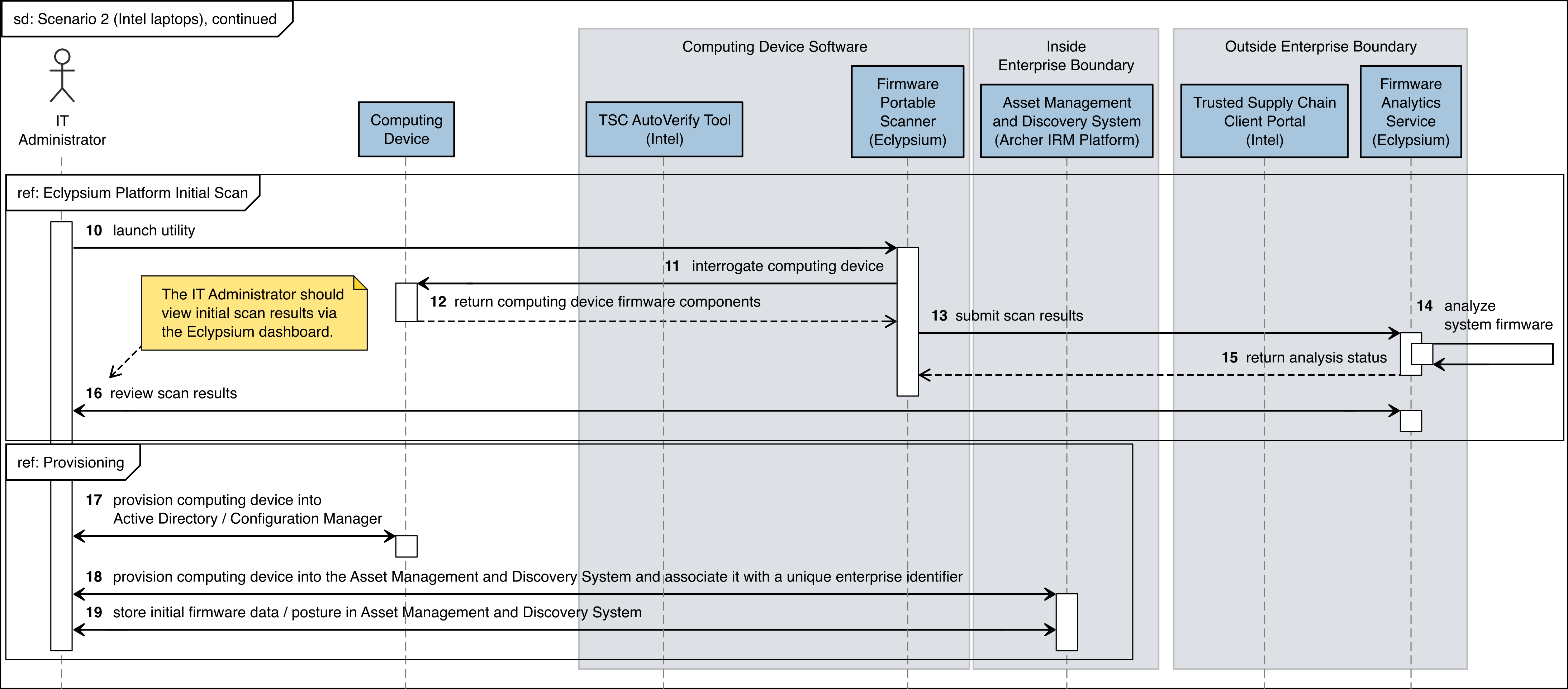
Figure C‑5 Intel Server Scenario 2 Part 1
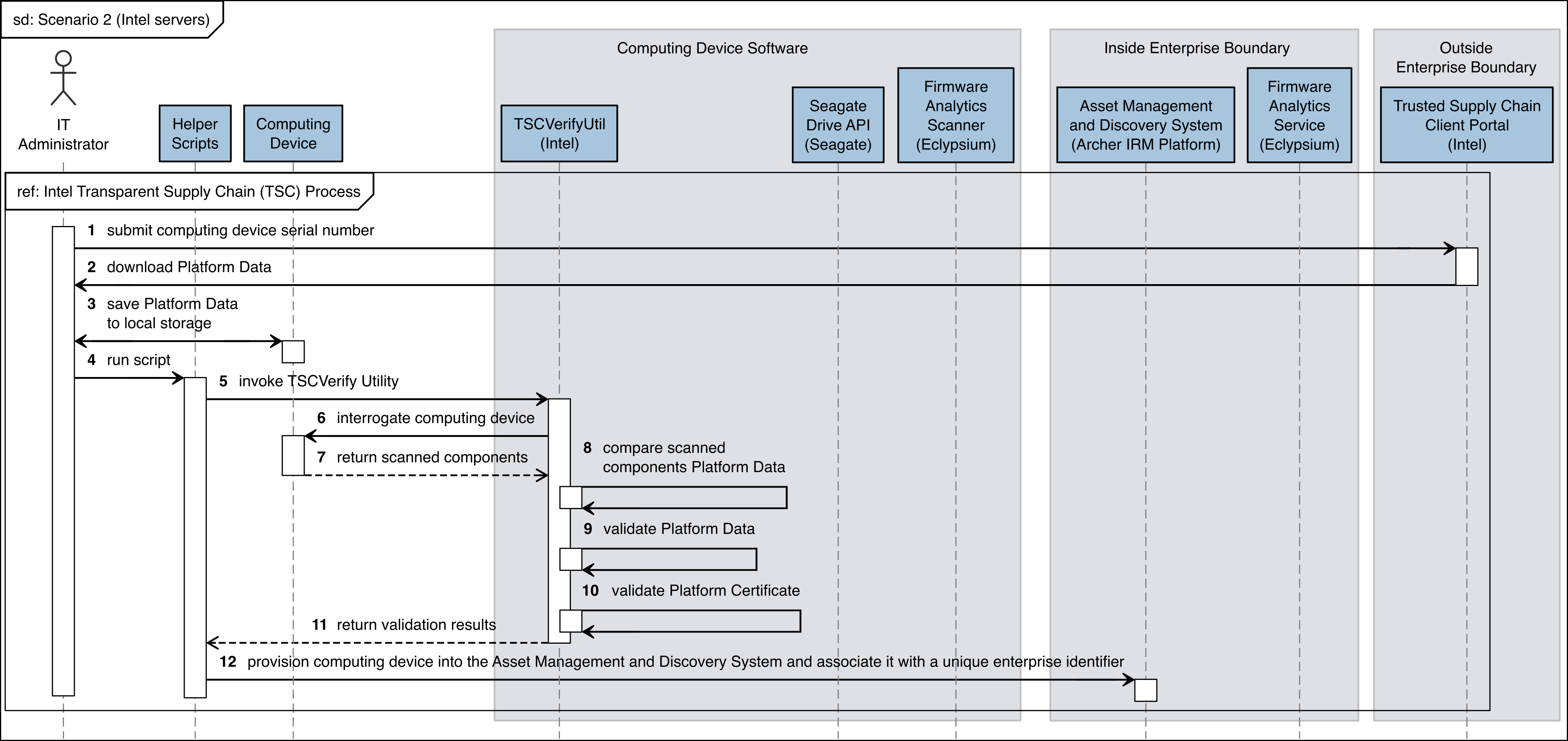
Figure C‑6 Intel Server Scenario 2 Part 2
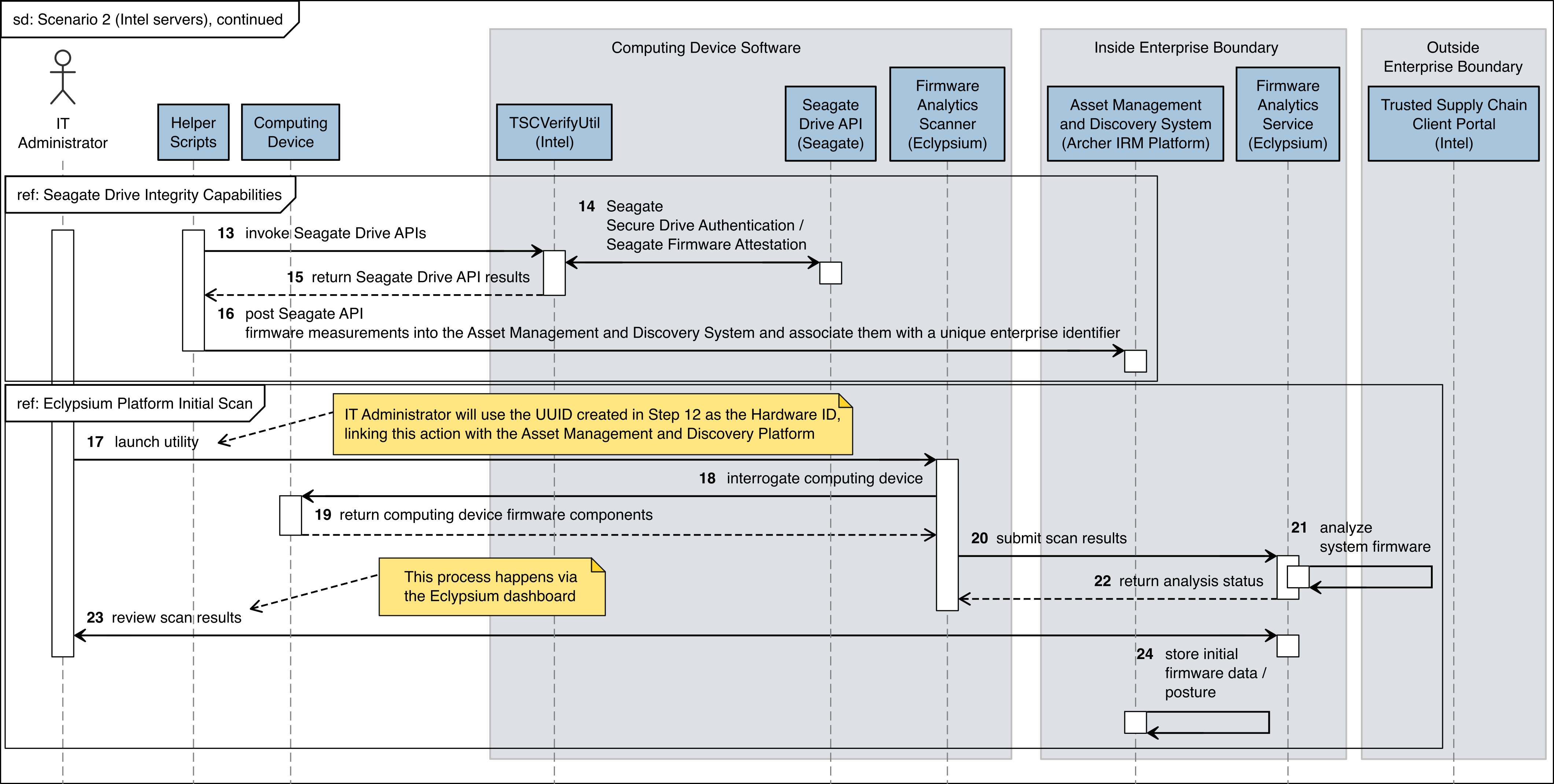
Figure C‑7 Dell Server Scenario 2
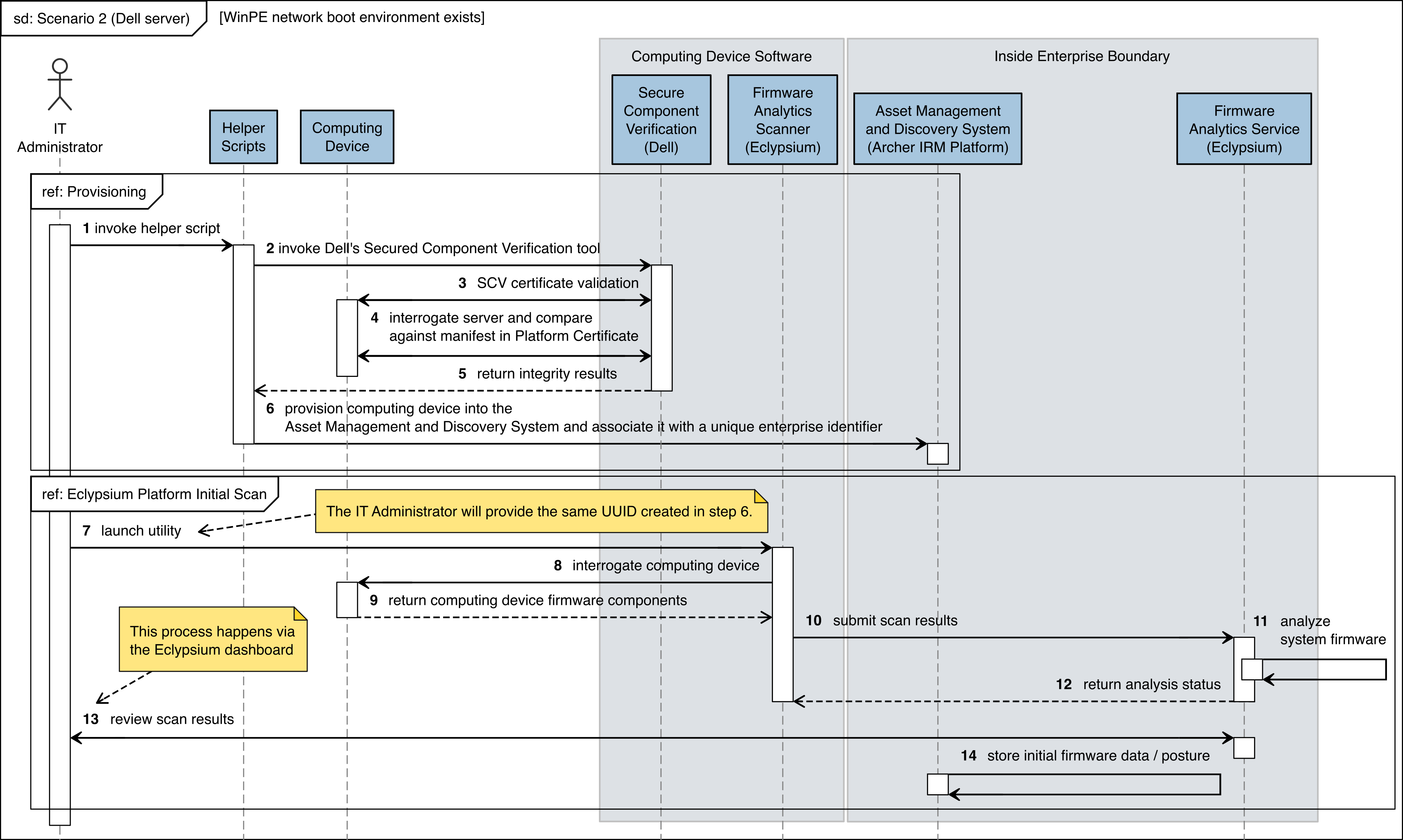
Figure C‑8 HPE Server Scenario 2
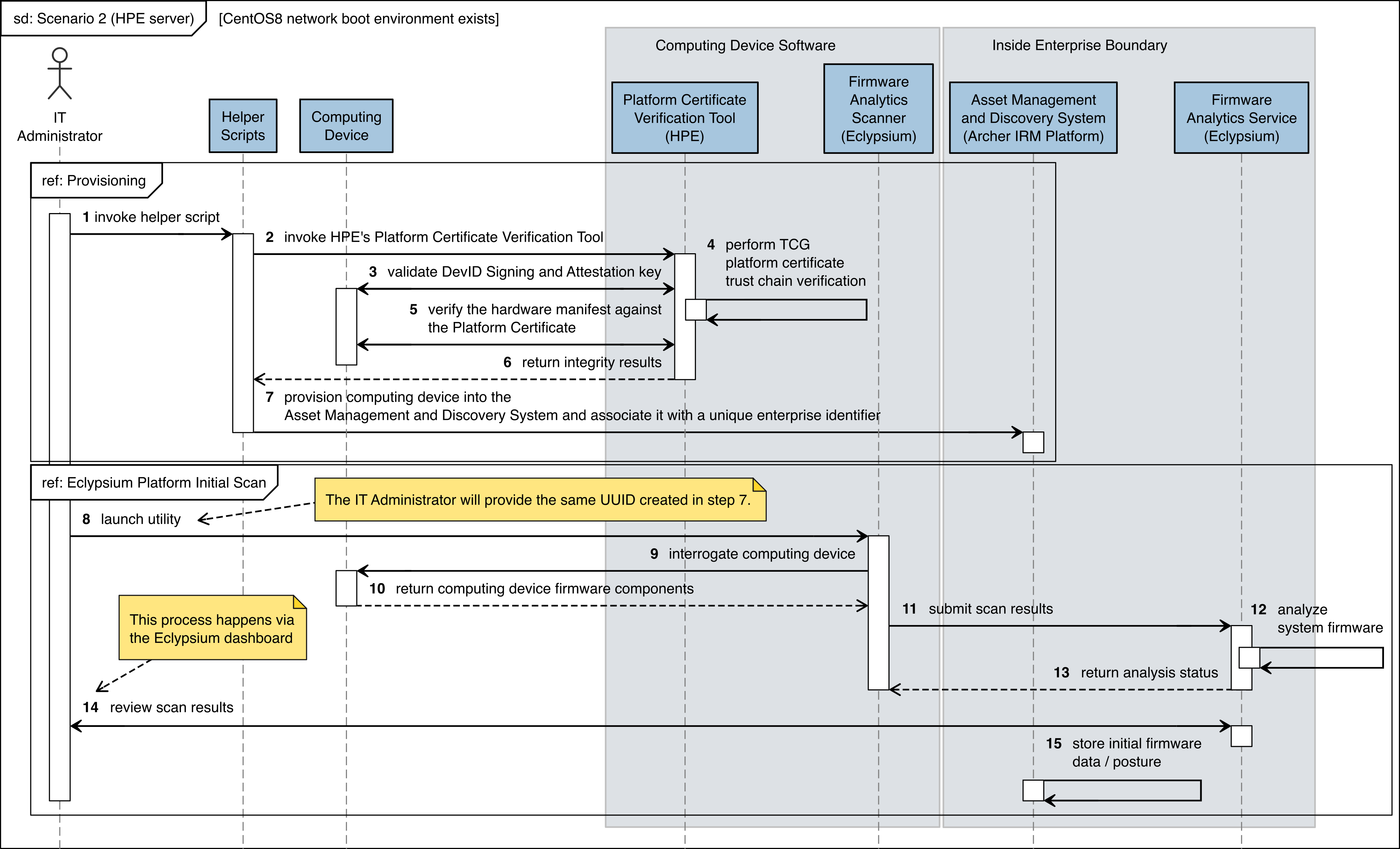
Figure C‑9 Intel Laptop Scenario 3
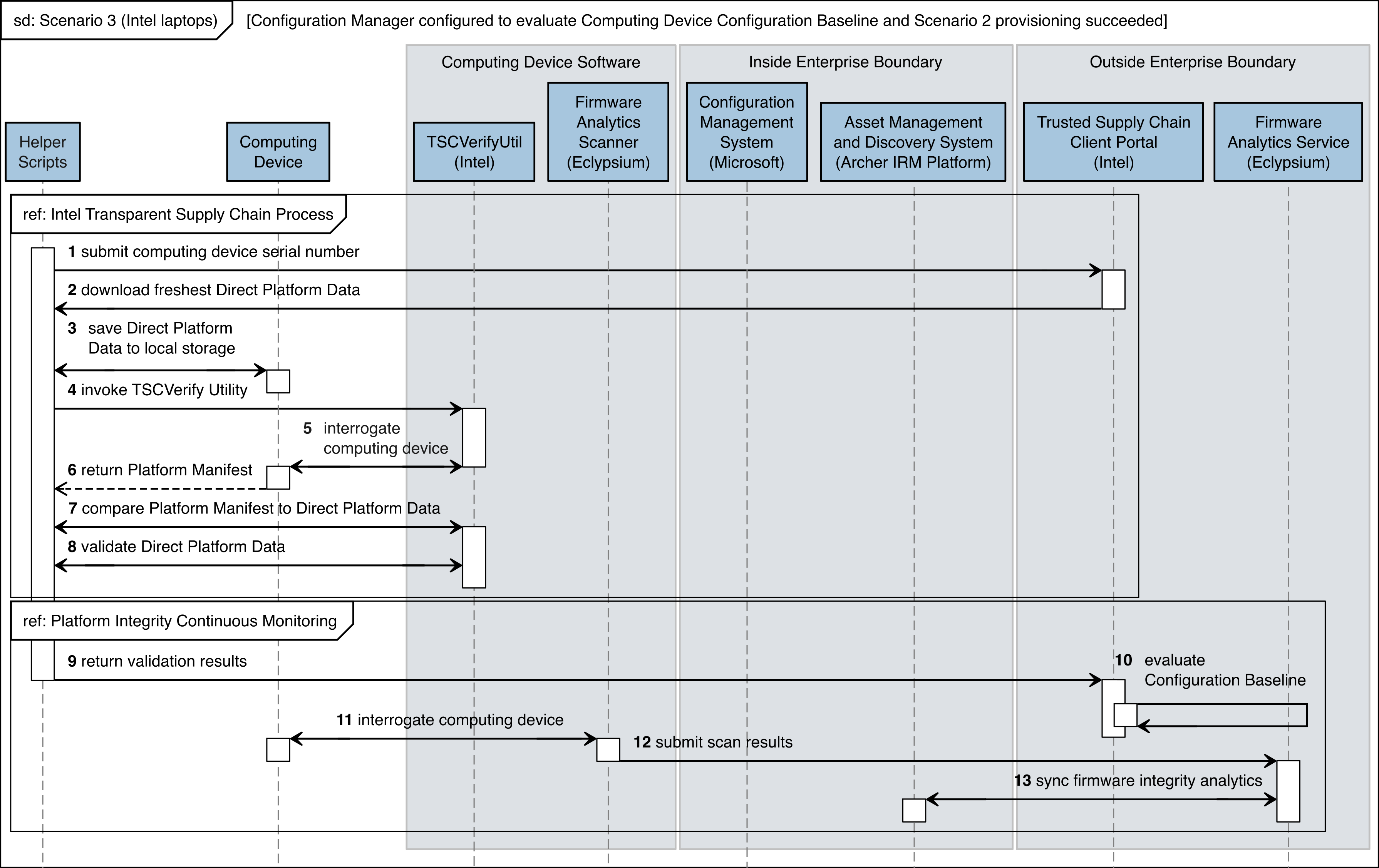
Figure C‑10 Dell Laptops Scenario 3

Figure C‑11 HP Inc. Laptops Scenario 3