NIST SPECIAL PUBLICATION 1800-22 Supplement
Mobile Device Security:
Bring Your Own Device (BYOD)
Supplement
Example Scenario: Putting Guidance Into Practice
Kaitlin Boeckl
Nakia Grayson
Gema Howell
Naomi Lefkovitz
Applied Cybersecurity Division
Information Technology Laboratory
Jason Ajmo
R. Eugene Craft
Milissa McGinnis*
Kenneth Sandlin
Oksana Slivina
Julie Snyder
Paul Ward
The MITRE Corporation
McLean, VA
*Former employee; all work for this publication done while at employer
September 2023
FINAL
This publication is available free of charge from https://doi.org/10.6028/NIST.SP.1800-22

DISCLAIMER
Certain commercial entities, equipment, products, or materials may be identified by name or company logo or other insignia in order to acknowledge their participation in this collaboration or to describe an experimental procedure or concept adequately. Such identification is not intended to imply special status or relationship with NIST or recommendation or endorsement by NIST or NCCoE; neither is it intended to imply that the entities, equipment, products, or materials are necessarily the best available for the purpose.
National Institute of Standards and Technology Special Publication 1800-22 Supplement Natl. Inst. Stand. Technol. Spec. Publ. 1800-22 Supplement, 61 pages, (September 2023), CODEN: NSPUE2
FEEDBACK
As a private-public partnership, we are always seeking feedback on our practice guides. We are particularly interested in seeing how businesses apply NCCoE reference designs in the real world. If you have implemented the reference design, or have questions about applying it in your environment, please email us at mobile-nccoe@nist.gov.
All comments are subject to release under the Freedom of Information Act.
NATIONAL CYBERSECURITY CENTER OF EXCELLENCE
The National Cybersecurity Center of Excellence (NCCoE), a part of the National Institute of Standards and Technology (NIST), is a collaborative hub where industry organizations, government agencies, and academic institutions work together to address businesses’ most pressing cybersecurity issues. This public-private partnership enables the creation of practical cybersecurity solutions for specific industries, as well as for broad, cross-sector technology challenges. Through consortia under Cooperative Research and Development Agreements (CRADAs), including technology partners—from Fortune 50 market leaders to smaller companies specializing in information technology security—the NCCoE applies standards and best practices to develop modular, easily adaptable example cybersecurity solutions using commercially available technology. The NCCoE documents these example solutions in the NIST Special Publication 1800 series, which maps capabilities to the NIST Cyber Security Framework and details the steps needed for another entity to recreate the example solution. The NCCoE was established in 2012 by NIST in partnership with the State of Maryland and Montgomery County, Maryland.
NIST CYBERSECURITY PRACTICE GUIDES
NIST Cybersecurity Practice Guides (Special Publication Series 1800) target specific cybersecurity challenges in the public and private sectors. They are practical, user-friendly guides that facilitate the adoption of standards-based approaches to cybersecurity. They show members of the information security community how to implement example solutions that help them align with relevant standards and best practices, and provide users with the materials lists, configuration files, and other information they need to implement a similar approach.
The documents in this series describe example implementations of cybersecurity practices that businesses and other organizations may voluntarily adopt. These documents do not describe regulations or mandatory practices, nor do they carry statutory authority.
This Practice Guide demonstrates a standards-based reference design and provides users with the information they need to replicate enhancing the security of bring your own device (BYOD) solutions. This reference design is modular and can be deployed in whole or in part.
This guide contains four volumes:
NIST SP 1800-22A: Executive Summary
NIST SP 1800-22B: Approach, Architecture, and Security Characteristics – what we built and why
NIST SP 1800-22 Supplement: Example Scenario: Putting Guidance into Practice – how organizations can implement this example solution’s guidance
NIST SP 1800-22C: How-To Guides – instructions for building the example solution
ABSTRACT
Bring Your Own Device (BYOD) refers to the practice of performing work-related activities on personally owned devices. This practice guide provides an example solution demonstrating how to enhance security and privacy in Android and Apple phones and tablets used in BYOD deployments.
Incorporating BYOD deployments into an organization can increase the opportunities and methods available to access organizational resources. For some organizations, the combination of traditional in-office processes with mobile device technologies enables portable communication approaches and adaptive workflows. For others, it fosters a mobile-first approach in which their employees communicate and collaborate primarily using their mobile devices.
However, some of the features that make BYOD mobile devices increasingly flexible and functional also present unique security and privacy challenges to both organizations and device owners. The unique nature of these challenges is driven by the differing risks posed by the type, age, operating system (OS), and other variances in mobile devices.
Enabling BYOD capabilities in the enterprise introduces new cybersecurity risks. Solutions that are designed to secure corporate devices and on-premises data do not provide an effective cybersecurity solution for BYOD. Finding an effective solution can be challenging due to the unique risks that BYOD deployments impose. Additionally, enabling BYOD capabilities introduces new privacy risks to employees by providing their employer a degree of access to their personal devices, opening up the possibility of observation and control that would not otherwise exist.
To help organizations benefit from BYOD’s flexibility while protecting themselves from critical security and privacy challenges, this practice guide provides an example solution using standards-based, commercially available products and step-by-step implementation guidance.
KEYWORDS
Bring your own device; BYOD; mobile device management; mobile device security.
ACKNOWLEDGMENTS
We are grateful to the following individuals for their generous contributions of expertise and time.
Name |
Organization |
|---|---|
Donna Dodson* |
NIST |
Joshua M. Franklin* |
NIST |
Dylan Gilbert |
NIST |
Jeff Greene* |
NIST |
Natalia Martin |
NIST |
William Newhouse |
NIST |
Cherilyn Pascoe |
NIST |
Murugiah Souppaya |
NIST |
Kevin Stine |
NIST |
Chris Brown |
The MITRE Corporation |
Nancy Correll* |
The MITRE Corporation |
Spike E. Dog |
The MITRE Corporation |
Sallie Edwards |
The MITRE Corporation |
Parisa Grayeli |
The MITRE Corporation |
Marisa Harriston* |
The MITRE Corporation |
Brian Johnson* |
The MITRE Corporation |
Karri Meldorf |
The MITRE Corporation |
Steven Sharma* |
The MITRE Corporation |
Jessica Walton |
The MITRE Corporation |
Erin Wheeler* |
The MITRE Corporation |
Dr. Behnam Shariati |
University of Maryland, Baltimore County |
Jeffrey Ward* |
IBM |
Cesare Coscia* |
IBM |
Chris Gogoel |
Kryptowire (now known as Quokka) |
Tom Karygiannis* |
Kryptowire (now known as Quokka) |
Jeff Lamoureaux |
Palo Alto Networks |
Sean Morgan |
Palo Alto Networks |
Kabir Kasargod |
Qualcomm |
Viji Raveendran |
Qualcomm |
Mikel Draghici* |
Zimperium |
*Former employee; all work for this publication done while at employer.
The Technology Partners/Collaborators who participated in this build submitted their capabilities in response to a notice in the Federal Register. Respondents with relevant capabilities or product components were invited to sign a Cooperative Research and Development Agreement (CRADA) with NIST, allowing them to participate in a consortium to build this example solution. We worked with:
Technology Partner/Collaborator |
Build Involvement |
|---|---|
IBM |
Mobile Device Management |
Kryptowire (now known as Quokka) |
Application Vetting |
Palo Alto Networks |
Firewall; Virtual Private Network |
Qualcomm |
Trusted Execution Environment |
Zimperium |
Mobile Threat Defense |
DOCUMENT CONVENTIONS
The terms “shall” and “shall not” indicate requirements to be followed strictly to conform to the publication and from which no deviation is permitted. The terms “should” and “should not” indicate that among several possibilities, one is recommended as particularly suitable without mentioning or excluding others, or that a certain course of action is preferred but not necessarily required, or that (in the negative form) a certain possibility or course of action is discouraged but not prohibited. The terms “may” and “need not” indicate a course of action permissible within the limits of the publication. The terms “can” and “cannot” indicate a possibility and capability, whether material, physical, or causal.
PATENT DISCLOSURE NOTICE
NOTICE: The Information Technology Laboratory (ITL) has requested that holders of patent claims whose use may be required for compliance with the guidance or requirements of this publication disclose such patent claims to ITL. However, holders of patents are not obligated to respond to ITL calls for patents and ITL has not undertaken a patent search in order to identify which, if any, patents may apply to this publication.
As of the date of publication and following call(s) for the identification of patent claims whose use may be required for compliance with the guidance or requirements of this publication, no such patent claims have been identified to ITL.
No representation is made or implied by ITL that licenses are not required to avoid patent infringement in the use of this publication.
List of Figures
Figure 2‑1 Great Seneca Accounting’s Work Environments
Figure 2‑2 Example Solution Architecture
Figure 2‑3 Great Seneca Accounting’s Security and Privacy Risk Management Steps
Figure 5‑1 Cybersecurity Framework Subcategory to Informative Reference Mapping
Figure 5‑2 Security and Privacy Objectives
Figure 5‑3 Subcategory DE.CM-5 Mapping to BYOD-Related Business/Mission Objectives
Figure 5‑4 Subcategory PR.AC-5 Mapping to BYOD-Related Business/Mission Objectives
Figure D-1 Great Seneca Accounting’s Work Environments
Figure E‑1 Comparing Framework Processes to Establish or Improve Programs
Figure F‑1 Risk Assessment Process
Figure F‑2 NIST SP 800-30 Generic Risk Model
List of Tables
Table 3‑1 Great Seneca Accounting’s Cybersecurity Framework Target Profile
Table 3‑2 Great Seneca Accounting’s Privacy Target Profile
Table F‑1 Great Seneca Accounting’s BYOD Deployment Threats
Table F‑2 Threat Event Mapping to the Mobile Threat Catalogue
Table F‑3 Identify Vulnerabilities and Predisposing Conditions
Table F‑4 Summary of Risk Assessment Findings
Table G‑1 Privacy References for the Example Solution Technologies
1 Applying This Build: Example Scenario¶
This document provides guidance for leveraging standards and tools to reduce cybersecurity and privacy risks in a Bring Your Own Device (BYOD) implementation. This document uses an example scenario - using a fictional company named Great Seneca Accounting—to outline specific steps an organization could take. The example shows how BYOD objectives can align with a fictional organization’s security and privacy priorities using risk management standards, guidance, and tools.
To demonstrate how an organization may use this National Institute of Standards and Technology (NIST) Special Publication (SP) and other NIST tools to implement a BYOD use case, the National Cybersecurity Center of Excellence created an example scenario that centers around a fictional, small-to-mid-size organization called Great Seneca Accounting. This scenario exemplifies the issues that an organization may face when addressing common enterprise BYOD security challenges.
1.1 Standards and Guidance Used in this Example Scenario¶
In addition to the Executive Summary contained in Volume A, and the architecture description in Volume B, this practice guide also includes a series of how-to instructions in Volume C. The how-to instructions in Volume C provide step-by-step instructions covering the initial setup (installation or provisioning) and configuration for each component of the architecture. These step-by-step instructions can help security engineers rapidly deploy and evaluate the example solution in their test environment.
The example solution uses standards-based, commercially available products that can be used by an organization interested in deploying a BYOD solution. The example solution provides recommendations for enhancing security and privacy infrastructure by integrating on-premises and cloud-hosted mobile security technologies. This practice guide provides an example solution that an organization may use in whole or in part as the basis for creating a custom solution that best supports their unique needs.
The fictional Great Seneca Accounting organization illustrates how this guide may be applied by an organization, starting with a mobile device infrastructure that lacked mobile device security architecture concepts. Great Seneca employed multiple NIST cybersecurity and privacy risk management tools to understand the gaps in its architecture and methods to enhance security of its systems and privacy for its employees.
This example scenario provides useful context for using the following NIST Frameworks and other relevant tools to help mitigate some of the security and privacy challenges that organizations may encounter when deploying BYOD capabilities:
NIST Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1 (Cybersecurity Framework) [S1]
NIST Privacy Framework: A Tool for Improving Privacy Through Enterprise Risk Management, Version 1.0 (Privacy Framework) [S2]
NIST Special Publication (SP) 800-181 National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework [S3]
NIST Risk Management Framework [S4]
NIST Mobile Threat Catalogue [S5]
For additional information, see Volume B’s Appendix D.
2 About Great Seneca Accounting¶
In the example scenario, Great Seneca Accounting is a fictional accounting firm that grew from a single office location into a larger firm with a regional presence. Great Seneca Accounting performs accounting functions related to capturing, communicating, processing, transmitting, and analyzing financial data and accounting services for its customers.
When the firm was first created, most of its employees worked from the Great Seneca Accounting office, with minimal use of mobile devices. They were able to do this without actively embracing mobile device usage because most of the employees worked at their desks at the company’s single location.
Over the years, the Great Seneca Accounting company grew from a local company, where all its employees performed work at their desks by using desktop computers provided by the organization, into a regional firm with employees who work remotely and who support regional customers.
Now, many of the employees spend part of their week traveling and working from customer or other remote locations. This has prompted the organization to specify, the need to support employees to work remotely as a strategic priority, while both traveling and working from a customer location. Consequently, the company wants to embrace BYOD solutions to support its remote work.
Figure 2‑1 shows an overview of the typical work environments for a Great Seneca Accounting employee. Many employees work remotely while using their own mobile phones and tablets to perform both work and personal activities throughout the day.
Figure 2‑1 Great Seneca Accounting’s Work Environments

Great Seneca Accounting’s corporate management initiated a complete review of all policies, procedures, and technology relating to its mobile deployment to ensure that the company is well protected against attacks involving personal mobile devices. This includes mitigating risks against its devices, custom applications, and corporate infrastructure supporting mobile services. Management identified NIST’s Risk Management Framework (RMF) [S4] and Privacy Risk Assessment Methodology (PRAM) [S6] as useful tools for supporting this analysis. The company developed Cybersecurity Framework and Privacy Framework Target Profiles to guide Great Seneca Accounting’s decision-making because the target profiles link Great Seneca Accounting’s mission and business priorities with supporting cybersecurity and privacy activities.
Great Seneca Accounting identified the scope of their mobile solution to be both Android and Apple personally owned mobile phones and tablets. While this example scenario intends to provide an exemplar of organization guidance with a description of BYOD concepts and how to apply those concepts, this example scenario should not suggest a limit on BYOD uses.
Great Seneca Accounting plans to use NIST SP 1800-22 (this practice guide) to inform its updated BYOD architecture as well as NIST’s Mobile Threat Catalogue to identify threats to mobile deployment. These NIST frameworks and tools used are described further in Appendix E.
As shown in Figure 2‑2, this example solution applied multiple mobile device security technologies. These included a cloud-based Enterprise Mobility Management solution integrated with cloud- and agent-based mobile security technologies to help deploy a set of security and privacy capabilities that support the example solution.
Figure 2‑2 Example Solution Architecture

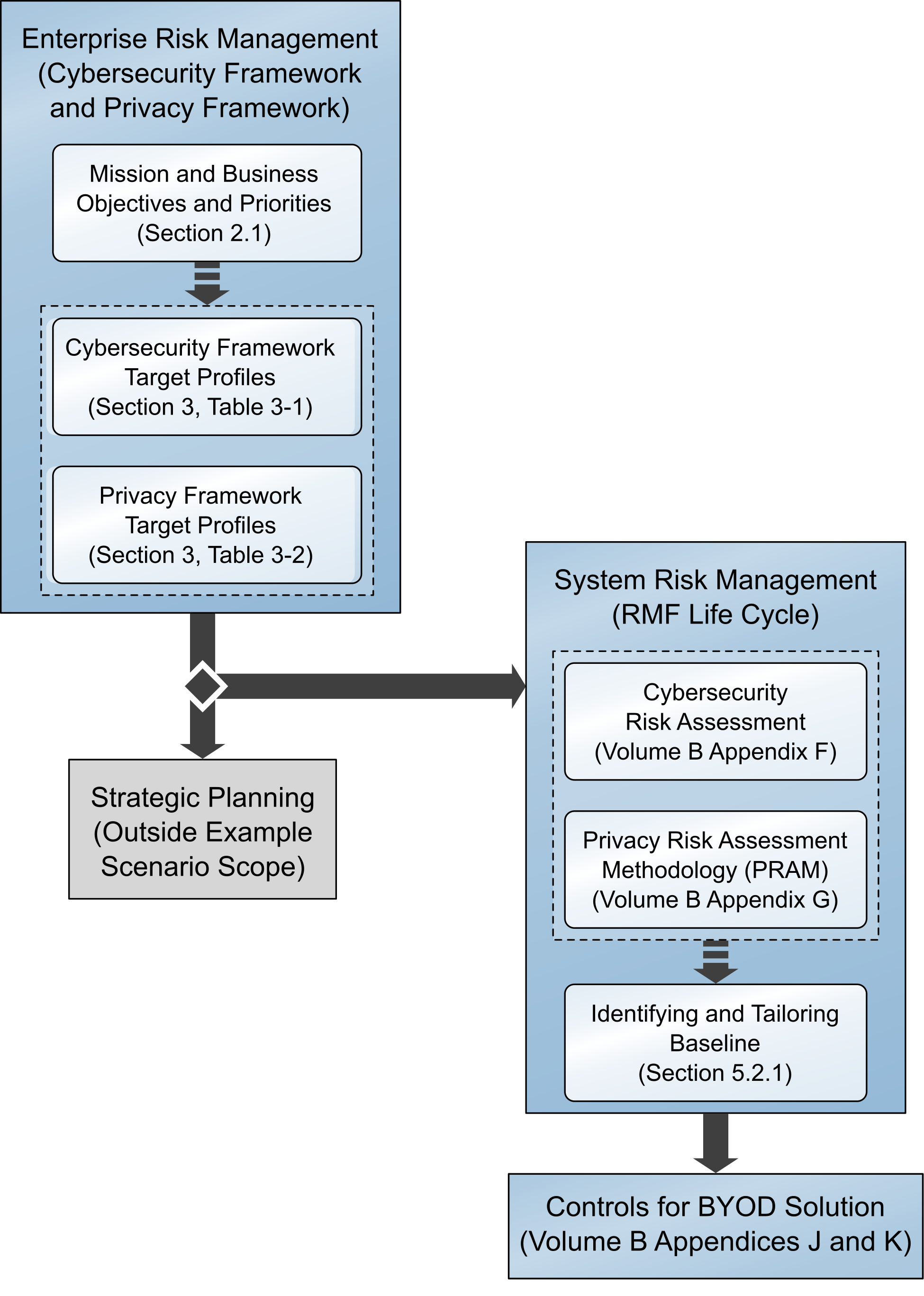
Figure 2‑3 shows the overall process that Great Seneca Accounting plans to follow. It highlights key activities from various NIST guidance documents related to security and privacy risk management, each of which is discussed in the sections identified in Figure 2‑3. Please note that this process is an abbreviated version of steps provided in NIST SP 800-37 Revision 2 [S7], which shows how some available resources may be used by any organization.
Figure 2‑3 Great Seneca Accounting’s Security and Privacy Risk Management Steps
2.1 Great Seneca Accounting’s Business/Mission Objectives¶
Great Seneca Accounting developed a mission statement and a set of supporting business/mission objectives to ensure that its activities align with its core purpose. The company has had the same mission since it was founded:
While Great Seneca Accounting has a number of business/mission objectives, those below relate to its interest in BYOD, listed in priority order:
Mission Objective 1—Provide good data stewardship
Mission Objective 2—Enable timely communication with clients
Mission Objective 3—Provide innovative financial services
Mission Objective 4—Enable workforce flexibility
3 Great Seneca Accounting’s Target Profiles¶
Great Seneca Accounting used the NIST Cybersecurity Framework and NIST Privacy Framework as key strategic planning tools to improve its security and privacy programs. It followed the processes outlined in the frameworks, and as part of that effort, created two target profiles—one for cybersecurity and one for privacy.
These Target Profiles describe the desired or aspirational state of Great Seneca Accounting by identifying and prioritizing the cybersecurity and privacy activities and outcomes needed to support its enterprise business/mission objectives. The Subcategories in each Framework Core articulate those cybersecurity and privacy activities and outcomes.
Note: See Appendix E for a high-level description of the Cybersecurity Framework and Privacy Framework.
To understand what Subcategories to prioritize implementing in each framework, Great Seneca Accounting considered the importance of the Subcategories for accomplishing each business/mission objective. The Target Profiles reflect that discussion by designating prioritized Subcategories as low, moderate, or high.
Subcategory improvements important for BYOD deployment also became part of its Target Profiles because Great Seneca Accounting was upgrading its existing information technology infrastructure as part of its BYOD implementation.
The Cybersecurity Framework Target Profile in Table 3-1 and the Privacy Framework Target Profile in Table 3-2 are included as examples of Great Seneca Accounting’s identification of the business/mission objectives that are relevant to their BYOD deployment.
Great Seneca Accounting chose to address the Subcategories that are prioritized as moderate and high for multiple business/mission objectives in its Target Profiles for this year’s BYOD deployment with plans to address the low Subcategories in the future.
Table 3-1 and Table 3-2 include only those Subcategories that are prioritized as moderate or high for the business/mission objectives. Any subcategory designated as low is included in Table 3‑1 and Table 3‑2 only because it is high or moderate for another business/mission objective.
Great Seneca Accounting used the Target Profiles to help guide risk management decisions throughout the organization’s activities, including making decisions regarding budget allocation, technology design, and staffing for its programs and technology deployments. Discussions for developing and using the Target Profiles include stakeholders in various parts of the organization, such as business/mission program owners, data stewards, cybersecurity practitioners, privacy practitioners, legal and compliance experts, and technology experts.
Note: Low, moderate, and high designations indicate the level of relative importance among Subcategories for Great Seneca to accomplish a business/mission objective.
Table 3‑1 Great Seneca Accounting’s Cybersecurity Framework Target Profile
Function |
Category |
Subcategory |
Mission Objective 1 |
Mission Objective 2 |
Mission Objective 3 |
Mission Objective 4 |
|---|---|---|---|---|---|---|
IDENTIFY |
Asset Management |
ID.AM-1: Physical devices and systems within the organization are inventoried. |
moderate |
moderate |
moderate |
low |
ID.AM-2: Software platforms and applications within the organization are inventoried. |
moderate |
moderate |
moderate |
low |
||
Risk Assessment |
ID.RA-1: Asset vulnerabilities are identified and documented. |
moderate |
moderate |
moderate |
moderate |
|
ID.RA-3: Threats, both internal and external, are identified and documented. |
moderate |
moderate |
moderate |
moderate |
||
PROTECT |
Identity Management and Access Control |
PR.AC-1: Identities and credentials are issued, managed, verified, revoked, and audited for authorized devices, users, and processes. |
moderate |
high |
moderate |
high |
PR.AC-3: Remote access is managed. |
moderate |
high |
high |
high |
||
PR.AC-5: Network integrity is protected (e.g., network segregation, network segmentation). |
high |
high |
high |
high |
||
PR.AC-6: Identities are proofed and bound to credentials and asserted in interactions. |
moderate |
high |
high |
high |
||
Data Security |
PR.DS-1: Data-at-rest is protected. |
high |
moderate |
moderate |
high |
|
PR.DS-2: Data-in-transit is protected. |
moderate |
high |
moderate |
high |
||
PR.DS-6: Integrity-checking mechanisms are used to verify software, firmware, and information integrity. |
high |
moderate |
moderate |
high |
||
PR.DS-8: Integrity checking mechanisms are used to verify hardware integrity. |
moderate |
moderate |
moderate |
low |
||
Information Protection Processes and Procedures |
PR.IP-1: A baseline configuration of information technology/industrial control systems is created and maintained incorporating security principles. |
moderate |
moderate |
moderate |
low |
|
Protective Technology |
PR.PT-4: Communications and control networks are protected. |
low |
moderate |
moderate |
low |
|
DETECT |
Anomalies and Events |
DE.AE-5: Incident alert thresholds are established. |
high |
high |
high |
high |
Security Continuous Monitoring |
DE.CM-4: Malicious code is detected. |
high |
high |
high |
high |
|
DE.CM-5: Unauthorized mobile code is detected. |
moderate |
moderate |
moderate |
low |
||
DE.CM-8: Vulnerability scans are performed. |
high |
high |
high |
high |
Table 3‑2 Great Seneca Accounting’s Privacy Target Profile
Function |
Category |
Subcategory |
Mission Objective 1 |
Mission Objective 2 |
Mission Objective 3 |
Mission Objective 4 |
|---|---|---|---|---|---|---|
IDENTIFY-P |
Inventory and Mapping |
ID.IM-P7: The data processing environment is identified (e.g., geographic location, internal, cloud, third parties). |
high |
high |
high |
high |
GOVERN-P |
Governance Policies, Processes, and Procedures |
GV.PO-P1: Organizational privacy values and policies (e.g., conditions on data processing, individuals’ prerogatives with respect to data processing) are established and communicated. |
high |
high |
high |
high |
GV.PO-P5: Legal, regulatory, and contractual requirements regarding privacy are understood and managed. |
high |
high |
high |
high |
||
Monitoring and Review |
GV.MT-P3: Policies, processes, and procedures for assessing compliance with legal requirements and privacy policies are established and in place. |
high |
high |
high |
high |
|
GV.MT-P5: Policies, processes, and procedures are established and in place to receive, analyze, and respond to problematic data actions disclosed to the organization from internal and external sources (e.g., internal discovery, privacy researchers, professional events). |
high |
high |
high |
high |
||
CONTROL-P |
Data Management |
CT.DM-P1: Data elements can be accessed for review. |
high |
moderate |
high |
moderate |
CT.DM-P3: Data elements can be accessed for alteration. |
high |
moderate |
high |
moderate |
||
CT.DM-P4: Data elements can be accessed for deletion. |
high |
moderate |
high |
moderate |
||
CT.DM-P5: Data are destroyed according to policy. |
high |
moderate |
high |
moderate |
||
Disassociated Processing |
CT.DP-P4: System or device configurations permit selective collection or disclosure of data elements. |
high |
high |
high |
high |
|
COMMUNICATE-P |
Data Processing Awareness |
CM.AW-P5: Data corrections or deletions can be communicated to individuals or organizations (e.g., data sources) in the data processing ecosystem. |
high |
moderate |
moderate |
moderate |
PROTECT-P |
Data Protection Policies, Processes, and Procedures |
PR.PO-P3: Backups of information are conducted, maintained, and tested. |
high |
moderate |
high |
moderate |
PR.AC-P1: Identities and credentials are issued, managed, verified, revoked, and audited for authorized individuals, processes, and devices. |
moderate |
high |
moderate |
high |
||
Identity Management, Authentication, and Access Control |
PR.AC-P2: Physical access to data and devices is managed. |
high |
moderate |
high |
moderate |
|
PR.AC-P4: Access permissions and authorizations are managed, incorporating the principles of least privilege and separation of duties. |
high |
moderate |
high |
moderate |
||
PR.AC-P5: Network integrity is protected (e.g., network segregation, network segmentation). |
high |
high |
high |
high |
||
PR.DS-P1: Data-at-rest is protected. |
high |
moderate |
moderate |
high |
||
Data Security |
PR.DS-P2: Data-in-transit is protected. |
moderate |
high |
moderate |
high |
|
PR.DS-P5: Protections against data leaks are implemented. |
high |
moderate |
high |
moderate |
||
PR.DS-P6: Integrity checking mechanisms are used to verify software, firmware, and information integrity. |
high |
moderate |
moderate |
high |
||
PR.PT-P3: Communications and control networks are protected. |
moderate |
high |
moderate |
high |
4 Great Seneca Accounting Embraces BYOD¶
Great Seneca Accounting now allows its staff to use their personal mobile devices to perform their daily work duties on an as-needed basis. Accountants use the devices for various tasks including communicating with client organizations and other employees, collecting confidential client information, analyzing financial transactions, generating reports, accessing tax and payroll information, and creating and reviewing comprehensive financial statements.
Great Seneca accountants work from many locations including their corporate office building, their homes, their customers’ offices, and other locations. In order to be able to work in all these locations, they require the use of mobile devices to perform their job functions.
Great Seneca Accounting’s current mobile infrastructure enables accountants to perform their job duties by using their personally owned devices, despite minimal security installed and enforced on these devices. Examples of security concerns with the use of personally owned devices are:
Employees can connect to any Wi-Fi network to perform work-related activities when they are working on the road, including at a client’s site.
Custom mobile applications being sideloaded onto devices that employees use.
The personally owned devices allow users to install applications on an as-needed basis without separation of enterprise and personal data.
While not affecting Great Seneca Accounting, a string of well-publicized cybersecurity attacks was recently reported in the news, and this prompted Great Seneca to review its mobile device security and privacy deployment strategy. When making BYOD deployment decisions, Great Seneca Accounting plans to prioritize implementing cybersecurity and privacy capabilities that would enable it to accomplish its business/mission objectives (i.e., its reasons for deploying BYOD capabilities).
To do this, Great Seneca Accounting conducted a technical assessment of its current BYOD architecture to help it understand ways to improve the confidentiality, integrity, availability, and privacy of data and devices associated with its BYOD deployment. The company identified several vulnerabilities based on its current mobile device deployment. Figure 4-1 below presents a subset of those vulnerabilities.
Figure 4‑1 Great Seneca Accounting’s Current Mobile Deployment Architecture (Before Security and Privacy Enhancements)

Figure 4‑1 highlights the following vulnerabilities with a red exclamation mark:
BYOD deployments can place organizational and personal data, as well as employees’ privacy, at risk. Organizational and personal data can become commingled if either the same application is used in both contexts or if multiple applications access shared device resources (e.g., contacts or calendar) as applications for both personal and work usage are installed. This also puts employees’ privacy at risk, as the organization can have visibility into their personal life outside work.
BYOD deployments can leverage nonsecure networks. As employees use nonsecure Wi-Fi hotspots, mobile devices that are connecting to Great Seneca Accounting from those unencrypted networks place data transmitted prior to a secure connection at risk of discovery and eavesdropping, including passwords.
As employees install applications on their personally owned devices, the applications can have unidentified vulnerabilities or weaknesses that increase the risk of device compromise (e.g., applications that access contacts may now have access to the organization’s client contact information). Further, legitimate, privacy-intrusive applications can legally collect data through terms and conditions and requested permissions.
On personally owned devices without restriction policies in place, employees may inadvertently download applications outside official application stores, which are malware in disguise.
Because personally owned mobile devices can connect from unknown locations, firewall rules must allow inbound connections from unrecognized, potentially malicious Internet Protocol addresses.
In addition to identifying the technical assets and the vulnerabilities, Great Seneca Accounting identified the scope of the mobile solution (i.e., both Android and Apple personally owned mobile phones and tablets) and the regulatory requirements or guidance that will apply to their deployment and solution (e.g., encryption will be Federal Information Processing Standards [FIPS]-validated to protect sensitive accounting information).
5 Applying NIST Risk Management Methodologies to Great Seneca Accounting’s BYOD Architecture¶
Section 2 and Section 3 above describe Great Seneca Accounting, their business mission, and what security and privacy areas they consider most important. Great Seneca created Target Profiles that mapped their BYOD-related mission/business objectives and priorities with the Functions, Categories, and Subcategories of both the Cybersecurity Framework and the Privacy Framework. Those Cybersecurity Framework and Privacy Framework Target Profiles are provided in Table 3-1 and Table 3-2 in Section 3 of this document.
Now, the Target Profiles provided in Section 3 will demonstrate the role they play in identifying and prioritizing the implementation of the security and privacy controls, as well as the capabilities that Great Seneca would like to include in its new BYOD security and privacy-enhanced architecture.
5.1 Using Great Seneca Accounting’s Target Profiles¶
The Cybersecurity Framework maps its Subcategories to Informative References. The Informative References contained in the Framework Core provide examples of methods that Great Seneca can use to achieve its desired outcomes. The Cybersecurity Framework’s Subcategory and Informative References mappings include NIST SP 800-53 controls.
An illustrative segment of the Cybersecurity Framework’s Framework Core is shown in Figure 5-1. Highlighted in the green box is an example of how the Cybersecurity Framework provides a mapping of Subcategories to Informative References.
Figure 5‑1 Cybersecurity Framework Subcategory to Informative Reference Mapping
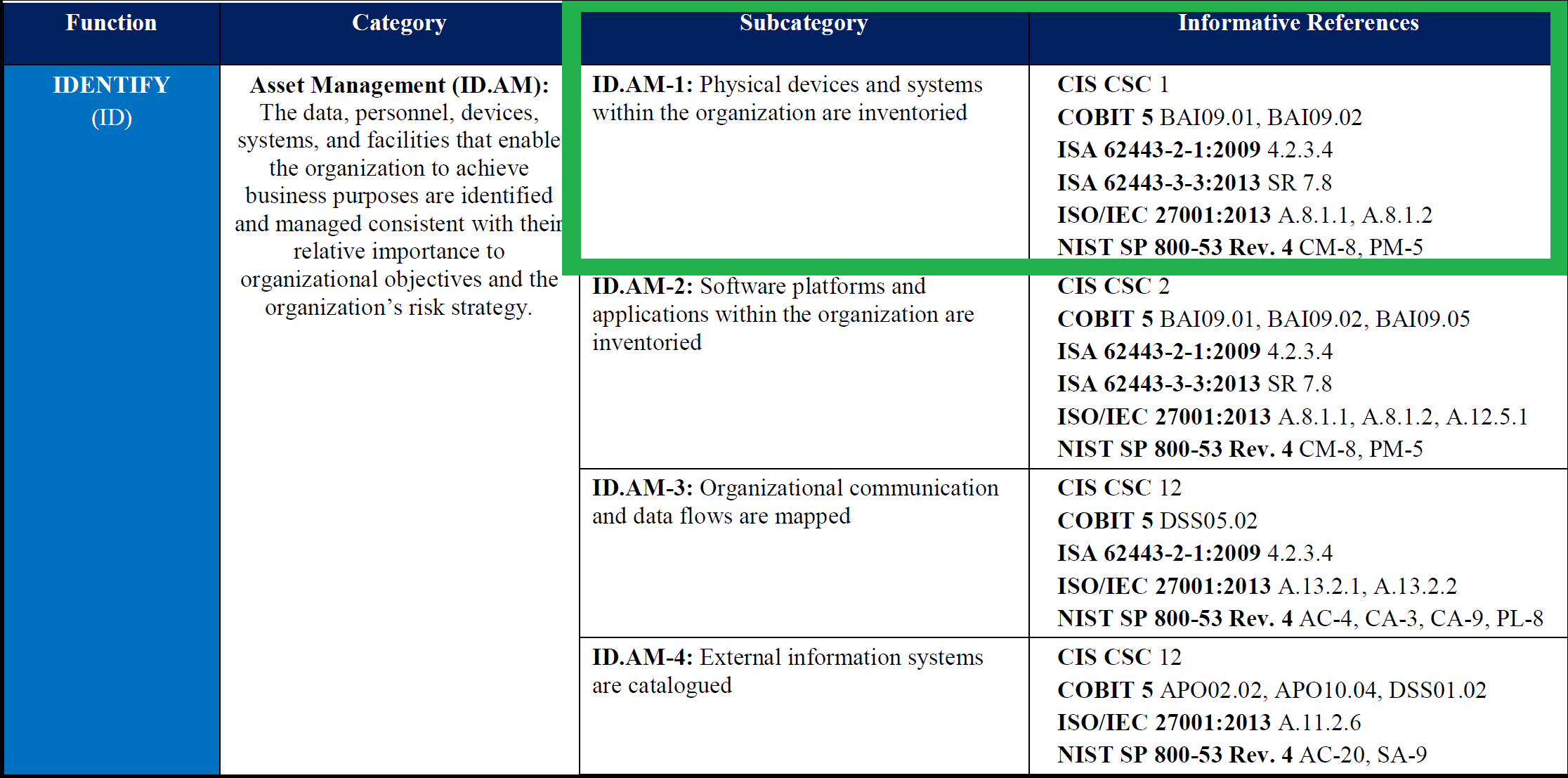
To provide a starting point for Great Seneca’s mapping of their Cybersecurity Framework and Privacy Framework Target Profiles to the NIST SP 800-53 security and privacy controls and capabilities, Great Seneca leveraged the mapping provided in the Cybersecurity Framework. An example of the Cybersecurity Framework’s mapping is provided in Figure 5‑1.
See Volume B’s Appendices E and F for additional information on the security and privacy outcomes that this document’s example solution supports. Appendices E and F provide a mapping of this document’s example solution capabilities with the related Subcategories in the Cybersecurity Framework and Privacy Framework.
Volume B’s Appendix E provides the Cybersecurity Framework Subcategory mappings, and Volume B’s Appendix F provides the Privacy Framework Subcategory mappings.
5.2 Great Seneca Uses the Target Profiles to Help Prioritize Security and Privacy Control Deployment¶
Due to budget constraints, Great Seneca Accounting will focus on implementing the higher priority security and privacy controls that were identified in the organization’s two Target Profiles first. The company will then focus on implementing lower priority controls when more funding becomes available. This is accomplished by Great Seneca Accounting comparing the prioritized Subcategories contained in Section 3’s Table 3-1 and Table 3-2 with the outcomes that the example solution supports.
By comparing its Cybersecurity Framework Target Profile (Table 3-1) with the Subcategories supported by the example solution that are shown in Volume B’s Appendix E, Great Seneca Accounting determines that the example solution will help it achieve its desired Cybersecurity Framework Target Profile outcomes.
Great Seneca performs a similar comparison of the Privacy Framework Target Profile in Table 3-2 with the Subcategories supported by the example solution that are shown in Volume B’s Appendix F. From that comparison of the example solution’s capabilities and Great Seneca’s privacy-related objectives, Great Seneca determines that the example solution provided in this practice guide will help it to achieve the privacy-related outcomes that were identified in Table 3‑2’s Privacy Framework Target Profile.
5.2.1 Identifying and Tailoring the Baseline Controls¶
Now that Great Seneca Accounting understands how the Target Profiles will help prioritize the implementation of the high-level security and privacy objectives shown in Figure 5‑2, they would like to look more closely at the NIST SP 800-53 controls it will initially implement in its new BYOD architecture. This will help Great Seneca identify the capabilities it will deploy first to meet its architecture needs.
Figure 5‑2 Security and Privacy Objectives

Volume B’s Appendices E and F provide a list of the controls that the example solution implements, including how the controls in the example solution align to the Subcategories in both the Cybersecurity Framework and Privacy Framework. Because these controls only focus on the example solution, Great Seneca will need to implement additional controls that address the unique risks associated with its environment.
To help identify the specific controls Great Seneca Accounting will be implementing to support the new BYOD architecture, it uses the NIST RMF process to manage security and privacy risk for its systems. The organization decides to follow the RMF guidance in NIST SP 800-37 [S7] to conduct security and privacy risk assessments as it continues preparing to design its new solution.
5.3 Great Seneca Accounting Performs a Risk Assessment¶
Great Seneca Accounting completes a security risk assessment by using the guidance in NIST SP 800-30 [S8] and the Mobile Threat Catalogue [S5] to identify cybersecurity threats to the organization. The company then uses the NIST PRAM [S6] to perform a privacy risk assessment. Appendix F and Appendix G in this document describe these risk assessments in more detail. These risk assessments produce two significant conclusions:
Great Seneca Accounting finds similar cybersecurity threats in its environment and problematic data actions for employee privacy as those discussed in NIST SP 1800-22, validating that the controls discussed in the example solution are relevant to their environment.
The organization determines that it has a high-impact system, based on the impact guidance in NIST FIPS 200, Minimum Security Requirements for Federal Information and Information Systems [S9], and needs to implement more controls beyond those identified in NIST SP 1800-22 and its Target Profiles to support the additional system components in its own solution (e.g., underlying OS, the data center where the equipment will reside).
5.4 Great Seneca Accounting Tailors Their Security and Privacy Control Baselines¶
As part of their review of NIST FIPS 200 [S9], Great Seneca Accounting selects the high controls baseline in NIST SP 800-53 [S10] for their BYOD architecture implementation. They then tailor the control baselines based on the needs identified through the priority Subcategories in its cybersecurity and privacy Target Profiles.
Control baselines are tailored to meet their organization’s needs. NIST SP 800-53 [S10] defines tailoring as “The process by which security control baselines are modified by: (i) identifying and designating common controls; (ii) applying scoping considerations on the applicability and implementation of baseline controls; (iii) selecting compensating security controls; (iv) assigning specific values to organization-defined security control parameters; (v) supplementing baselines with additional security controls or control enhancements; and (vi) providing additional specification information for control implementation.”
While not discussed in this example scenario, Great Seneca also plans to make tailoring decisions based on other unique needs in its environment (e.g., legal, and regulatory requirements).
5.4.1 An Example Tailoring of the System and Communications Protection Security Control Family¶
As Great Seneca Accounting reviews the System and Communications Protection (SC) control family in NIST SP 800-53 [S10], it notes there are opportunities for tailoring.
For example, the NIST SP 800-53 baseline includes control enhancements, whereas the Cybersecurity Framework Informative References contain only base controls. Great Seneca Accounting decides to implement the enhancements that are applicable to a high-impact system for the SC controls they have selected.
Using this decision as a guide, Great Seneca Accounting also makes the following tailoring decisions related to the NIST SP 800-53 SC control family:
NIST SP 800-53 provides recommendations regarding implementation priorities for controls. The implementation priorities of controls related to some Cybersecurity Framework Subcategories were adjusted to be higher or lower based on their alignment with Subcategory prioritization in the Target Profile.
For example, the implementation priority for Cybersecurity Framework Subcategory DE.CM-5 was identified as having low or moderate importance for accomplishing all four BYOD-related Business/Mission Objectives. NIST SP 800-53 designates control SC-18, which supports the implementation of Cybersecurity Framework Subcategory DE.CM-5, as high priority. However, since Cybersecurity Framework Subcategory DE.CM-5 is moderate or low priority in this context, Great Seneca makes a tailoring decision to lower the implementation priority for the SC-18 NIST SP 800-53 control to moderate.
DE.CM-5’s importance designations for accomplishing the BYOD-Related Business/Mission Objectives are highlighted using a green box in Figure 5‑3.
Figure 5‑3 Subcategory DE.CM-5 Mapping to BYOD-Related Business/Mission Objectives

Conversely, just as the implementation priority for the NIST SP 800-53 control that supports implementation of Subcategory DC.CM-5 was lowered based on the Target Profile, the implementation priority for the NIST SP 800-53 controls that support implementation of Cybersecurity Framework Subcategory PR.AC-5 was raised. This is because Subcategory PR.AC-5 was identified as having high importance for accomplishing all four BYOD-Related Business/Mission Objectives.
The NIST SP 800-53 SC Family security control related to the Cybersecurity Framework Subcategory PR.AC-5 is SC-7. NIST SP 800-53 prioritizes control SC-7 as low. Since control SC-7 supports the implementation of a Cybersecurity Framework Subcategory that is designated as high priority in Great Seneca’s Target Profile (Cybersecurity Framework Subcategory PR.AC-5), Great Seneca makes a tailoring decision to increase the priority of NIST SP 800-53 control SC-7 to high.
- PR.AC-5’s high importance designation for accomplishing the BYOD-Related Business/Mission Objectives is highlighted using a green box in Figure 5‑4. All Subcategory prioritizations (including PR.AC-5’s shown below) can be found in
Figure 5‑4 Subcategory PR.AC-5 Mapping to BYOD-Related Business/Mission Objectives

Great Seneca Accounting follows the same approach for the privacy controls in NIST SP 800-53, using the Privacy Framework Target Profile and controls identified through its PRAM analysis (for more information reference Appendix G).
Great Seneca Accounting will evaluate the security controls as they come up for review under its continuous monitoring program to determine whether there are enhancements to the implemented security controls that can be made over time.
In addition to identifying controls to select, the priorities articulated in Target Profiles will also help Great Seneca Accounting decide how to align financial resources for control implementations (e.g., buying a tool to automate a control as opposed to relying on policy and procedures alone). The Target Profiles will help Great Seneca identify how robustly to reassess the efficacy of implemented controls before new system components or capabilities are enabled in a production environment. Great Seneca will also be able to use the Target Profiles to help evaluate the residual risks of the architecture in the context of Great Seneca Accounting’s business/mission objectives, and the frequency and depth of continued monitoring requirements over time.
Note: All the tailoring decisions discussed above are for example purposes only. An organization’s actual tailoring decision will be based upon their own unique business/mission objectives, risk assessment results, and organizational needs that may significantly vary from these examples.