Appendix A List of Acronyms¶
AD |
Active Directory |
ADCS |
Active Directory Certificate Services |
ADDS |
Active Directory Domain Services |
API |
Application Programming Interface |
ATARC |
Advanced Technology Academic Research Center |
ATT&CK |
Adversarial Tactics, Techniques, and Common Knowledge |
BYOD |
Bring Your Own Device |
CIO |
Chief Information Officer |
CIS |
Center for Internet Security |
COMSEC |
Communications Security |
COPE |
Corporate-Owned Personally-Enabled |
CSP |
Credential Service Provider |
CVE |
Common Vulnerabilities and Exposures |
DHS |
Department of Homeland Security |
DMZ |
Demilitarized Zone |
EMM |
Enterprise Mobility Management |
FedRAMP |
Federal Risk and Authorization Management Program |
FIPS |
Federal Information Processing Standards |
GPS |
Global Positioning System |
HTTP |
Hypertext Transfer Protocol |
HTTPS |
Hypertext Transfer Protocol Secure |
IEC |
International Electrotechnical Commission |
IEEE |
Institute of Electrical and Electronics Engineers |
IMEI |
International Mobile Equipment Identity |
IP |
Internet Protocol |
IR |
Interagency Report |
ISO |
International Organization for Standardization |
IT |
Information Technology |
MDM |
Mobile Device Management |
MSCT |
Mobile Services Category Team |
MTC |
Mobile Threat Catalogue |
MTD |
Mobile Threat Defense |
MTI |
Mobile Threat Intelligence |
MTP |
Mobile Threat Protection |
NCCoE |
National Cybersecurity Center of Excellence |
NIAP |
National Information Assurance Partnership |
NICE |
National Initiative for Cybersecurity Education |
NIST |
National Institute of Standards and Technology |
NVD |
National Vulnerability Database |
OS |
Operating System |
PA |
Palo Alto Networks |
PII |
Personally Identifiable Information |
PRAM |
Privacy Risk Assessment Methodology |
RMF |
Risk Management Framework |
ROM |
Read-only Memory |
SCEP |
Simple Certificate Enrollment Protocol |
SIEM |
Security Information and Event Management |
SMS |
Short Message Service |
SP |
Special Publication |
TE |
Threat Event |
TEE |
Trusted Execution Environment |
TLS |
Transport Layer Security |
UPN |
User Principal Name |
URL |
Uniform Resource Locator |
VPN |
Virtual Private Network |
Appendix B Glossary¶
Access Management |
Access Management is the set of practices that enables only those permitted the ability to perform an action on a particular resource. The three most common Access Management services you encounter every day perhaps without realizing it are: Policy Administration, Authentication, and Authorization [B48]. |
Agent |
A host-based intrusion prevention system program that monitors and analyzes activity and performs preventive actions; OR a program or plug-in that enables an SSL VPN to access non-Web-based applications and services [B49]. |
Application Layer |
Layer of the TCP/IP protocol stack that sends and receives data for particular applications such as DNS, HTTP, and SMTP [B49]. |
App-Vetting Process |
The process of verifying that an app meets an organization’s security requirements. An app vetting process comprises app testing and app approval/rejection activities [B50]. |
Brute-Force Attack |
In cryptography, an attack that involves trying all possible combinations to find a match [B51]. |
Chief Information Officers (CIO) Council |
The CIO Council is the principal interagency forum for improving agency practices related to the design, acquisition, development, modernization, use, sharing, and performance of Federal information resources [B52]. |
Common Vulnerabilities and Exposures |
A dictionary of common names for publicly known information system vulnerabilities [B53]. |
Corporate-Owned Personally-Enabled (COPE) |
A device owned by an enterprise and issued to an employee. Both the enterprise and the employee can install applications onto the device. |
Cryptographic Algorithm |
A well-defined computational procedure that takes variable inputs, including a cryptographic key, and produces an output [B54]. |
Cryptographic Key |
A value used to control cryptographic operations, such as decryption, encryption, signature generation, or signature verification [B55]. |
Cryptography |
The discipline that embodies the principles, means, and methods for the transformation of data in order to hide their semantic content, prevent their unauthorized use, or prevent their undetected modification [B54]. |
Data Action |
System operations that process PII [B20]. |
De-identification |
General term for any process of removing the association between a set of identifying data and the data subject [B51]. |
Demilitarized Zone (DMZ) |
A network created by connecting two firewalls. Systems that are externally accessible but need some protections are usually located on DMZ networks [B56]. |
Disassociability |
Enabling the processing of PII or events without association to individuals or devices beyond the operational requirements of the system [B20]. |
Encryption |
The cryptographic transformation of data to produce ciphertext [B54]. |
Enterprise Mobility Management |
Enterprise Mobility Management (EMM) systems are a common way of managing mobile devices in the enterprise. Although not a security technology by itself, EMMs can help to deploy policies to an enterprise’s device pool and to monitor device state [B9]. |
Identity Verification |
Confirmation, through the provision of objective evidence, that specified requirements have been fulfilled (e.g., an entity’s requirements have been correctly defined, or an entity’s attributes have been correctly presented; or a procedure or function performs as intended and leads to the expected outcome). Adapted from Verification [B54]. |
Impact |
The effect on organizational operations, organizational assets, individuals, other organizations, or the Nation (including the national security interests of the United States) of a loss of confidentiality, integrity, or availability of information or an information system [B11]. |
Key Logger |
A remote program designed to record which keys are pressed on a computer keyboard used to obtain passwords or encryption keys and thus bypass other security measures [B57]. |
Malware |
Software or firmware intended to perform an unauthorized process that will have adverse impact on the confidentiality, integrity, or availability of an information system. A virus, worm, Trojan horse, or other code-based entity that infects a host. Spyware and some forms of adware are also examples of malicious code [B11]. |
Manageability |
Providing the capability for granular administration of data, including alteration, deletion, and selective disclosure [B20]. |
Mobile Device |
A portable computing device that: (i) has a small form factor such that it can easily be carried by a single individual; (ii) is designed to operate without a physical connection (e.g., wirelessly transmit or receive information); (iii) possesses local, non-removable or removable data storage; and (iv) includes a self-contained power source. Mobile devices may also include voice communication capabilities, on-board sensors that allow the devices to capture information, and/or built-in features for synchronizing local data with remote locations. Examples include smart phones, tablets, and E-readers [B11]. |
Mobile Device Management (MDM) |
The administration of mobile devices such as smartphones, tablets, computers, laptops, and desktop computers. MDM is usually implemented through a third-party product that has management features for particular vendors of mobile devices [B50]. |
Network Layer |
Layer of the TCP/IP protocol stack that is responsible for routing packets across networks [B49]. |
Person (Man)-in-the-Middle Attack |
An attack in which an attacker is positioned between two communicating parties in order to intercept and/or alter data traveling between them. In the context of authentication, the attacker would be positioned between claimant and verifier, between registrant and CSP during enrollment, or between subscriber and CSP during authenticator binding [B55]. |
Phishing |
An attack in which the subscriber is lured (usually through an email) to interact with a counterfeit verifier/RP and tricked into revealing information that can be used to masquerade as that subscriber to the real verifier/RP [B55]. |
Predictability |
Enabling reliable assumptions by individuals, owners, and operators about data and their processing by a system, product, or service [B20]. |
Predisposing Conditions |
A condition that exists within an organization, a mission/business process, enterprise architecture, or information system including its environment of operation, which contributes to (i.e., increases or decreases) the likelihood that one or more threat events, once initiated, will result in undesirable consequences or adverse impact to organizational operations and assets, individuals, other organizations, or the Nation [B12]. |
Privacy Risk Assessment Methodology (PRAM) |
The PRAM is a tool that applies the risk model from NISTIR 8062 and helps organizations analyze, assess, and prioritize privacy risks to determine how to respond and select appropriate solutions. The PRAM can help drive collaboration and communication between various components of an organization, including privacy, cybersecurity, business, and IT personnel [B58]. |
Read-Only Memory |
ROM is a pre-recorded storage medium that can only be read from and not written to [B59]. |
Red Team Exercise |
An exercise, reflecting real-world conditions, that is conducted as a simulated adversarial attempt to compromise organizational missions and/or business processes to provide a comprehensive assessment of the security capability of the information system and organization [B11]. |
Replay Resistance |
Protection against the capture of transmitted authentication or access control information and its subsequent retransmission with the intent of producing an unauthorized effect or gaining unauthorized access [B60]. |
Risk |
A measure of the extent to which an entity is threatened by a potential circumstance or event, and typically a function of: (i) the adverse impacts that would arise if the circumstance or event occurs; and (ii) the likelihood of occurrence [B12]. |
Risk Assessment |
The process of identifying risks to organizational operations (including mission, functions, image, reputation), organizational assets, individuals, other organizations, and the Nation, resulting from the operation of an information system. Part of risk management, incorporates threat and vulnerability analyses, and considers mitigations provided by security controls planned or in place. Synonymous with risk analysis [B11]. |
Risk Management Framework |
The Risk Management Framework (RMF) provides a structured, yet flexible approach for managing the portion of risk resulting from the incorporation of systems into the mission and business processes of the organization [B61]. |
Sandbox |
A restricted, controlled execution environment that prevents potentially malicious software, such as mobile code, from accessing any system resources except those for which the software is authorized (Under Sandboxing) [B54]. |
Security Control |
A safeguard or countermeasure prescribed for an information system or an organization designed to protect the confidentiality, integrity, and availability of its information and to meet a set of defined security requirements [B11]. |
Side-Channel Attacks |
An attack enabled by leakage of information from a physical cryptosystem. Characteristics that could be exploited in a side-channel attack include timing, power consumption, and electromagnetic and acoustic emissions [B55]. |
Social Engineering |
The act of deceiving an individual into revealing sensitive information, obtaining unauthorized access, or committing fraud by associating with the individual to gain confidence and trust [B55]. |
Threat |
Any circumstance or event with the potential to adversely impact organizational operations (including mission, functions, image, or reputation), organizational assets, individuals, other organizations, or the Nation through an information system via unauthorized access, destruction, disclosure, or modification of information, and/or denial of service [B12]. |
Threat Events |
An event or situation that has the potential for causing undesirable consequences or impact [B12]. |
Threat Intelligence |
Threat information that has been aggregated, transformed, analyzed, interpreted, or enriched to provide the necessary context for decision-making processes [B62]. |
Threat Sources |
The intent and method targeted at the intentional exploitation of a vulnerability or a situation and method that may accidentally trigger a vulnerability. Synonymous with threat agent [B11]. |
Transport Layer |
Layer of the TCP/IP protocol stack that is responsible for reliable connection-oriented or connectionless end-to-end communications [B49]. |
Transport Layer Security (TLS) |
A security protocol providing privacy and data integrity between two communicating applications. The protocol is composed of two layers: the TLS Record Protocol and the TLS Handshake Protocol [B54]. |
Trusted Certificate |
A certificate that is trusted by the Relying Party on the basis of secure and authenticated delivery. The public keys included in trusted certificates are used to start certification paths. Also known as a “trust anchor” [B63]. |
Unmanaged Device |
A device inside the assessment boundary that is either unauthorized or, if authorized, not assigned to a person to administer [B64]. |
Virtual Private Network |
Protected information system link utilizing tunneling, security controls, and endpoint address translation giving the impression of a dedicated line [B54]. |
Vulnerability |
Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited by a threat source [B12]. |
Watering Hole |
Watering hole attacks involve attackers compromising one or more legitimate Web sites with malware in an attempt to target and infect visitors to those sites [B65]. |
Appendix C References¶
- B1
National Institute of Standards and Technology (NIST), “NIST Computer Security Resource Center,” [Online]. Available: https://csrc.nist.gov/publications/sp800.
- B2
National Information Assurance Partnership (NIAP), “NIAP Home Page,” [Online]. Available: https://www.niap-ccevs.org/.
- B3
Department of Homeland Security, “Home Page,” [Online]. Available: https://www.dhs.gov/.
- B4
Federal Chief Information Officers (CIO) Council, “Federal CIO Home Page,” [Online]. Available: https://www.cio.gov/.
- B5
National Institute of Standards and Technology (NIST), “NIST Cybersecurity Framework, Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1,” 16 April 2018. [Online]. Available: https://www.nist.gov/cyberframework.
- B6
National Institute of Standards and Technology (NIST), “NIST Privacy Engineering Program,” [Online]. Available: https://www.nist.gov/itl/applied-cybersecurity/privacy-engineering/resources.
- B7
National Institute of Standards and Technology (NIST), “NIST SP 800-181, National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework,” August 2017. [Online]. Available: https://csrc.nist.gov/publications/detail/sp/800-181/final.
- B8
National Institute of Standards and Technology (NIST), “Risk Management Framework (RMF) Overview,” [Online]. Available: https://csrc.nist.gov/projects/risk-management/risk-management-framework-(rmf)-overview.
- B9(1,2,3,4)
National Institute of Standards and Technology (NIST), “Mobile Threat Catalogue,” [Online]. Available: https://pages.nist.gov/mobile-threat-catalogue/.
- B10
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Mobile Device Security for Enterprises Building Block Version 2 Final Draft,” 12 September 2014. [Online]. Available: https://www.nccoe.nist.gov/sites/default/files/library/project-descriptions/mds-project-description-final.pdf.
- B11(1,2,3,4,5,6,7,8)
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-53 Revision 4, Security and Privacy Controls for Federal Information Systems and Organizations,” 22 January 2015. [Online]. Available: https://csrc.nist.gov/publications/sp.
- B12(1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17)
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-30 Revision 1, Guide for Conducting Risk Assessments,” September 2012. [Online]. Available: https://csrc.nist.gov/publications/detail/sp/800-30/rev-1/final.
- B13
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-124 Revision 2 Draft, Guidelines for Managing the Security of Mobile Devices in the Enterprise,” March 2020. [Online]. Available: https://csrc.nist.gov/publications/detail/sp/800-124/rev-2/draft.
- B14
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 1800-4, Mobile Device Security: Cloud and Hybrid Builds,” 21 February 2019. [Online]. Available: https://www.nccoe.nist.gov/projects/building-blocks/mobile-device-security/cloud-hybrid.
- B15
International Organization for Standardization / International Electrotechnical Commission / Institute of Electrical and Electronics Engineers (ISO/IEC/IEEE), “International Organization for Standardization / International Electrotechnical Commission / Institute of Electrical and Electronics Engineers (ISO/IEC/IEEE) 15288:2015, Systems and software engineering – System life cycle processes,” 2015. [Online]. Available: https://www.iso.org/standard/63711.html.
- B16
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-160 Volume 1: Systems Security Engineering: Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems,” November 2016. [Online]. Available: https://csrc.nist.gov/publications/detail/sp/800-160/vol-1/final.
- B17
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-37, Revision 2, Risk Management Framework for Information Systems and Organizations, A System Life Cycle Approach for Security and Privacy,” December 2018. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-37r2.pdf.
- B18
Tech Times, “Flashlight apps are spying on users Android, iOS, Windows Phone smartphones, is yours on the list?,” 26 October 2014. [Online]. Available: https://www.techtimes.com/articles/18762/20141026/flashlight-apps-are-spying-on-users-android-ios-windows-phone-smartphones-is-yours-on-the-list.htm.
- B19
National Institute of Standards and Technology (NIST), “NIST Privacy Framework,” [Online]. Available: https://www.nist.gov/privacy-framework.
- B20(1,2,3,4,5)
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Internal Report (NISTIR) 8062, An Introduction to Privacy Engineering and Risk Management in Federal Systems,” January 2017. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/ir/2017/NIST.IR.8062.pdf.
- B21
M. A. A. B. Mohamed Sabt, “Trusted Execution Environment: What It is, and What It is Not. 14th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Helsinki, Finland,” August 2015. [Online]. Copy and paste link into browser to access. Available: https://hal.archives-ouvertes.fr/hal-01246364/file/trustcom_2015_tee_what_it_is_what_it_is_not.pdf.
- B22
Zimperium, “MobileIron Threat Defense, Mobile Device Security & MDM,” [Online]. Available: https://www.zimperium.com/partners/mobileiron.
- B23
National Information Assurance Partnership (NIAP), “U.S. Government Approved Protection Profile - Protection Profile for Mobile Device Management Version 4.0,” 25 April 2019. [Online]. Available: https://www.niap-ccevs.org/Profile/PP.cfm.
- B24
National Information Assurance Partnership (NIAP), “U.S. Government Approved Protection Profile - Extended Package for VPN Gateways Version 2.1,” 8 March 2017. [Online]. Available: https://www.niap-ccevs.org/Profile/PP.cfm.
- B25
National Information Assurance Partnership (NIAP), “U.S. Government Approved Protection Profile - Collaborative Protection Profile for Network Devices Version 2.0 + Errata 20180314,” 14 March 2018. [Online]. Available: https://www.niap-ccevs.org/Profile/PP.cfm.
- B26
National Information Assurance Partnership, “Approved Protection Profiles,” [Online]. Available: https://www.niap-ccevs.org/Profile/PP.cfm.
- B27
Qualcomm, “Qualcomm Secure Boot and Image Authentication Technical Overview,” [Online]. Available: https://www.qualcomm.com/media/documents/files/secure-boot-and-image-authentication-technical-overview-v1-0.pdf.
- B28
National Information Assurance Partnership (NIAP), “Product Compliant List,” [Online]. Available: https://www.niap-ccevs.org/Product/.
- B29
Palo Alto Networks, “Remote Access VPN (Certificate Profile),” [Online]. Available: https://docs.paloaltonetworks.com/globalprotect/8-1/globalprotect-admin/globalprotect-quick-configs/remote-access-vpn-certificate-profile.
- B30
MobileIron, “Admin Google Android Google Apps API,” [Online]. Available: http://mi.extendedhelp.mobileiron.com/45/all/en/desktop/Google_Apps_API.htm.
- B31
MobileIron, “MobileIron unified endpoint security platform,” [Online]. Available: https://www.mobileiron.com/en/unified-endpoint-management/platform.
- B32
Open Web Application Security Project (OWASP), [Online]. Available: https://www.owasp.org/index.php/Main_Page.
- B33
Palo Alto Networks, “Always On VPN Configuration,” [Online]. Available: https://docs.paloaltonetworks.com/globalprotect/7-1/globalprotect-admin/globalprotect-quick-configs/always-on-vpn-configuration.
- B34
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-46 Revision 2, Guide to Enterprise Telework, Remote Access, and Bring Your Own Device (BYOD) Security,” July 2016. [Online]. Available: https://csrc.nist.gov/publications/detail/sp/800-46/rev-2/final.
- B35
National Institute of Standards and Technology (NIST), “Cryptographic Module Validation Program,” [Online]. Available: https://csrc.nist.gov/projects/cryptographic-module-validation-program.
- B36
Palo Alto Networks, “FIPS-CC Security Functions documentation site,” [Online]. Available: https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/certifications/fips-cc-security-functions.
- B37
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-52, Revision 2, Guidelines for the Selection, Configuration, and Use of Transport Layer Security (TLS) Implementations,” August 2019. [Online]. Available: https://csrc.nist.gov/publications/detail/sp/800-52/rev-2/final.
- B38
Apple Computer, “Apple at Work,” [Online]. Available: https://www.apple.com/business/it/.
- B39
Apple Computer, “Apple Configurator 2,” [Online]. Available: https://itunes.apple.com/us/app/apple-configurator-2/id1037126344?mt=12.
- B40
Apple Computer, “Apple Platform Security,” [Online]. Available: https://support.apple.com/guide/security/welcome/web.
- B41
Android.com, “Build a device policy controller,” [Online]. Available: https://developer.android.com/work/dpc/build-dpc.
- B42
Android.com, “Work profiles on fully managed devices,” [Online]. Available: https://developers.google.com/android/work/requirements/work-profile.
- B43
Google.com, “Android Enterprise Fully managed device,” [Online]. Available: https://developers.google.com/android/work/requirements/fully-managed-device.
- B44
Google.com, “Android Enterprise Work profile,” [Online]. Available: https://www.android.com/enterprise/.
- B45
International Organization for Standardization (ISO), International Electrotechnical Commission (IEC), “ISO/IEC 27001:2013 Information technology – Security techniques – Information security management systems – Requirements,” October 2013. [Online]. Available: https://www.iso.org/standard/54534.html.
- B46
Center for Internet Security, “Center for Internet Security Home Page,” [Online]. Available: https://www.cisecurity.org/.
- B47
Google.com, “Google Play Store,” [Online]. Available: https://play.google.com/store/apps.
- B48
IDManagement.gov, “Federal Identity, Credential, and Access Management Architecture,” [Online]. Available: https://arch.idmanagement.gov/services/access/.
- B49(1,2,3,4,5)
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-113 Guide to SSL VPNs,” July 2008. [Online]. Available: https://csrc.nist.gov/publications/detail/sp/800-113/final.
- B50(1,2,3)
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-163 Revision 1, Vetting the Security of Mobile Applications,” April 2019. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-163r1.pdf.
- B51(1,2)
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Internal Report (NISTIR) 8053, De-Identification of Personal Information,” October 2015. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/ir/2015/NIST.IR.8053.pdf.
- B52
General Services Administration, “Chief Information Officers Council (CIOC),” [Online]. Available: https://www.gsa.gov/about-us/organization/office-of-governmentwide-policy/office-of-shared-solutions-and-performance-improvement/chief-information-officers-council-cioc.
- B53
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-126 Revision 3, The Technical Specification for the Security Content Automation Protocol (SCAP),” February 2018. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-126r3.pdf.
- B54(1,2,3,4,5,6,7)
Committee on National Security Systems, “Committee on National Security Systems (CNSS) Glossary, Publication 4009,” 6 April 2015. [Online]. Available: https://www.cnss.gov/CNSS/issuances/Instructions.cfm.
- B55(1,2,3,4,5)
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-63-3, Digital Identity Guidelines,” 2 March 2020. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-63-3.pdf.
- B56
National Institute of Standards and Technology (NIST), “NISTIR 7711 Security Best Practices for the Electronic Transmission of Election Materials for UOCAVA Voters,” September 2011. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/Legacy/IR/nistir7711.pdf.
- B57
National Institute of Standards and Technology (NIST), “NIST Special Publication 800-82 Revision 2, Guide to Industrial Control Systems (ICS) Security,” May 2015. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-82r2.pdf.
- B58
National Institute of Standards and Technology (NIST), “Risk Assessment Tools,” [Online]. Available: https://www.nist.gov/itl/applied-cybersecurity/privacy-engineering/collaboration-space/browse/risk-assessment-tools.
- B59
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication 800-88, Revision 1, Guidelines for Media Sanitization,” December 2014. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-88r1.pdf.
- B60(1,2)
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171, Revision 2, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations,” February 2020. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-171r2.pdf.
- B61
National Institute of Standards and Technology (NIST), “Risk Management Framework: Quick Start Guide,” [Online]. Available: https://csrc.nist.gov/projects/risk-management/risk-management-framework-quick-start-guides.
- B62
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-150, Guide to Cyber Threat Information Sharing,” October 2016. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-150.pdf.
- B63
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-32, Introduction to Public Key Technology and the Federal PKI Infrastructure,” February 2001. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-32.pdf.
- B64
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Interagency Report (NISTIR) 8011 Volume 1, Automation Support for Security Control Assessments,” June 2017. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/ir/2017/NIST.IR.8011-1.pdf.
- B65
United States Department of Homeland Security, “ICS-CERT Monitor,” October, November, December 2013. [Online]. Available: https://ics-cert.us-cert.gov/sites/default/files/Monitors/ICS-CERT_Monitor_Oct-Dec2013.pdf.
- B66
National Institute of Standards and Technology (NIST), “Digital Identity Guidelines,” 2 March 2020. [Online]. Available: https://csrc.nist.gov/publications/sp.
- B67
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Special Publication (SP) 800-114 Revision 1, User’s Guide to Telework and Bring Your Own Device (BYOD) Security,” July 2016. [Online]. Available: https://csrc.nist.gov/publications/detail/sp/800-114/rev-1/final.
- B68
Executive Office of the President, “Bring Your Own Device, A Toolkit to Support Federal Agencies Implementing Bring Your Own Device (BYOD) Programs,” 23 August 2012. [Online]. Available: https://obamawhitehouse.archives.gov/digitalgov/bring-your-own-device.
- B69
Federal CIO Council and Department of Homeland Security, “Mobile Security Reference Architecture Version 1.0,” 23 May 2013. [Online]. Available: https://s3.amazonaws.com/sitesusa/wp-content/uploads/sites/1151/2016/10/Mobile-Security-Reference-Architecture.pdf.
- B70
Digital Services Advisory Group and Federal Chief Information Officers Council, “Government Use of Mobile Technology Barriers, Opportunities, and Gap Analysis,” December 2012. [Online]. Available: https://s3.amazonaws.com/sitesusa/wp-content/uploads/sites/1151/2016/10/Government_Mobile_Technology_Barriers_Opportunities_and_Gaps.pdf.
- B71
“Mobile Computing Decision,” [Online]. Available: https://s3.amazonaws.com/sitesusa/wp-content/uploads/sites/1151/2016/10/Mobile-Security-Decision-Framework-Appendix-B.pdf.
- B72
Mobile Services Category Team (MSCT) Advanced Technology Academic Research Center (ATARC), “Mobility Strategy Development Guidelines Working Group Document,” June 2017. [Online]. Available: https://hallways.cap.gsa.gov/app/#/gateway/mobile-services-category-team/9658/docs/12997/Agency_Mobility_Strategy_Deliverable.pdf.
- B73
Mobile Services Category Team (MSCT) Advanced Technology Academic Research Center (ATARC), “Mobile Threat Protection App Vetting and App Security Working Group Document,” July 2017. [Online]. Available: https://hallways.cap.gsa.gov/app/#/gateway/mobile-services-category-team/9658/docs/12996/Mobile_Threat_Protection_Deliverable.pdf.
- B74
Mobile Services Category Team (MSCT), “Device Procurement and Management Guidance,” November 2016. [Online]. Available: https://hallways.cap.gsa.gov/app/#/gateway/information-technology/4485/mobile-device-procurement-and-management-guidance.
- B75
Mobile Services Category Team (MSCT), “Mobile Device Management (MDM) MDM Working Group Document,” August 2017. [Online]. Available: https://s3.amazonaws.com/sitesusa/wp-content/uploads/sites/1197/2017/10/EMM_Deliverable.pdf.
- B76
Mobile Services Category Team (MSCT), “Mobile Services Roadmap (MSCT Strategic Approach),” 23 September 2016. [Online]. Available: https://atarc.org/project/mobile-services-roadmap-msct-strategic-approach/.
- B77
National Information Assurance Partnership (NIAP), “NIAP U.S. Government Approved Protection Profile - Extended Package for Mobile Device Management Agents Version 3.0,” 21 November 2016. [Online]. Available: https://www.niap-ccevs.org/Profile/Info.cfm?PPID=403&id=403.
- B78
National Information Assurance Partnership (NIAP), “U.S. Government Approved Protection Profile - Protection Profile for Mobile Device Fundamentals Version 3.1,” 16 June 2017. [Online]. Available: https://www.niap-ccevs.org/Profile/PP.cfm.
- B79
National Information Assurance Partnership (NIAP), “U.S. Government Approved Protection Profile - Protection Profile for Mobile Device Management Version 3.0,” 21 November 2016. [Online]. Available: https://www.niap-ccevs.org/Profile/Info.cfm?PPID=392&id=392.
- B80
United States Office of Management and Budget (OMB), “Category Management Policy 16-3: Improving the Acquisition and Management of Common Information Technology: Mobile Devices and Services,” 4 August 2016. [Online]. Available: https://www.whitehouse.gov/sites/whitehouse.gov/files/omb/memoranda/2016/m_16_20.pdf.
- B81
National Institute of Standards and Technology (NIST), “United States Government Configuration Baseline (In Development),” [Online]. Available: https://csrc.nist.gov/Projects/United-States-Government-Configuration-Baseline.
- B82
Department of Homeland Security (DHS), “DHS Study on Mobile Device Security,” April 2017. [Online]. Available: https://www.dhs.gov/publication/csd-mobile-device-security-study.
- B83
Android, “Android zero-touch enrollment,” [Online]. Available: https://www.android.com/enterprise/management/zero-touch/.
- B84
Google, “Android’s enterprise requirements,” [Online]. Available: https://support.google.com/work/android/answer/6174145?hl=en.
- B85
Apple, “Business Support,” [Online]. Available: https://support.apple.com/business.
- B86
Apple, “Configuration Profile,” 3 May 2019. [Online]. Available: https://developer.apple.com/business/documentation/Configuration-Profile-Reference.pdf.
- B87
Samsung, “Knox Mobile Enrollment,” [Online]. Available: https://www.samsungknox.com/en/solutions/it-solutions/knox-mobile-enrollment.
- B88
Samsung, “Secured by Knox,” [Online]. Available: https://www.samsungknox.com/en/secured-by-knox.
- B89
Samsung, “Devices built on Knox,” [Online]. Available: https://www.samsungknox.com/en/knox-platform/supported-devices.
- B90
Samsung, “Knox features on Android,” [Online]. Available: https://www.samsungknox.com/en/knox-features/android/kme.
- B91
The MITRE Corporation, “ATT&CK,” [Online]. Available: https://attack.mitre.org/.
- B92
National Institute of Standards and Technology (NIST), “National Institute of Standards and Technology (NIST) Interagency Report (NISTIR) 8144 (Draft), Assessing Threats to Mobile Devices & Infrastructure: the Mobile Threat Catalogue,” [Online]. Available: https://csrc.nist.gov/publications/detail/nistir/8144/draft.
- B93
The MITRE Corporation, “ATT&CK for Mobile,” [Online]. Available: https://attack.mitre.org/resources/mobile-introduction/.
- B94
The MITRE Corporation, “Common Vulnerabilities and Exposures (CVEs),” [Online]. Available: http://cve.mitre.org/.
- B95
FedRAMP, “FedRAMP Home Page,” [Online]. Available: https://www.fedramp.gov/.
- B96
National Institute of Standards and Technology (NIST), “NIST Information Technlogy Laboratory National Vulnerability Database,” [Online]. Available: https://nvd.nist.gov/.
- B97
Android Open Source Project, “Pixel / Nexus Security Bulletins,” [Online]. Available: https://source.android.com/security/bulletin/pixel/.
- B98
Apple Computers, “Apple Security Updates,” [Online]. Available: https://support.apple.com/en-us/HT201222.
- B99
Apple, “Managing Devices & Corporate Data on iOS,” July 2018. [Online]. Available: https://www.apple.com/business/resources/docs/Managing_Devices_and_Corporate_Data_on_iOS.pdf.
- B100
Samsung, “Android Security Updates,” [Online]. Available: https://security.samsungmobile.com/securityUpdate.smsb.
Appendix D Standards and Guidance¶
National Institute of Standards and Technology (NIST) Cybersecurity Framework Version 1.1 [B5]
NIST Mobile Threat Catalogue [B9]
NIST Risk Management Framework [B8]
NIST Special Publication (SP) 1800-4, Mobile Device Security: Cloud and Hybrid Builds [B14]
NIST SP 800-30 Revision 1, Guide for Conducting Risk Assessments [B12]
NIST SP 800-37 Revision 2, Risk Management Framework for Information Systems and Organizations [B17]
NIST SP 800-46 Revision 2, Guide to Enterprise Telework, Remote Access, and Bring Your Own Device (BYOD) Security [B34]
NIST SP 800-52 Revision 2, Guidelines for the Selection, Configuration, and Use of Transport Layer Security (TLS) Implementations [B37]
NIST SP 800-53 Revision 4, Security and Privacy Controls for Federal Information Systems and Organizations [B11]
NIST SP 800-63, Digital Identity Guidelines [B66]
NIST SP 800-113, Guide to SSL VPNs [B49]
NIST SP 800-114 Revision 1, Userʼs Guide to Telework and Bring Your Own Device (BYOD) Security [B67]
NIST SP 800-124 Revision 2 Draft, Guidelines for Managing the Security of Mobile Devices in the Enterprise [B13]
NIST SP 800-163 Revision 1, Vetting the Security of Mobile Applications [B50]
NIST SP 800-171 Revision 2, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations [B60]
NIST SP 800-181, National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework [B7]
Center for Internet Security [B46]
Executive Office of the President, Bring Your Own Device Toolkit [B68]
Federal Chief Information Officers (CIO) Council and Department of Homeland Security (DHS) Mobile Security Reference Architecture, Version 1.0 [B69]
Digital Services Advisory Group and Federal Chief Information Officers Council, Government Use of Mobile Technology Barriers, Opportunities, and Gap Analysis [B70]
International Organization for Standardization (ISO), International Electrotechnical Commission (IEC) 27001:2013, Information technology–Security techniques–Information security management systems–Requirements [B45]
Mobile Computing Decision Example Case Study [B71]
Mobile Services Category Team (MSCT) Advanced Technology Academic Research Center (ATARC), Mobility Strategy Development Guidelines Working Group Document [B72]
MSCT ATARC, Mobile Threat Protection App Vetting and App Security Working Group Document [B73]
MSCT, Device Procurement and Management Guidance [B74]
MSCT, Mobile Device Management (MDM), MDM Working Group Document [B75]
MSCT, Mobile Services Roadmap, MSCT Strategic Approach [B76]
NIAP U.S. Government Approved Protection Profile—Extended Package for Mobile Device Management Agents Version 3.0 [B77]
NIAP U.S. Government Approved Protection Profile—Protection Profile for Mobile Device Fundamentals Version 3.1 [B78]
NIAP U.S. Government Approved Protection Profile—Protection Profile for Mobile Device Management Version 3.0 [B79]
NIAP Product Compliant List [B28]
United States Office of Management and Budget (OMB), Category Management Policy 16-3: Improving the Acquisition and Management of Common Information Technology: Mobile Devices and Services [B80]
The United States Government Configuration Baseline (USGCB) [B81]
United State Department of Homeland Security (DHS) Study on Mobile Device Security [B82]
Appendix E Android, Apple, and Samsung Knox Mobile Enrollment¶
Device enrollment and management capabilities are available when deploying mobile devices in bulk. Certain settings can be preloaded, and devices can ship preconfigured for enterprise management. iOS-, Android-, and Samsung Knox-based devices integrate directly with Enterprise Mobility Management (EMM) solutions, providing enterprise-level management of security controls based on policy.
E.1 Android Devices¶
For Android devices, zero-touch enrollment provides an option different from the manual setup of Android devices. Android-based devices offer security controls that an EMM can leverage for enterprise deployments. The Android Enterprise program by Google is available on devices with Android 5.0 (Lollipop) and higher. An EMM deploys a device policy controller as part of its on-device agent that controls local device policies and system applications on devices. Android Enterprise supports corporate-owned personally-enabled and bring your own device deployment scenarios through work-managed and work-profile device solutions [B83], [B84].
E.2 iOS Devices¶
For iOS devices, Apple Configurator supports Volume Purchase and Device Enrollment Program scenarios. Apple Business Manager provides a mobile device management solution to assist organizations in deploying iOS devices. iOS devices are managed by configuration profiles. Configuration profiles can force security policies such as virtual private network usage, enterprise Kerberos support, and access to cloud services. iOS further incorporates a set of additional security controls in what is termed supervised mode, which denotes a corporately owned device.
Typically, organizations choose to use the Device Enrollment Program for large-scale deployments of iOS devices in supervised mode due to the reduction of labor involved in manually configuring each device. However, due to the small number of devices in our reference design, we have configured supervised mode using the Apple Configurator 2 tool. A more detailed description of iOS capabilities can be found in the iOS Security Guide [B85], [B86].
E.3 Samsung Knox Devices¶
Samsung Knox Mobile Enrollment provides the ability to add Samsung devices to the enterprise without manually enrolling each device. Samsung Knox Mobile Enrollment works on Samsung Galaxy devices running Android Lollipop or higher. It allows remote provisioning of devices when they connect to Wi-Fi or cellular networks. Samsung Knox Mobile Enrollment works with a number of EMM solutions, including cloud-based options [B87], [B88], [B89], [B90].
Appendix F Risk Assessment¶
F.1 Risk Assessment¶
National Institute of Standards and Technology (NIST) Special Publication (SP) 800-30 Revision 1, Guide for Conducting Risk Assessments, [B12] states that risk is “a measure of the extent to which an entity is threatened by a potential circumstance or event, and typically a function of: (i) the adverse impacts that would arise if the circumstance or event occurs; and (ii) the likelihood of occurrence.” The guide further defines risk assessment as “the process of identifying, estimating, and prioritizing risks to organizational operations (including mission, functions, image, reputation), organizational assets, individuals, other organizations, and the Nation, resulting from the operation of an information system. Part of risk management incorporates threat and vulnerability analyses, and considers mitigations provided by security controls planned or in place.”
The NCCoE recommends that any discussion of risk management, particularly at the enterprise level, begins with a comprehensive review of NIST SP 800-37 Revision 2, Risk Management Framework for Information Systems and Organizations—material that is available to the public. The Risk Management Framework (RMF) guidance, as a whole, proved to be invaluable in giving us a baseline to assess risks, from which we developed the project, the security characteristics of the build, and this guide.
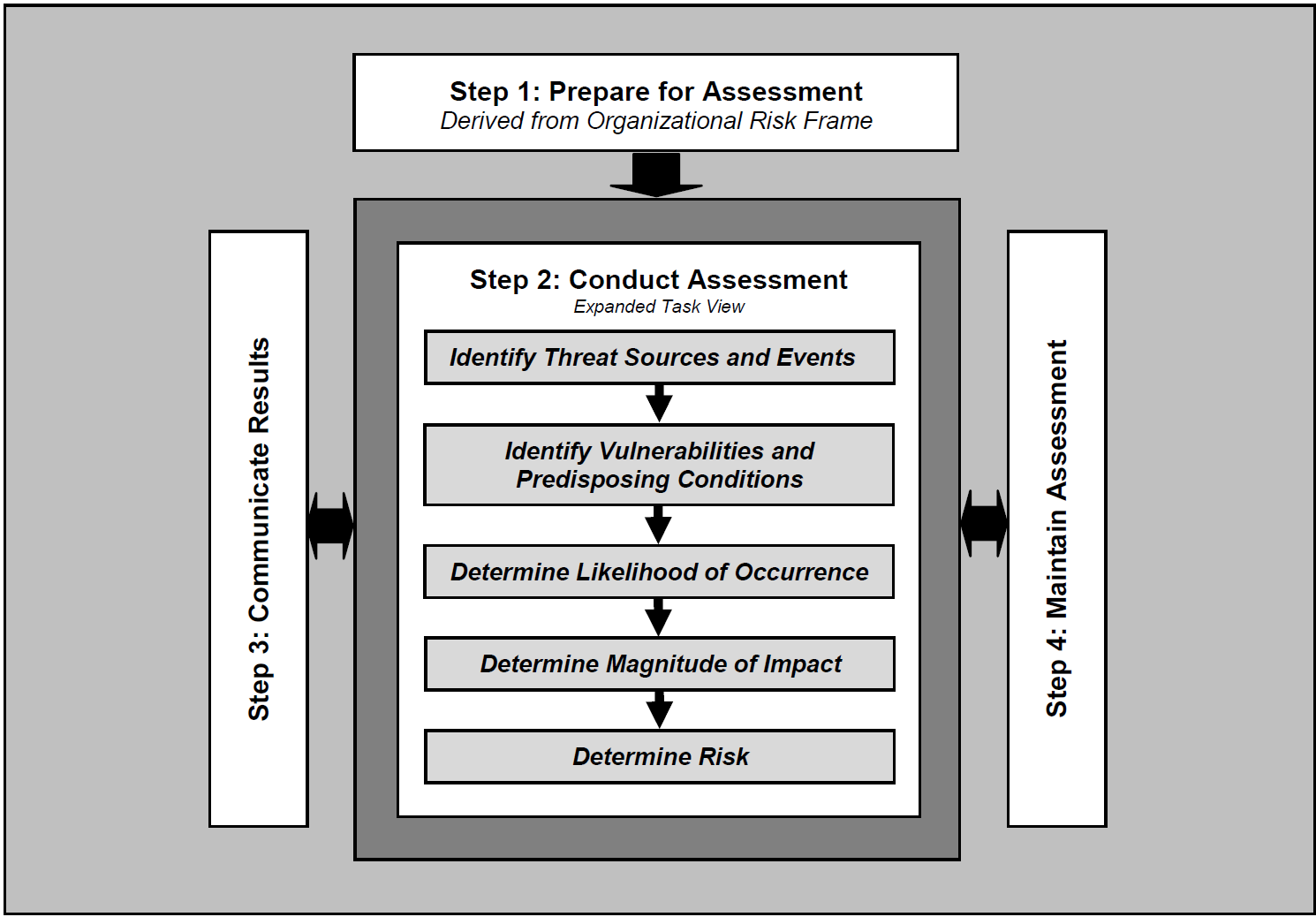
This section details the risk assessment undertaken to improve the mobile security posture of the fictional organization Orvilia Development. Typically, a NIST SP 800-30 Revision 1-based risk assessment follows a four-step process as shown in Figure F‑1: Prepare for assessment, conduct assessment, communicate results, and maintain assessment.
Figure F‑1 Risk Assessment Process
To provide the most value in this exercise:
We focused on the preparation, which established the context of the risk assessment.
We conducted the risk assessment, which produced a list of information security risks that were prioritized by risk level and used to inform risk response decisions.
We followed the process detailed in Section 3 of NIST SP 800-30 Revision 1 [B12] to perform a risk assessment of the current mobile infrastructure.
We recommend that organizations performing a risk assessment communicate results and perform maintenance of the risk assessment, but these activities were deemed out of scope for this project. The following tasks were used during the assessment process.
F.1.1 Task 1-1: Risk Assessment Purpose¶
Identify the purpose of the risk assessment in terms of the information that the assessment is intended to produce and the decisions the assessment is intended to support.
The purpose of the risk assessment of Orvilia Development was to identify and document new risks to its mission resulting from addition of a mobility program.
The results of the risk assessment informed decisions to Orvilia’s mobility deployment that included:
implementation of new security mechanisms
configuration changes to existing infrastructure
updates to security and appropriate-use policies relevant to their mobility program
F.1.2 Task 1-2: Risk Assessment Scope¶
Identify the scope of the risk assessment in terms of organizational applicability, time frame supported, and architectural/technology considerations.
Organizational Applicability:
The scope of this risk assessment was limited to systems impacted by inclusion of a mobility program; it did not include existing information technology (IT) infrastructure to which no impact was anticipated. With their original architecture, Orvilia deployed corporate-owned personally-enabled (COPE) devices. Orvilia employees utilized mobile devices for local and remote work activities and limited personal activities (e.g., phone calls, messaging, social applications, and personal emails).
With Orvilia’s new government contract, this risk assessment also evaluated Orvilia’s mobile deployment regarding its ability to access and store government data while meeting applicable information security and privacy requirements.
While not directly associated with risk assessment activities, Orvilia will be required to demonstrate compliance with government standards and policies established to improve data security. Therefore, Orvilia needed to determine how compliance with government policy and application of its standards would best align with its strategy to identify, protect again, detect, respond to, and recover from threats related to its mobility program.
Time Frame Supported:
Because this was the first risk assessment performed by Orvilia, the process was more time-intensive than it will be in future risk management cycles. Orvilia completed the initial risk assessment within six months.
Architectural and Technology Considerations:
This risk assessment was scoped to Orvilia’s mobile deployment, which constitutes mobile devices used to access Orvilia enterprise resources along with any backend IT components used to manage or provide services to those mobile devices.
The following provide an overview of the mobile deployment components involved in the original (current) Orvilia architecture.
Mobile Device: A mobile device is a small form factor device with a rich operating system, at least one wireless network interface, and the ability to run applications. These features are considered essential for Orvilia to have portable and efficient access to enterprise data.
Communication Networks and Data Transmission: Mobile devices will establish connections to the internet by using their cellular or Wi-Fi adapters. As connections may be made to unsecured access points or may traverse untrusted networks, consideration will be given to the risks associated with the security of those connections and the data transmitted over them. Additionally, the organization will need to consider risks arising from permitting inbound connections by mobile devices via the internet.
Public Application Stores: With a COPE deployment strategy, employees will have the option to download any mobile application available from official platform application stores (e.g., Google Play Store). While those platforms analyze applications for malicious behaviors, it is still possible for such applications to exceed Orvilia’s needs for user privacy or pose a risk to the devices or data. Therefore, risks from such applications should be included in this assessment.
Device and Operating System (OS) Vendor Infrastructure: The hardware, firmware, and software that compose each model of mobile device can vary, particularly those from different manufacturers and vendors, which may incorporate technology that is exclusive to their products. It will be important to select devices that demonstrate security mechanisms that align with the organization’s risk mitigation strategy. However, risks that are specific to given device components (e.g., chipsets or driver versions) will be out of scope for this assessment.
Enterprise Systems: If a potentially compromised mobile device can connect to the enterprise, it poses direct risks to any systems it can reach or data it can access. Such systems will reasonably include on-premises mobile application stores, mobile management technologies, email servers, file servers, and intranet web servers. Subsequent compromise of any of these systems may cascade to others not directly reachable by the mobile device. Risks to all such systems by a mobile device should be included in this assessment.
F.1.3 Task 1-3: Risk Assessment Assumptions and Constraints¶
Identify the specific assumptions and constraints under which the risk assessment is conducted.
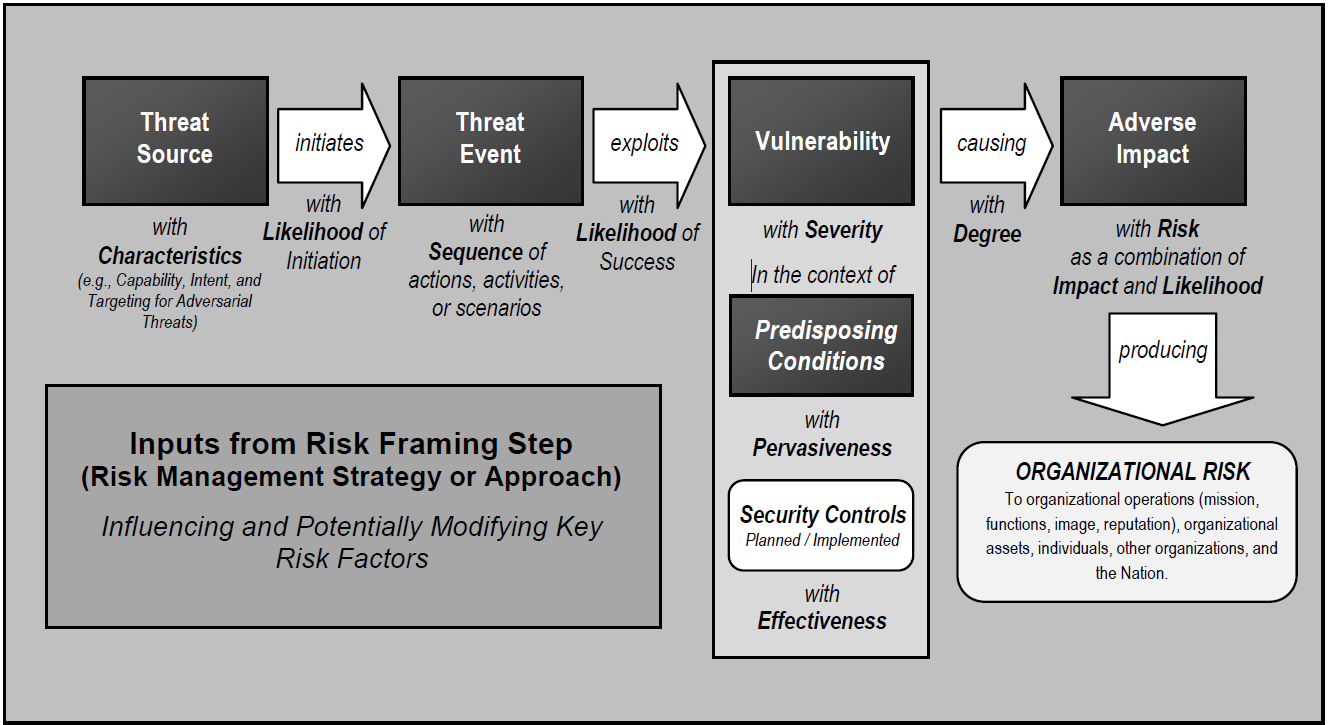
Risk assessment assumptions and constraints were developed using a NIST SP 800-30 Revision 1 Generic Risk Model as shown in Figure F‑2.
Figure F‑2 NIST 800-30 Generic Risk Model
F.1.3.1 Risk Assessment Assumptions¶
Some of the threats and their resulting risks and impacts span several levels. In cases where these risks and impacts have several possible levels, it was assumed that Orvilia would document these using a high-water mark methodology. This assumption of greatest risk then provided the basis for risk mitigation activities. For example, where the threat risk could pose a moderate, high, or very high outcome, the very high outcome was selected, and these very high risks were prioritized for mitigation.
F.1.3.2 Risk Assessment Constraints¶
Information regarding the following were used as input for the constraints for the risk assessment.
threat sources
threat events
vulnerabilities and predisposing conditions
likelihood
impacts
risk assessment and analysis approaches
resources available for the assessment
skills and expertise
Threat Sources
Orvilia’s executives and managers identified two threat sources as possible concerns. Orvilia’s technical staff were provided security control mappings identified within this guide to help them understand the additional security that the example solution could provide to Orvilia as they implemented the example solution.
Additionally, due to the cybersecurity-focused scope of the risk assessment, non-adversarial threat sources (e.g., unintentional hardware, software, or system design and architecture shortcoming threats) were not considered.
As identified in Section F.1.6, Task 2-1: Identify and Characterize Threat Sources of Concern, the risk assessment identified the following threat sources of concern:
Orvilia’s competitors
nation-state actors
Threat Events
Threat events were described at a high level and in general terms within the risk assessment. Similar threat events were combined into a single, broader threat.
Only those threat events that have been previously observed by an authoritative source were considered (e.g., reported as already having occurred by other organizations), drawing primarily from the NIST National Cybersecurity Center of Excellence Mobile Threat Catalogue [B9].
Threat events involving exploitation of vulnerabilities within the cellular network, including a mobile device’s cellular baseband, reasonably exceeded Orvilia’s ability to directly identify and mitigate them and were not further assessed.
Threat events involving exploitation of vulnerabilities in low-level hardware, firmware, and device controllers reasonably exceeded Orvilia’s ability to directly identify and mitigate them and were not further assessed.
Threat events involving exploitation of vulnerabilities in the supply chain reasonably exceeded Orvilia’s ability to directly identify and mitigate them and were not further assessed.
Vulnerabilities and Predisposing Conditions
Mobile device vulnerabilities considered during this risk assessment included those in mobile operating systems and mobile applications, including third-party software libraries.
Vulnerabilities in commonly used noncellular network protocols such as Bluetooth and Wi-Fi were considered.
Vulnerabilities related to a potential Enterprise Mobility Management (EMM) system were considered.
Additional information and determinations were made via Appendix F of NIST SP 800-30 Revision 1.
Likelihood
Likelihood determinations were made via Appendix G of NIST SP 800-30 Revision 1.
Note: The rating of overall likelihood is derived from the Likelihood of Initiation and Likelihood that Threat Events Result from Adverse Impacts using Table G-5 of Appendix G in NIST SP 800-30 Revision 1 [B12]. Ratings of the latter two variables relied heavily on the subjective judgment of Orvilia employees.
Impacts
Impact determinations were made via Appendix H of NIST SP 800-30 Revision 1.
Note: Ratings of impact relied heavily on the subjective judgment of Orvilia employees.
Risk Assessment and Analysis Approaches
This risk assessment focused on identifying an initial set of threats to Orvilia’s mobile deployment.
Approaches for describing threats and their impact were informed by the Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) Framework [B91].
The rating of Risk was derived from both the overall likelihood and level of impact using Table I-2 of Appendix I in NIST SP 800-30 Revision 1 [B12].
Resources Available for the Assessment
Orvilia ensured the appropriate staff with the requisite expertise were available to conduct the assessment within the time allotted.
Orvilia provided funding for the risk analysis staff.
Orvilia staff who conducted the risk assessment had the necessary information systems and software.
Skills and Expertise
Risk assessments were conducted by experts leveraging industry best practices and NIST risk assessment frameworks.
F.1.4 Task 1-4: Risk Assessment Threat, Vulnerability, and Impact Sources¶
Identify the sources of descriptive threat, vulnerability, and impact information to be used in the risk assessment.
Orvilia used the following methods to identify mobile infrastructure threats, vulnerabilities, and impacts.
F.1.4.1 Sources of Threats¶
This risk assessment identified NIST’s Mobile Threat Catalogue (MTC) [B9], along with its associated NIST Interagency Report 8144, Assessing Threats to Mobile Devices & Infrastructure [B92], and MITRE’s ATT&CK Mobile Profile [B93] as credible sources for threat information. Each entry in the MTC contains several pieces of information: an identifier, a category, a high-level description, details on its origin, exploit examples, Common Vulnerabilities and Exposures [B94] examples, possible countermeasures, and academic references.
MITRE’s ATT&CK is a curated knowledge base and model for cyber-adversary behavior. ATT&CK details specific techniques that can be used by cyber adversaries. Each technique entry typically includes a detailed technical description, mitigations, detection analytics, examples of use by malicious actors, and references. The ATT&CK model organizes these techniques into high-level malicious actor tactical objectives, referred to as tactics. A primary use case for ATT&CK is use by organizations to assess the state of their cybersecurity defenses and prioritize deployment of defensive capabilities. The ATT&CK Mobile Profile describes tactics and techniques specific to the mobile environment.
Due to Orvilia’s current use of cloud services, it identified the outputs of the Federal Risk and Authorization Management Program [B95] and associated NIST SP 800-53 security controls as being in scope for this risk assessment.
F.1.4.2 Sources of Vulnerabilities¶
Vulnerabilities are commonly associated with mobile operating systems, device drivers, mobile applications, and third-party libraries. However, vulnerabilities can be present in any level of the mobile technology stack. For up-to-date information regarding vulnerabilities, this risk assessment identified the National Vulnerability Database (NVD) [B96] as a credible source of information. The NVD is the U.S. government repository of standards-based vulnerability management data. Use of NVD was supplemented by review of individual vendor vulnerability disclosures such as those published in the Pixel/Nexus Security Bulletins [B97] for Android, Apple security updates [B98] for iOS, Managing Devices & Corporate Data on iOS [B99], and Android Security Updates [B100] for Android-based Samsung devices.
F.1.4.3 Sources of Impacts¶
This risk assessment identified the scenario described in Section F.1.2 as the primary source of impact determination information. The scenario identified the following systems as being critical to the organization’s mission:
Microsoft Active Directory domain
Microsoft Exchange email server
timekeeping web application
travel support web application
corporately owned mobile devices
An example of a successful attack against a mobile device is one that could be used to glean the credentials for the travel support web application and use them to penetrate the application server. While Orvilia can absorb minimal downtime to the web application, the attacker could use this position to gain a foothold in the Orvilia infrastructure to laterally move to more critical systems in the environment, such as the email server. Compromise of the email server would have high impact, possibly causing serious harm to the organization.
F.1.5 Task 1-5: Risk Assessment Risk Model and Analytic Approach Identification¶
Identify the risk model and analytic approach to be used in the risk assessment.
In this risk assessment, the analytic approach used qualitative (i.e., subjective) ratings of risk (i.e., very low, low, moderate, high, and very high). The approach was primarily threat oriented, as described in Section F.1.6.
F.1.6 Task 2-1: Identify and Characterize Threat Sources of Concern¶
Identify and characterize threat sources of concern, including capability, intent, and targeting characteristics for adversarial threats and range of effects for non-adversarial threats.
Orvilia examined NIST SP 800-30 Revision 1’s Table D-2: Taxonomy of Threat Sources [B12] and identified the following threat sources of concern:
Table F‑1 Threat Sources of Concern
Identifier |
Threat Source |
Description |
Characteristic |
|---|---|---|---|
TS-1 |
Adversarial, Organization, Competitor |
Orvilia’s competitors seek to exploit dependence on cyber resources, specifically the data entrusted by its customers to increase market share. |
Capability, Intent, Targeting |
TS-2 |
Adversarial, Nation-State |
Nation-state actors stealing sensitive government data from unsecured devices and infrastructure |
Capability, Intent, Targeting |
Orvilia produced the following table as output of Task 2-1 to provide relevant inputs to the risk tables. It identifies the threat sources identified in NIST SP 800-30 Revision 1 with the associated risk rating of capability, intent, and targeting score (using the previously mentioned five-point scale: very low, low, moderate, high, and very high).
Orvilia’s assessment found that all threat events could be initiated by both threat sources (Organization/Competitor and Nation-State).
Capability refers to the level of expertise of the malicious actor. Intent refers to the malicious actor’s goal. Targeting refers to the reconnaissance and selection methods performed by the malicious actor.
Table F‑2 Threat Sources Qualitative Scale
Identifier |
Threat Events Relevant to Threat Sources |
In Scope |
Capability |
Intent |
Targeting |
|---|---|---|---|---|---|
TS-1 |
All threat events (Threat Events 1-12) |
Yes |
High |
High |
High |
TS-2 |
All threat events (Threat Events 1-12) |
Yes |
Very High |
Very High |
Very High |
F.1.7 Task 2-2: Identify Potential Threat Events¶
Identify potential threat events, relevance of the events, and the threat sources that could initiate the events.
The threat events used for the example solution are described below. These threat events describe how the mobile devices in Orvilia might be compromised by malicious activities. All of the threat events map to both threat sources identified in Section F.1.6.
Orvilia examined the sample tables in NIST SP 800-30 Revision 1—Tables E-1, E-2, E-3, E-4, and E-5—and analyzed the sources of mobile threats identified in Task 1-4. Using this process, Orvilia leadership identified the following threat events.
F.1.7.1 Threat Event 1—Unauthorized Access to Sensitive Information via a Malicious or Privacy-Intrusive Application¶
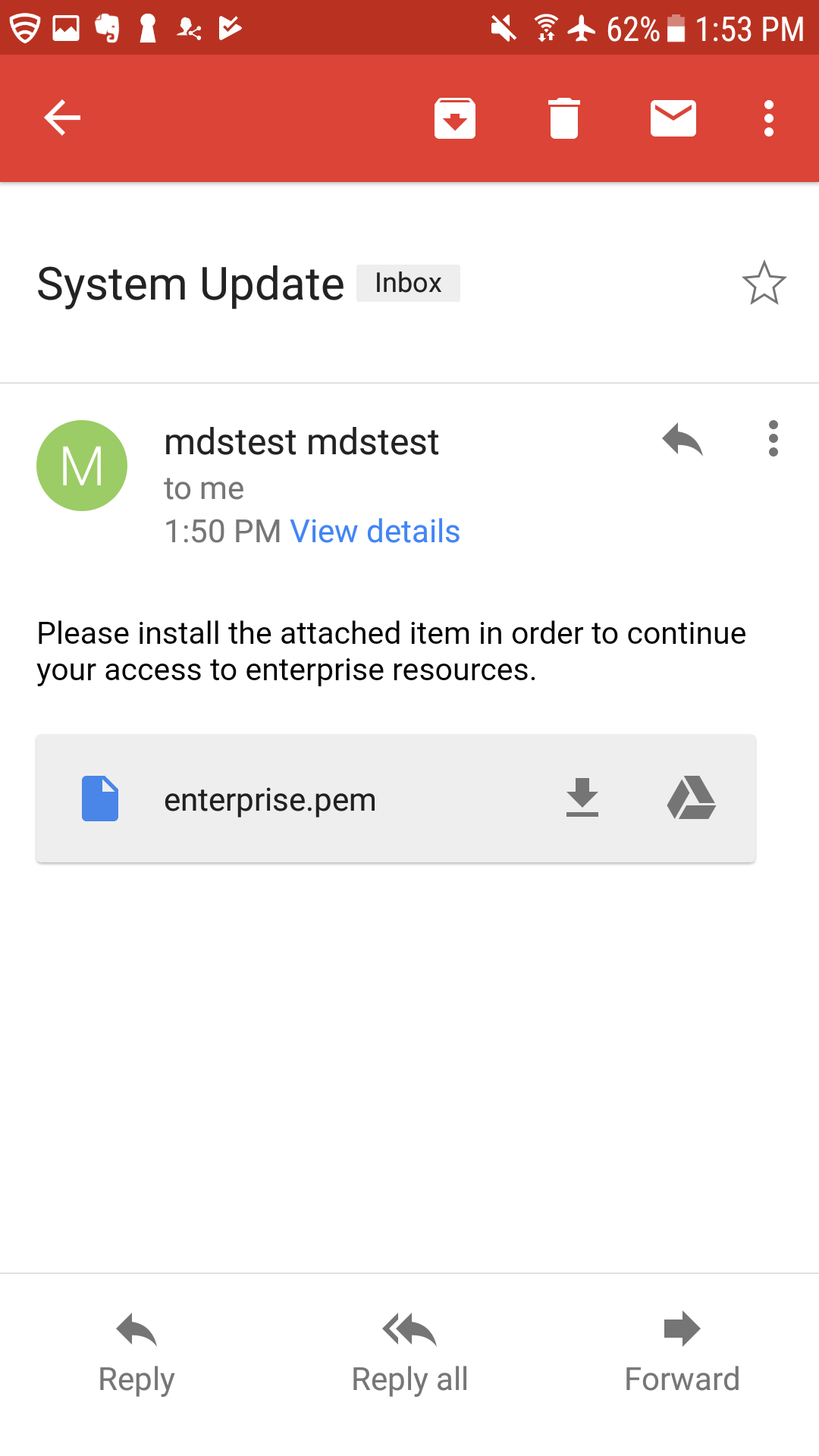
A mobile application can attempt to collect and exfiltrate any information to which it has been granted access. This includes any information generated during use of the application (e.g., user input), user-granted permissions (e.g., contacts, calendar, call logs, camera roll), and general device data available to any application (e.g., International Mobile Equipment Identity, device make and model, serial number). Further, if a malicious application exploits a vulnerability in other applications, the OS, or device firmware to achieve privilege escalation, it may gain unauthorized access to any data stored on or otherwise accessible through the device.
F.1.7.2 Threat Event 2—Theft of Credentials Through an SMS or Email Phishing Campaign¶
Malicious actors may create fraudulent websites that mimic the appearance and behavior of legitimate ones and entice users to authenticate to them by distributing phishing messages over short message service (SMS) or email. Effective use of social engineering techniques such as impersonating an authority figure or creating a sense of urgency may compel users to forgo scrutiny of the message and proceed to authenticate to the fraudulent website; it then captures and stores the user’s credentials before (usually) forwarding them to the legitimate website to allay suspicion.
F.1.7.3 Threat Event 3—Malicious Applications Installed via URLs in SMS or Email Messages¶
Malicious actors may send users SMS or email messages that contain a uniform resource locator (URL) where a malicious application is hosted. Generally, such messages are crafted using social engineering techniques designed to dissuade recipients from scrutinizing the nature of the message, thereby increasing the likelihood they access the URL by using their mobile device. If the URL is accessed, the device will attempt to download and install the application. Effective use of social engineering by the attacker will further compel an otherwise suspicious user to grant any trust required by the developer and all permissions requested by the application. Granting the former facilitates installation of other malicious applications by the same developer, and granting the latter increases the potential for the application to do direct harm.
F.1.7.4 Threat Event 4—Confidentiality and Integrity Loss Due to Exploitation of Known Vulnerability in the OS or Firmware¶
When malware successfully exploits a code execution vulnerability in the mobile OS or device drivers, the delivered code generally executes with elevated privileges and issues commands in the context of the root user or the OS kernel. This may be enough for some to accomplish their goal, but advanced malicious actors will usually attempt to install additional malicious tools and to establish a persistent presence. If successful, the attacker will be able to launch further attacks against the user, the device, or any other systems to which the device connects. As a result, any data stored on, generated by, or accessible to the device at that time—or in the future—may be compromised.
F.1.7.5 Threat Event 5—Violation of Privacy via Misuse of Device Sensors¶
Malicious actors with access (authorized or unauthorized) to device sensors (microphone, camera, gyroscope, Global Positioning System receiver, and radios) can use them to conduct surveillance. It may be directed at the user, as when tracking the device location, or it may be applied more generally, as when recording any nearby sounds. Captured sensor data, such as a recording of an executive meeting, may be immediately useful to a malicious actor. Alternatively, the data may be analyzed in isolation or in combination with other data to yield sensitive information. For example, audio recordings of on-device or proximate activity can be used to probabilistically determine user inputs to touchscreens and keyboards—essentially turning the device into a remote key logger.
F.1.7.6 Threat Event 6—Compromise of the Integrity of the Device or Its Network Communications via Installation of Malicious EMM/MDM, Network, VPN Profiles, or Certificates¶
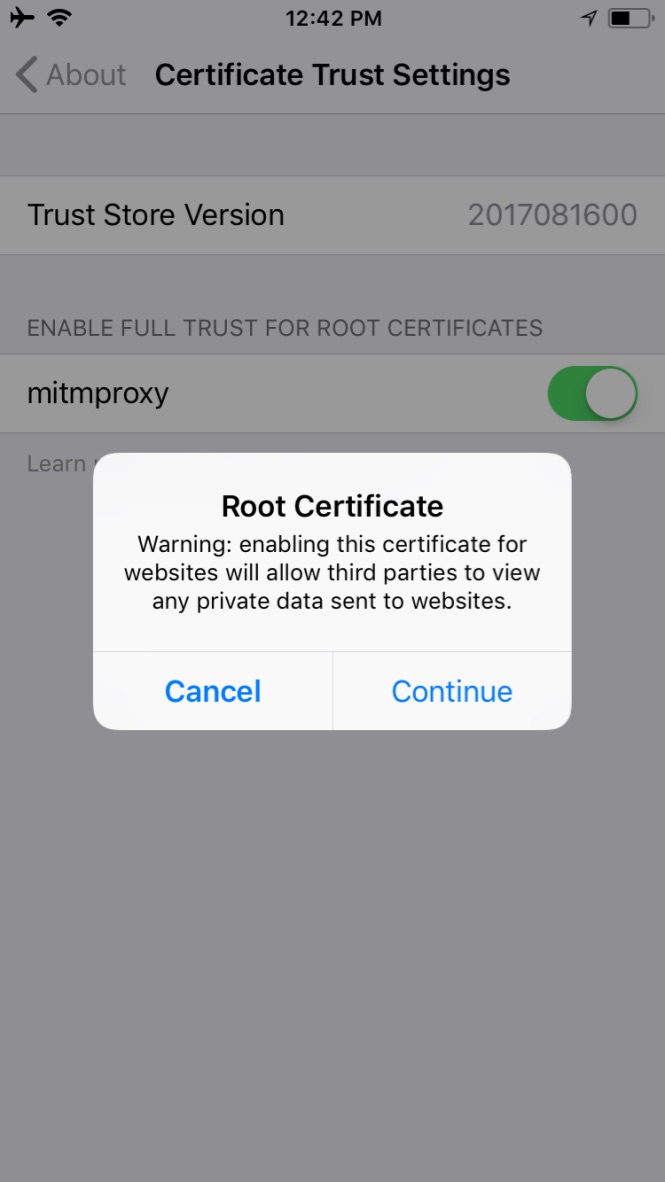
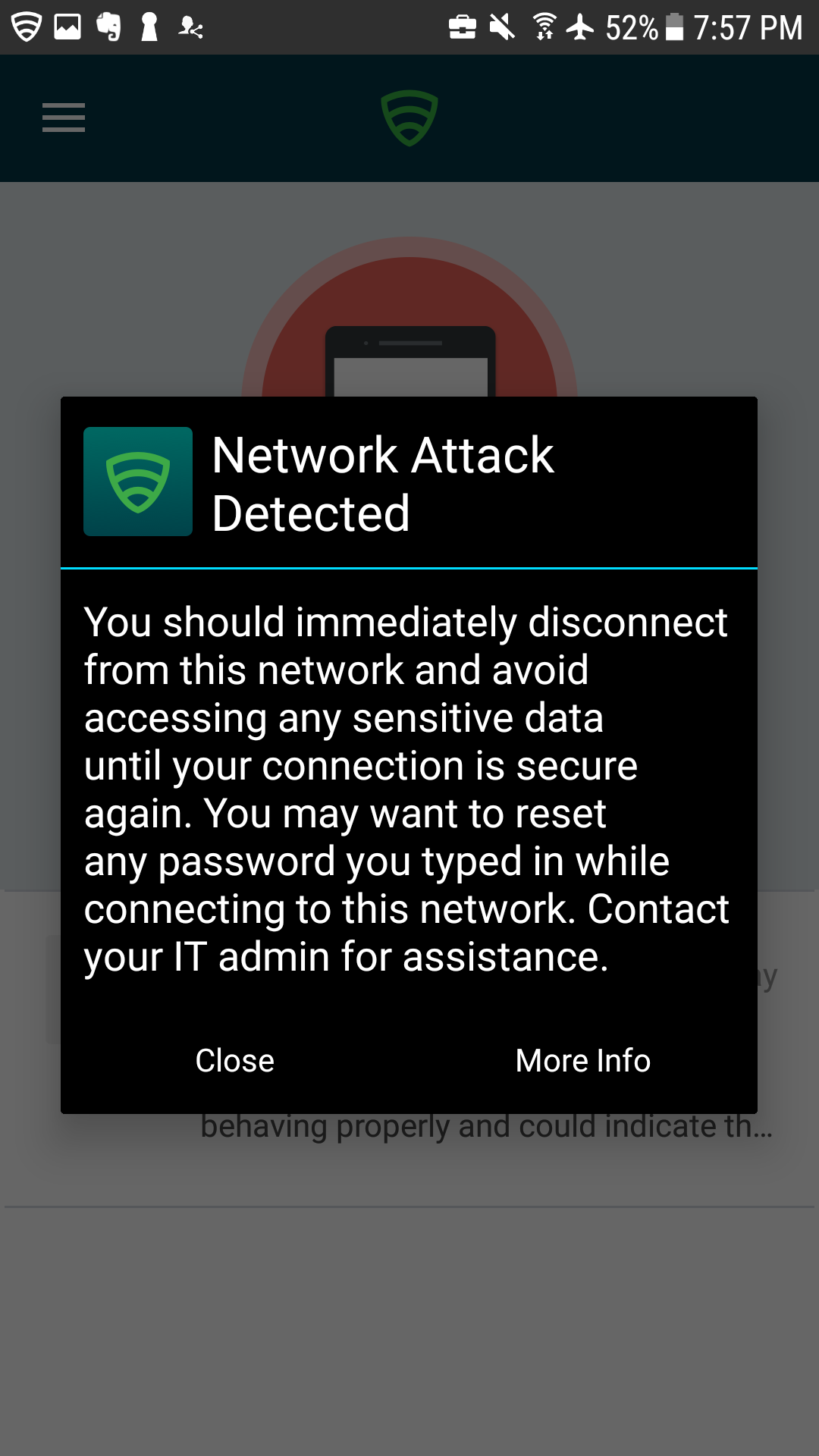
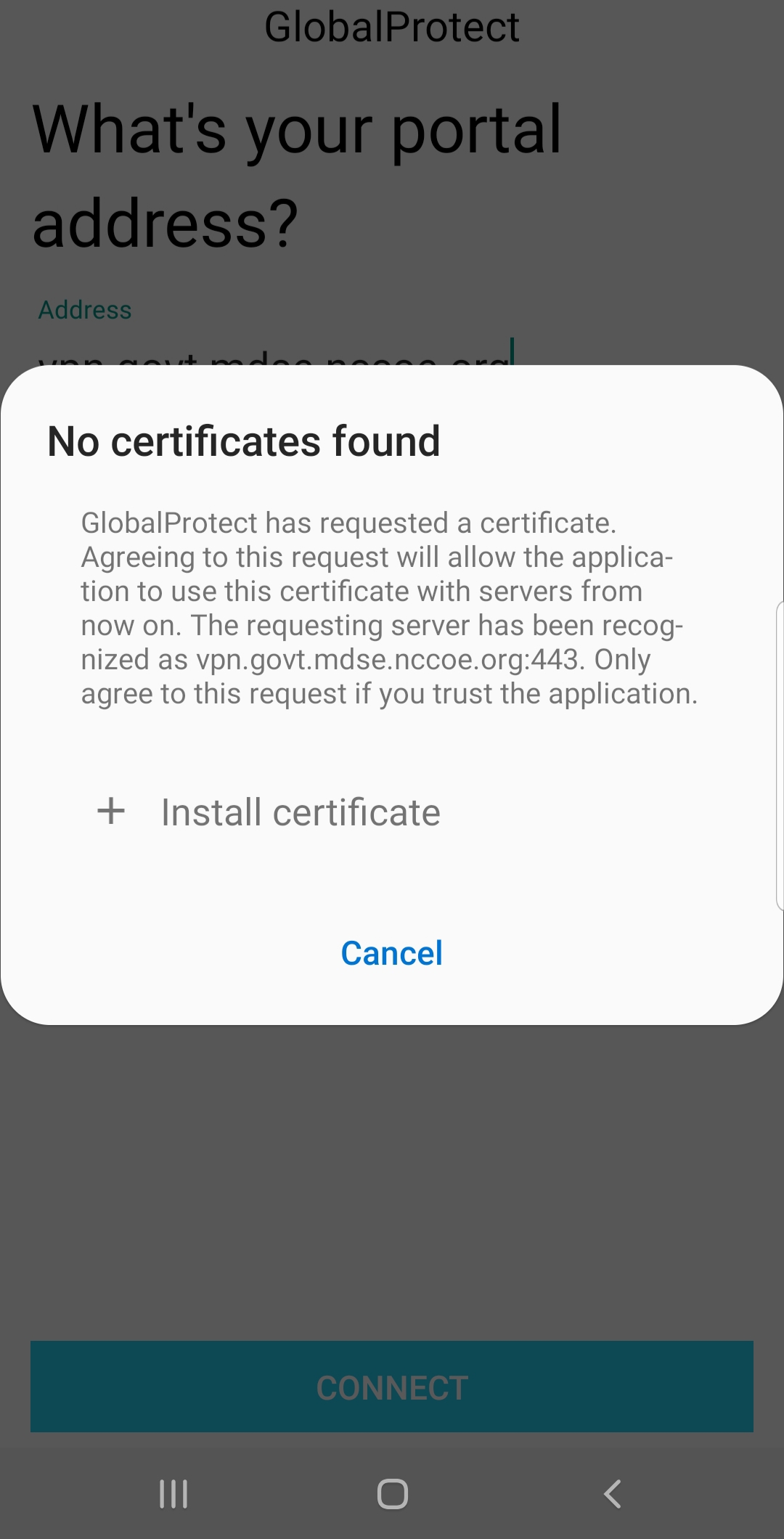
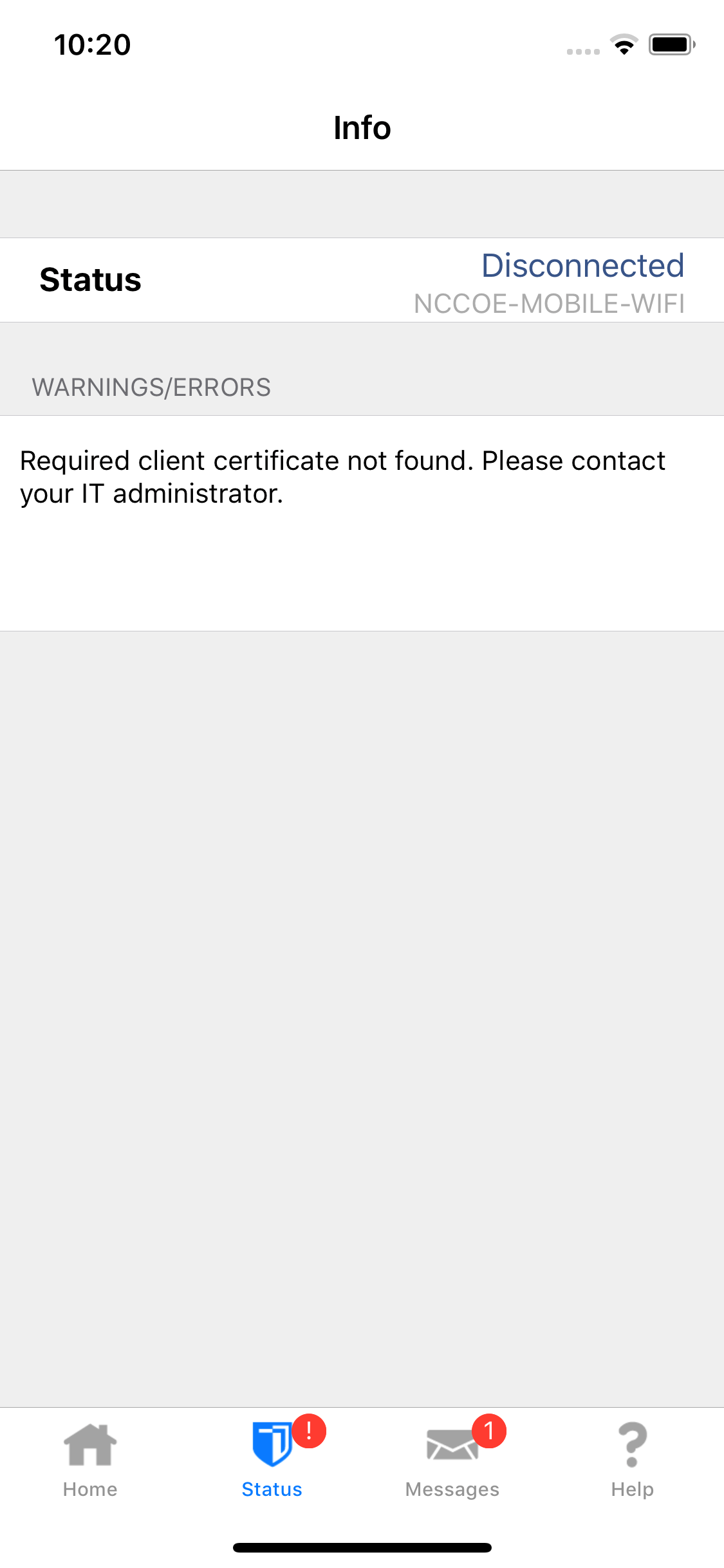
Malicious actors who successfully install an EMM/mobile device management (MDM), network, or virtual private network (VPN) profile or certificate onto a device will gain a measure of additional control over the device or its communications. Presence of an EMM/MDM profile will allow an attacker to misuse existing OS application programming interfaces to send the device a wide variety of commands. This may allow a malicious actor to obtain device information, install or restrict applications, or remotely locate, lock, or wipe the device. Malicious network profiles may allow a malicious actor to automatically compel the device to connect to access points under their control to achieve a person-in-the-middle attack on all outbound connections. Alternatively, VPN profiles assist in the undetected exfiltration of sensitive data by encrypting it, thus hiding it from network scanning tools. Additionally, malicious certificates may allow the malicious actor to compel the device to automatically trust connections to malicious web servers, wireless access points, or installation of applications under their control.
F.1.7.7 Threat Event 7—Loss of Confidentiality of Sensitive Information via Eavesdropping on Unencrypted Device Communications¶
Malicious actors can readily eavesdrop on communication over unencrypted, wireless networks such as public Wi-Fi access points, which are commonly provided by coffee shops and hotels. While a device is connected to such a network, an attacker would gain unauthorized access to any data sent or received by the device for any session not already protected by encryption at either the transport or application layers. Even if the transmitted data were encrypted, an attacker would be privy to the domains, internet protocol addresses, and services (as indicated by port numbers) to which the device connects; such information could be used in future watering hole attacks or person-in-the-middle attacks against the device user. Additionally, visibility into network layer traffic enables a malicious actor to conduct side-channel attacks against its encrypted messages, which can still result in a loss of confidentiality. Further, eavesdropping on unencrypted messages during a handshake to establish an encrypted session with another host or endpoint may facilitate attacks that ultimately compromise the security of the session.
F.1.7.8 Threat Event 8—Compromise of Device Integrity via Observed, Inferred, or Brute-Forced Device Unlock Code¶
A malicious actor may be able to obtain a user’s device unlock code by direct observation, side-channel attacks, or brute-force attacks. Both the first and second can be attempted with at least proximity to the device; only the third technique requires physical access. However, side-channel attacks that infer the unlock code by detecting taps and swipes to the screen can be attempted by applications with access to any peripherals that detect sound or motion (e.g., microphone, gyroscope, or accelerometer). Once the device unlock code has been obtained, a malicious actor with physical access to the device will gain immediate access to any data or functionality not already protected by additional access control mechanisms. Additionally, if the user employs the device unlock code as a credential to any other systems, the malicious actor may further gain unauthorized access to those systems.
F.1.7.9 Threat Event 9—Unauthorized Access to Backend Services via Authentication or Credential Storage Vulnerabilities in Internally Developed Applications¶
If a malicious actor gains unauthorized access to a mobile device, the malicious actor also has access to the data and applications on that mobile device. The mobile device may contain an organization’s in-house applications and can subsequently gain access to sensitive data or backend services. This could result from weaknesses or vulnerabilities present in the authentication or credential storage mechanisms implemented within an in-house application.
F.1.7.10 Threat Event 10—Unauthorized Access of Enterprise Resources from an Unmanaged and Potentially Compromised Device¶
An employee who accesses enterprise resources from an unmanaged mobile device may expose the enterprise to vulnerabilities that may compromise enterprise data. Unmanaged devices do not benefit from security mechanisms deployed by the organization such as mobile threat defense, mobile threat intelligence, application vetting services, and mobile security policies. These unmanaged devices limit an organization’s visibility into the state of a mobile device, including if the device is compromised by a malicious actor. Therefore, users who violate security policies to gain unauthorized access to enterprise resources from such devices risk providing malicious actors with access to sensitive organizational data, services, and systems.
F.1.7.11 Threat Event 11—Loss of Organizational Data Due to a Lost or Stolen Device¶
Due to the nature of the small form factor of mobile devices, they can be misplaced or stolen. A malicious actor who gains physical custody of a device with inadequate security controls may be able to gain unauthorized access to sensitive data or resources accessible to the device.
F.1.7.12 Threat Event 12—Loss of Confidentiality of Organizational Data Due to Its Unauthorized Storage to Non-Organizationally Managed Services¶
If employees violate data management policies by using unmanaged services to store sensitive organizational data, the data will be placed outside organizational control, where the organization can no longer protect its confidentiality, integrity, or availability. Malicious actors who compromise the unauthorized service account or any system hosting that account may gain unauthorized access to the data.
Further, storage of sensitive data in an unmanaged service may subject the user or the organization to prosecution for violation of any applicable laws (e.g., exportation of encryption) and may complicate efforts by the organization to achieve remediation or recovery from any future losses, such as those resulting from the public disclosure of trade secrets.
F.1.8 Task 2-3: Identify Vulnerabilities and Predisposing Conditions¶
Identify vulnerabilities and predisposing conditions that affect the likelihood that threat events of concern result in adverse impacts.
Drawing on the scenario described in Section 3.4.3, there existed vulnerabilities and predisposing conditions that increased the likelihood that identified threat events would result in adverse impacts for Orvilia. Each vulnerability or predisposing condition is listed in the table below along with the corresponding threat events.
The methodology used to rate the level of pervasiveness was qualitative (i.e., subjective) and used a five-point scale.
Very High
High
Moderate
Low
Very Low
Table F‑3 Identify Vulnerabilities and Predisposing Conditions
Vulnerability ID |
Vulnerability or Predisposing Condition |
Resulting Threat Events |
Pervasiveness |
|---|---|---|---|
VULN-1 |
Email and other enterprise resources can be accessed from anywhere, and only username/password authentication is required. |
TE-2, TE-10, TE-11 |
Very High |
VULN-2 |
Public Wi-Fi networks are regularly used by employees for remote connectivity from their corporate mobile devices. |
TE-7 |
Very High |
VULN-3 |
No EMM/MDM deployment exists to enforce and monitor compliance with security-relevant policies on corporate mobile devices. |
TE-1, TE-3, TE-4, TE-5, TE-6, TE-7, TE-8, TE-9, TE-11, TE-12 |
Very High |
Note 1: Ratings of the level of pervasiveness were based on the qualitative scale found in Table F-5 of Appendix F in NIST SP 800-30 Revision 1 [B12].
Note 2: Ratings of pervasiveness indicate that the vulnerabilities apply few (i.e., very low), some (i.e., low), many (i.e., moderate), most (i.e., high), or all (i.e., very high) organizational missions/business functions and processes, or information systems.
F.1.9 Task 2-4: Determine Likelihood of a Threat and the Likelihood of the Threat Having Adverse Impacts¶
Determine the likelihood that threat events of concern result in adverse impacts, considering (i) the characteristics of the threat sources that could initiate the events; (ii) the vulnerabilities/predisposing conditions identified; and (iii) the organizational susceptibility reflecting the safeguards/countermeasures planned or implemented to impede such events.
In the interest of brevity, the threat events of concern identified in Task 2-2 were limited to those presumed to have a foreseeably high likelihood of occurrence.
The methodology used to identify the likelihood of threats of concern was qualitative (i.e., subjective) and used the following five-point scale.
Very High
High
Moderate
Low
Very Low
Table F‑4 Likelihood of Threat Events of Concern
Threat ID |
Likelihood of Threat Event Initiation |
Likelihood of Threat Event Resulting in Adverse Impacts |
Overall Likelihood |
|---|---|---|---|
TE-1 |
High |
Very High |
Very High |
TE-2 |
Very High |
High |
Very High |
TE-3 |
High |
High |
High |
TE-4 |
Moderate |
Very High |
High |
TE-5 |
High |
Very High |
Very High |
TE-6 |
Moderate |
High |
Moderate |
TE-7 |
High |
High |
High |
TE-8 |
Moderate |
High |
High |
TE-9 |
Moderate |
High |
Very High |
TE-10 |
High |
Very High |
Very High |
TE-11 |
Very High |
Very High |
Very High |
TE-12 |
High |
High |
High |
Note 1: For the Likelihood of Threat Event Initiation, the ratings translate as follows: Moderate = malicious actor is somewhat likely to initiate; High = malicious actor is highly likely to initiate; Very high = malicious actor is almost certain to initiate.
Note 2: For the Likelihood of Threat Event Resulting in Adverse Impacts, the ratings translate as follows: Moderate = if the threat is initiated, it is somewhat likely to have adverse impacts; High = if the threat is initiated, it is highly likely to have adverse impacts; Very high = if the threat is initiated, it is almost certain to have adverse impacts.
Note 3: Overall likelihood was calculated based on the qualitative scale found in Table G-3 of Appendix G in NIST SP 800-30 Revision 1 [B12]. It is derived from both the Likelihood of Threat Event Initiation and Likelihood of Threat Event Resulting in Adverse Impacts. Because these scales are not true interval scales, the combined overall ratings do not always reflect a strict mathematical average of the two ratings.
F.1.10 Task 2-5: Determine the Extent of Adverse Impacts¶
Determine the adverse impacts from threat events of concern considering (i) the characteristics of the threat sources that could initiate the events; (ii) the vulnerabilities/predisposing conditions identified; and (iii) the susceptibility reflecting the safeguards/countermeasures planned or implemented to impede such events.
Threat events with a high potential for adverse impacts were then identified in our specific scenario.
The methodology used to determine the extent of adverse impacts was qualitative (i.e., subjective) and used the following five-point scale.
Very High
High
Moderate
Low
Very Low
Table F‑5 Potential Adverse Impacts
Threat ID |
Type of Impact |
Impact Affected Asset |
Maximum Impact |
|---|---|---|---|
TE-1 |
Harm to Operations, Assets, Individuals |
Inability, or limited ability, to perform missions/business functions in the future Damage to or loss of information systems or networks |
High |
TE-2 |
Harm to Operations, Other Organizations |
Inability, or limited ability, to perform missions/business functions in the future |
High |
TE-3 |
Harm to Operations, Assets |
Inability, or limited ability, to perform missions/business functions in the future Damage to or loss of information systems or networks |
High |
TE-4 |
Harm to Operations, Assets |
Inability, or limited ability, to perform missions/business functions in the future Damage to or loss of information systems or networks |
High |
TE-5 |
Harm to Operations, Assets, Individuals |
Inability, or limited ability, to perform missions/business functions in the future Damage to or loss of information systems or networks Loss of personally identifiable information |
High |
TE-6 |
Harm to Operations, Assets, Other Organizations |
Inability, or limited ability, to perform missions/business functions in the future Damage to or loss of information systems or networks Damage to reputation (and hence future or potential trust relationships) |
Very High |
TE-7 |
Harm to Operations, Assets |
Inability, or limited ability, to perform missions/business functions in the future Damage to or loss of information systems or networks |
High |
TE-8 |
Harm to Operations, Assets |
Inability, or limited ability, to perform missions/business functions in the future Damage to or loss of information systems or networks |
High |
TE-9 |
Harm to Operations, Assets |
Inability, or limited ability, to perform missions/business functions in the future Damage to or loss of information systems or networks |
High |
TE-10 |
Harm to Operations, Assets |
Inability, or limited ability, to perform missions/business functions in the future Damage to or loss of information systems or networks |
High |
TE-11 |
Harm to Operations, Assets, Individuals |
Inability, or limited ability, to perform missions/business functions in the future Damage to or loss of information systems or networks Damage to reputation (and hence future or potential trust relationships) Loss of personally identifiable information |
High |
TE-12 |
Harm to Operations, Assets, Other Organizations, Individuals |
Inability, or limited ability, to perform missions/business functions in the future Damage to or loss of information systems or networks Loss of personally identifiable information Damage to reputation (and hence future or potential trust relationships) |
High |
Note 1: Ratings of maximum impact were based on the qualitative scale found in Appendix H, Table H-3 in NIST SP 800-30 Revision 1 [B12].
Note 2: Ratings of maximum impact indicate the threat event could be expected to have negligible (i.e., very low risk), limited (i.e., low), serious (i.e., moderate), severe or catastrophic (i.e., high), or multiple severe or catastrophic effects (i.e., very high).
Note 3: For specific examples of types of impact, see Appendix H of NIST SP 800-30, Revision 1 [B12].
F.1.11 Task 2-6: Determine Risk to Organization¶
Determine the risk to the organization from threat events of concern considering (i) the impact that would result from the events; and (ii) the likelihood of the events occurring.
In the interest of brevity, the threat events of concern identified in Task 2-2 were limited to those presumed to have a foreseeably high likelihood of occurrence and high potential for adverse impact in Orvilia’s specific scenario.
Threat Source Characteristics
This table summarizes the risk assessment findings.
The methodology used to identify risk to organization was qualitative (i.e., subjective) and used the following five-point scale.
Very High
High
Moderate
Low
Very Low
Table F‑6 Summary of Risk Assessment Findings
Threat Event |
Vulnerabilities, Predisposing Conditions |
Overall Likelihood |
Level of Impact |
Risk |
|---|---|---|---|---|
TE-1: Unauthorized access to sensitive information via a malicious or privacy-intrusive application |
VULN-3 |
Very High |
High |
High |
TE-2: Theft of credentials through an SMS or email phishing campaign |
VULN-1 |
Very High |
High |
High |
TE-3: Malicious applications installed via URLs in SMS or email messages |
VULN-3 |
High |
High |
High |
TE-4: Confidentiality and integrity loss due to exploitation of known vulnerability in the OS or firmware |
VULN-3 |
High |
High |
High |
TE-5: Violation of privacy via misuse of device sensors |
VULN-3 |
Very High |
High |
High |
TE-6: Compromise of the integrity of the device or its network communications via installation of malicious EMM/MDM, network, VPN profiles, or certificates |
VULN-3 |
Moderate |
Very High |
High |
TE-7: Loss of confidentiality of sensitive information via eavesdropping on unencrypted device communications |
VULN-2 |
High |
High |
High |
TE-8: Compromise of device integrity via observed, inferred, or brute-forced device unlock code |
VULN-3 |
High |
High |
High |
TE-9: Unauthorized access to backend services via authentication or credential storage vulnerabilities in internally developed applications |
VULN-3 |
Very High |
High |
High |
TE-10: Unauthorized access of enterprise resources from an unmanaged and potentially compromised device |
VULN-1 |
Very High |
High |
High |
TE-11: Loss of organizational data due to a lost or stolen device |
VULN-3 |
Very High |
High |
High |
TE-12: Loss of confidentiality of organizational data due to its unauthorized storage in non-organizationally managed services |
VULN-3 |
High |
High |
High |
Note 1: Risk is stated in qualitative terms based on the scale in Table I-2 of Appendix I in NIST SP 800-30 Revision 1 [B12].
Note 2: The risk rating itself is derived from both the overall likelihood and level of impact using Table I-2 of Appendix I in NIST SP 800-30 Revision 1 [B12]. Because these scales are not true interval scales, the combined overall risk ratings from Table I-2 do not always reflect a strict mathematical average of these two variables. This is demonstrated in the table above in which levels of Moderate weigh more heavily than other ratings.
Note 3: Ratings of risk relate to the probability and level of adverse effect on organizational operations, organizational assets, individuals, other organizations, or the nation. Per NIST SP 800-30 Revision 1, adverse effects (and the associated risks) range from negligible (i.e., very low risk), limited (i.e., low), serious (i.e., moderate), severe or catastrophic (i.e., high), to multiple severe or catastrophic effects (i.e., very high).
Appendix G Privacy Risk Assessment¶
This section describes the privacy risk assessment conducted on Orvilia’s enterprise security architecture. To perform the privacy risk assessment, the National Institute of Standards and Technology (NIST) Privacy Risk Assessment Methodology (PRAM) was used, a tool for analyzing, assessing, and prioritizing privacy risks to help organizations determine how to respond and select appropriate solutions. The PRAM can also serve as a useful communication tool to convey privacy risks within an organization. A blank version of the PRAM is available for download on NIST’s website [B19].
The PRAM uses the privacy risk model and privacy engineering objectives described in NIST Internal Report 8062, An Introduction to Privacy Engineering and Risk Management in Federal Systems [B20], to analyze potential problematic data actions. Data actions are any system operations that process personally identifiable information (PII). Processing can include collection, retention, logging, analysis, generation, transformation or merging, disclosure, transfer, and disposal of PII. A problematic data action is one that could cause an adverse effect for individuals.
The PRAM begins with framing the business objectives for the system, including the organizational needs served, and framing organizational privacy governance, including identification of privacy-related legal obligations and commitments to principles or other organizational policies. Next, create a data map to illustrate the data actions performed by the system and the PII processed by the data actions. These data actions, the PII being processed, and the contextual factors that describe the circumstances surrounding the system’s processing of PII serve as inputs to the risk analysis.
Then, assess the probability that a data action will become problematic for individuals, assess the secondary costs absorbed by the organization from a data action creating a problem for individuals, and use likelihood and impact calculations to determine the total estimated risk per data action. Finally, list potential mitigating technical and policy controls for the identified risks. The output from the PRAM activities resulted in the information contained in Figure G‑1.
Note: The Key within Figure G‑1 includes all data action types (Collection, Retention/Logging, Generation/Transformation, Disclosure/Transfer, and Disposal), but this particular example solution does not cover the Disposal of data in the Privacy Data Mapping exercise.
Figure G‑1 PRAM Data Map for Orvilia’s Enterprise Security Architecture
As an output of the Orvilia PRAM, we identified three broad data actions with the potential to create problems for individuals and relevant mitigations. Some mitigations listed under a particular data action may provide privacy benefits to individuals beyond the scope of that data action. We also identified overarching training and support controls that can help mitigate risks associated with all three of these data actions.
While a security information and event management (SIEM) capability was not used in the reference implementation, SIEMs, as discussed here, can be extremely beneficial in understanding the privacy implications of the mobile device security data being logged, aggregated, and stored.
G.1 Data Action 1: Blocking Access and Wiping Devices¶
Devices that might pose a risk to the organization’s security posture can be blocked from accessing enterprise resources or wiped and reset to factory setting defaults. Options are outlined in the following sections for how this might be accomplished.
G.1.1 Potential Problem for Individuals¶
In a corporate-owned personally-enabled or bring your own device environment, employees are likely to use their devices for both personal and work-related purposes. Therefore, in a system that features the capability to wipe a device entirely, there could be an issue of employees losing personal data—and employees may not even expect this possibility. A hypothetical example would be that an Orvilia employee stores personal pictures on the mobile device issued to them by Orvilia, but these photos are lost when their device is wiped after anomalous activity is detected.
G.1.2 Mitigations¶
Block access instead of wiping devices.
As an alternative to wiping data entirely, devices can be blocked from accessing enterprise resources, for example, until an unapproved application is removed. This temporary blocking of access helps ensure an individual will not lose personal data through a full wipe of a device. Taking this approach may help bring the system’s capabilities into alignment with employees’ expectations about what can happen to their devices, especially if they are unaware that devices can be wiped by administrators—providing for greater predictability in the system.
Related mitigation: If this approach is taken, remediation processes should also be established and communicated to employees. It is important to have a clear remediation process in place to help employees regain access to resources on their devices at the appropriate time. It is equally important to clearly convey this remediation process to employees. A remediation process provides greater manageability in the system supporting employees’ ability to access resources. If well communicated to employees, this also provides greater predictability, as employees will know the steps involved in regaining access.
Enable only selective wiping.
An alternative mitigation option for wiping is to specify the information to be wiped. Performing a selective wipe is an option that only removes enterprise data from the device instead of being a full factory reset. When configured this way, a wipe preserves employees’ personal configurations, applications, and data while removing only the corporate configurations, applications, and data. Within the example solution, this option is available for iOS devices.
Advise employees to back up the personal data maintained on devices.
If device wiping remains an option for administrators, encourage employees to perform regular backups of their personal data to ensure it remains accessible in case of a wipe.
Limit staff with the ability to perform wipes or block access.
Limit staff with the ability to perform a wipe to only those with that responsibility by using role-based access controls. This can help decrease the chances of accidentally removing employee data or blocking access to resources.
G.2 Data Action 2: Employee Monitoring¶
The assessed infrastructure offers Orvilia a number of security capabilities, including reliance on comprehensive monitoring capabilities, as noted in Section 4, Architecture. A significant amount of data relating to employees, their devices, and their activities is collected and analyzed by multiple parties.
G.2.1 Potential Problem for Individuals¶
Employees may not be aware that their interactions with the system are being monitored and may not want this monitoring to occur. Collection and analysis of information might enable Orvilia or other parties to craft a narrative about an employee based on their interactions with the system, which could lead to a power imbalance between Orvilia and the employee and loss of trust in the employer if the employee discovers unanticipated monitoring.
G.2.2 Mitigations¶
Limit staff with ability to review data about employees and their devices.
This may be achieved using role-based access controls and by developing organizational policies to limit how employee data can be used by staff with access to that data. Access can be limited to any dashboard in the system containing data about employees and their devices but is most sensitive within the mobile management dashboard, which is the hub for data about employees, their devices, and threats. Minimizing access to sensitive information can enhance disassociability for employees using the system.
Limit or disable collection of specific data elements.
Conduct a system-specific privacy risk assessment to determine what elements can be limited. Consider the configuration options for intrusive device features, such as location services, application inventory collection, and location-based wake-ups. When collecting application inventory data, ensure that information is gathered only from applications installed from the organization’s corporate application store. While these administrative configurations may help provide for disassociability in the system, there are also some opportunities for employees to limit the data collected.
Organizations may allow their employees to manage certain aspects and configurations of their device. For example, employees may be able to disable location services in their device OS to prevent collection of location data. Each of these controls contributes to reducing the number of attributes collected regarding employees and their mobile devices. This reduction of collected data limits administrators’ ability to associate information with specific individuals.
Dispose of PII.
Disposal of PII after an appropriate retention period can help reduce the risk of entities building profiles of individuals. Disposal can also help bring the system’s data processing into alignment with employees’ expectations and reduce the security risk associated with storing a large volume of PII. Disposal may be particularly important for certain parties in the system that collect a larger volume of data or more sensitive data. Disposal may be achieved using a combination of policy and technical controls. Parties in the system may identify what happens to data, when, and how frequently.
G.3 Data Action 3: Data Sharing Across Parties¶
The infrastructure involves several parties that serve different purposes supporting Orvilia’s security objectives. As a result, there is a significant flow of data about individuals and their devices occurring across various parties. This includes sharing device and application data publicly and with third-party analytics services, and includes sharing device status and usage with third-party analytics.
G.3.1 Potential Problems for Individuals¶
Data transmission about individuals and their devices among a variety of different parties could be confusing for employees who might not know who has access to different information about them. If administrators and co-workers know what colleague is conducting activity on his or her device that triggers security alerts, it could cause employee embarrassment or emotional distress. This information being revealed and associated with specific employees could also lead to stigmatization and even impact Orvilia upper management in their decision-making regarding the employee. Further, clear text transmissions could leave information vulnerable to attackers and the unanticipated release of employee information.
G.3.2 Mitigations¶
Use de-identification techniques.
De-identification of data helps decrease the chances that a third party is aggregating information pertaining to one specific individual. While de-identification can help reduce privacy risk, there are residual risks of reidentification. De-identification techniques may be applied to aggregated data before sharing it with third-party analytics and publicly.
Use encryption.
Encryption decreases the chances of insecure information being transmitted between parties. Organizations should keep this in mind when considering how their enterprise data is transmitted and stored. Mobile security systems share mobile device and application data with one another to optimize efficiency and leverage data to perform security functions. This data may include application inventory and employee name, email address, and phone number. Some systems offer multiple encryption options that allow an organization to choose the encryption level necessary for the type of data that is stored or transmitted.
Limit or disable access to data.
Conduct a system-specific privacy risk assessment to determine how access to data can be limited. Using access controls to limit staff access to compliance information, especially when associated with individuals, is important in preventing association of specific events with particular employees, which could cause embarrassment. Products used by the organization may offer options for restricting the amount of employee information that an administrator can access. These options may include hiding an employee’s username and email address from the administrator console. Mobile application information may also include employee information. Organizations should consider how their mobile and other security systems hide application names, application binary analysis details, network names service set identifier, and network analysis details from administrators.
Limit or disable collection of specific data elements.
Conduct a system-specific privacy risk assessment to determine what elements can be limited. Identifying the employee information collected and determining what data elements are stored assist in assessing the privacy risk of mobile security systems. Organizations should consider the mobile security system’s ability to limit or reduce collection and storage of employee information, such as username, email address, Global Positioning System location, and application data.
Use contracts to limit third-party data processing.
Establish contractual policies to limit data processing by third parties to only the processing that facilitates delivery of security services, and no data processing beyond those explicit purposes.
G.4 Mitigations Applicable Across Various Data Actions¶
Several mitigations provide benefits to employees pertaining to all three data actions identified in the privacy risk assessment. These training and support mitigations can help Orvilia appropriately inform employees about the system and its data processing.
Mitigations:
Provide training to employees about the system, parties involved, data processing, and administrative actions that can be taken.
Training sessions can also highlight any privacy-preserving techniques used, such as for disclosures to third parties. Training should include confirmation from employees that they understand the actions that can be taken on their devices and the consequences—whether this involves blocking access or wiping data. Employees may also be informed of data retention periods and when their data will be disposed of. This can be more effective than sharing a privacy notice, which research has shown that individuals are unlikely to read.
Provide ongoing notifications or reminders about system activity.
This can be achieved using push notifications, similar to those pictured in screenshots in Appendix H, Threat Event 6, to help directly link administrative actions on devices to relevant threats and help employees understand why an action is being taken. Notifications of changes to policies can help increase system predictability by setting employee expectations appropriately with the way the system processes data and the resulting actions.
Provide a support point of contact.
By providing employees with a point of contact in the organization who can respond to inquiries and concerns regarding the system, employees can gain a better understanding of the system’s processing of their data, which enhances predictability.
Appendix H Threat Event Test Information¶
Detailed information and screenshots for some of this practice guide’s threat events and their testing results are provided below.
H.1 Threat Event 1—Unauthorized Access to Sensitive Information via a Malicious or Privacy-Intrusive Application¶
A part of Threat Event 1’s testing conclusions is shown in the following screen capture, where the calendar access permission is being set to a risk score of 10. This allows MobileIron to automatically apply the mobile threat protection high-risk label to the device and quarantine the device until the privacy-intrusive application is removed.
Figure H‑1 Setting a Custom Risk Level in Appthority
H.2 Threat Event 2—Theft of Credentials Through a Short Message Service (SMS) or Email Phishing Campaign¶
Threat Event 2’s outcome is shown in the following screen capture, where PAN-DB is blocking a website manually added to the malicious uniform resource locator (URL) database.
Figure H‑2 PAN-DB Blocked Website
H.3 Threat Event 3—Malicious Applications Installed via URLs in SMS or Email Messages¶
The following screenshots demonstrate enabling the Unknown Sources toggle and installing an application through a link in an email message.
Figure H‑3 Lock Screen and Security |
Figure H‑4 Phishing Email on Android |
Figure H‑5 depicts the iOS test activity of receiving an email containing a link to an application from a non-Apple App Store source.
Figure H‑5 Phishing Email on iOS |
Figure H‑6 Untrusted Developer Warning |
After the application is installed, an untrusted developer notice appears as shown in Figure H‑6 when the user attempts to launch the application.
Figure H‑7 shows Lookoutʼs ability to detect application signing certificates that have been trusted on a device by the user to execute applications from sources other than Appleʼs App Store.
Figure H‑7 Application Signing Certificates
The following screenshots depict an attempt to install and run the unauthorized demo application on an iOS device with the allowEnterpriseAppTrust policy
restriction set to false by an Enterprise Mobility Management (EMM) system. The user is not able to trust the developer when the policy restriction is active,
and hence the application will not run.
Figure H‑8 Restriction Setting Modification Screen
Figure H‑9 Unable to Trust Developer
Android Device Testing
On Android devices, applications cannot be installed from sources other than the Google Play Store unless the Unknown Sources setting is enabled in the deviceʼs security settings. Lookout can identify when the Unknown Sources setting has been enabled and can communicate this information to MobileIron to enable automated response actions, such as blocking device access to enterprise resources until the situation is resolved. However, even if Unknown Sources is disabled, it is possible that the setting was previously enabled and that unauthorized applications were installed at that time.
Figure H‑10 shows Lookoutʼs ability to detect Android devices with Unknown Sources enabled.
Figure H‑10 Unknown Sources Detection
H.4 Threat Event 4—Confidentiality and Integrity Loss due to Exploitation of Known Vulnerability in the Operating System or Firmware¶
Figure H‑11 demonstrates Lookoutʼs ability to identify known vulnerabilities to which unpatched iOS and Android devices are susceptible. Figure H‑12 shows the patch level of the device.
Figure H‑11 Vulnerability Identification
Figure H‑12 Patch Level Display
H.5 Threat Event 5—Violation of Privacy via Misuse of Device Sensors¶
The following screenshot depicts a Kryptowire application analysis report and the reported permissions that this application was requesting.
Figure H‑13 Kryptowire Analysis Report
H.6 Threat Event 6—Compromise of the Integrity of the Device or Its Network Communications via Installation of Malicious EMM/Mobile Device Management, Network, Virtual Private Network (VPN) Profiles, or Certificates¶
The configuration profile used for configuring and testing Threat Event 6 is shown in Figure H‑14.
Figure H‑14 Configuration Profile Example
Figure H‑15 shows the email containing a malicious device configuration profile, and Figure H‑16 shows the warning displayed to the user when attempting to mark the malicious certificate as a trusted root.
Figure H‑15 Configuration Profile Phishing Email |
Figure H‑16 Root Certificate Authority Enablement Warning |
Figure H‑17 Reversed Web Page
Browse to a hypertext transfer protocol secure (https) website from the mobile device and observe whether the content has been reversed. Figure H‑17 illustrates that the person-in-the-middle attack on a Transport Layer Security-protected connection was successful.
The following screenshots demonstrate a person-in-the-middle attack on Android.
Figure H‑18 Certificate Phishing Email |
Figure H‑19 Reversed Web Page |
Person-in-the-middle attack is detected by Lookout as shown in Figure H‑20.
Figure H‑20 Network Attack Detected
H.7 Threat Event 7—Loss of Confidentiality of Sensitive Information via Eavesdropping on Unencrypted Device Communications¶
The following screenshot shows Appthority detecting an application sending data unencrypted.
Figure H‑21 Unencrypted Data Transfer
H.8 Threat Event 8—Compromise of Device Integrity via Observed, Inferred, or Brute-Forced Device Unlock Code¶
MobileIron applies a policy to the devices to enforce a mandatory personal identification number and device-wipe capability. Lookout reports devices that have the lock screen disabled.
Figure H‑22 Lock Screen Disabled Detection Notice
H.9 Threat Event 9—Unauthorized Access to Backend Services via Authentication or Credential Storage Vulnerabilities in Internally Developed Applications¶
As shown in Figure H‑23, Appthority recognized that an application used hard-coded credentials. The application’s use of hard-coded credentials could introduce vulnerabilities if the hard-coded credentials were used for access to enterprise resources by unauthorized entities or for unauthorized actions.
Figure H‑23 Hard-Coded Credentials
H.10 Threat Event 10—Unauthorized Access of Enterprise Resources from an Unmanaged and Potentially Compromised Device¶
The following two screenshots depict the inability to connect to the GlobalProtect VPN without the proper client certificates, obtainable only through enrolling the device in MobileIron.
Figure H‑24 No Certificates Found on Android |
Figure H‑25 No Certificates Found on iOS |
H.11 Threat Event 11—Loss of Organizational Data Due to a Lost or Stolen Device¶
This screenshot depicts the final warning before Android factory-resets the device. In the event the device was stolen, all corporate data would be removed from the device after one more failed unlock attempt, thwarting the malicious actor’s goal.
Figure H‑26 Android Device Wipe Warning
H.12 Threat Event 12—Loss of Confidentiality of Organizational Data Due to Its Unauthorized Storage in Non-Organizationally Managed Services¶
The following screenshot shows one of the data loss prevention configuration options in MobileIron for iOS.
Figure H‑27 Disallowing Screenshots and Screen Recording
Appendix I Example Security Control Map¶
Table I‑1 lists the technologies used in this project and provides a mapping among the generic application term, the specific product used, the security control(s) the product provides, and a mapping to the relevant National Institute of Standards and Technology (NIST) Special Publication (SP) 800-181, National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework Work Roles. From left to right, the columns in the table describe:
Specific product used: vendor product used by the example solution
How the component functions in the build: capability the component provides in the example solution. This is mapped to the general mobile technology component term.
Applicable Cybersecurity Framework Subcategories: applicable Cybersecurity Framework Subcategory(s) that the component is providing in the example solution
Applicable NIST controls: the NIST SP 800-53 Revision 4 controls that the component provided in the example solution
ISO/IEC 27001:2013: International Organization for Standardization (ISO), International Electrotechnical Commission (IEC) 27001:2013 mapping that the component provides in the example solution
CIS 6: Center for Internet Security (CIS) version 6 controls mapping that the component provides in the example solution
NIST SP 800-181, NICE Framework Work Roles: NICE Framework work role(s) that could be used to manage this component’s use in the example solution. This mapping provides information on the workforce members who would be engaged in this part of the example solution’s support.
Table I‑1 Example Solution’s Cybersecurity Standards and Best Practices Mapping
Specific product used |
How the component functions in the build |
Applicable Cybersecurity Framework Version 1.1 Subcategories |
Applicable NIST SP 800-53 Revision 4 Controls |
ISO/IEC 27001:2013 |
CIS 6 |
NIST SP 800-181 NICE Framework Work Roles |
|---|---|---|---|---|---|---|
Mobile Threat Intelligence |
||||||
Appthority Cloud Service |
Mobile Threat Intelligence |
ID.RA-1—Asset vulnerabilities are identified and documented |
Security Assessment and Authorization CA-2, CA-7, CA-8 Risk Assessment RA-3, RA-5 System and Services Acquisition SA-5, SA-11 System and Information Integrity SI-2, SI-4, SI-5 |
A.12.6.1 Control of Technical vulnerabilities A.18.2.3 Technical Compliance Review |
CSC 4 Continuous Vulnerability Assessment and Remediation |
SP-RSK-002 Security Control Assessor SP-ARC-002 Security Architect OM-ANA-001 Systems Security Analyst PR-VAM-001 Vulnerability Assessment Analyst PR-CDA-001 Cyber Defense Analyst OV-MGT-001 Information Systems Security Manager |
ID.RA-3—Threats, both internal and external, are identified and documented |
Risk Assessment RA-3 System and Information Integrity SI-5 Insider Threat Program PM-12, PM-16 |
Clause 6.1.2 Information Risk Assessment Process |
CSC 4 Continuous Vulnerability Assessment and Remediation |
SP-RSK-002 Security Control Assessor PR-CDA-001 Cyber Defense Analyst OV-SPP-001 Cyber Workforce Developer and Manager OV-TEA-001 Cyber Instructional Curriculum Developer AN-TWA-001 Threat/Warning Analyst PR-VAM-001 Vulnerability Assessment Analyst OV-MGT-001 Information Systems Security Manager |
||
DE.CM-4— Malicious code is detected |
System and Information Integrity SI-3, SI-8 |
A.12.2.1 Controls Against Malware |
CSC 4 Continuous Vulnerability Assessment and Remediation CSC 7 Email and Web Browser Protections CSC 8 Malware Defenses CSC 12 Boundary Defense |
PR-VAM-001 Vulnerability Assessment Analyst PR-CIR-001 Cyber Defense Incident Responder PR-CDA-001 Cyber Defense Analyst OM-NET-001 Network Operations Specialist |
||
DE.CM-5—Unauthorize d mobile code is detected |
Mobile Code SC-18, SC-44 System and Information Integrity SI-4 |
A.12.5.1 Installation of Software on Operational Systems A.12.6.2 Restrictions on Software Installation |
CSC 7 Email and Web Browser Protections CSC 8 Malware Defenses |
PR-CDA-001 Cyber Defense Analyst OM-NET-001 Network Operations Specialist |
||
Mobile Application Vetting Service |
||||||
Kryptowire Cloud Service |
Application Vetting |
ID.RA-1—Asset vulnerabilities are identified and documented |
Security Assessment and Authorization CA-2, CA-7, CA-8 Risk Assessment RA-3, RA-5 System and Services Acquisition SA-5, SA-11 System and Information Integrity SI-2, SI-4, SI-5 |
A.12.6.1 Control of Technical vulnerabilities A.18.2.3 Technical Compliance Review |
CSC 4 Continuous Vulnerability Assessment and Remediation |
SP-RSK-002 Security Control Assessor SP-ARC-002 Security Architect OM-ANA-001 Systems Security Analyst PR-VAM-001 Vulnerability Assessment Analyst PR-CDA-001 Cyber Defense Analyst OV-MGT-001 Information Systems Security Manager |
ID.RA-3—Threats, both internal and external, are identified and documented |
Risk Assessment RA-3 System and Information Integrity SI-5 Insider Threat Program PM-12, PM-16 |
Clause 6.1.2 Information Risk Assessment Process |
CSC 4 Continuous Vulnerability Assessment and Remediation |
SP-RSK-002 Security Control Assessor OM-ANA-001 Systems Security Analyst OV-SPP-001 Cyber Workforce Developer and Manager OV-TEA-001 Cyber Instructional Curriculum Developer AN-TWA-001 Threat/Warning Analyst PR-VAM-001 Vulnerability Assessment Analyst PR-CDA-001 Cyber Defense Analyst OV-MGT-001 Information Systems Security Manager |
||
DE.CM-4—Malicious code is detected |
System and Information Integrity SI-3, SI-8 |
A.12.2.1 Controls Against Malware |
CSC 4 Continuous Vulnerability Assessment and Remediation CSC 7 Email and Web Browser Protections CSC 8 Malware Defenses CSC 12 Boundary Defense |
PR-CIR-001 Cyber Defense Incident Responder PR-CDA-001 Cyber Defense Analyst PR-VAM-001 Vulnerability Assessment Analyst OM-NET-001 Network Operations Specialist |
||
DE.CM-5—Unauthorized mobile code is detected |
Mobile Code SC-18, SC-44 System and Information Integrity SI-4 |
A.12.5.1 Installation of Software on Operational Systems A.12.6.2 Restrictions on Software Installation |
CSC 7 Email and Web Browser Protections CSC 8 Malware Defenses |
PR-CDA-001 Cyber Defense Analyst OM-NET-001 Network Operations Specialist |
||
Mobile Threat Defense |
||||||
Lookout Cloud Service/ Lookout Agent Version 5.10.0.142 (iOS), 5.9.0.420 (Android) |
Mobile Threat Defense/Endpoint Security |
PR.AC-5—Network integrity is protected (e.g., network segregation, network segmentation) |
Access Control AC-4, AC-10 System and Communications Protection SC-7 |
A.13.1.1 Network Controls A.13.1.3 Segregation in Networks A.13.2.1 Information Transfer Policies and Procedures A.14.1.2 Securing Application Services on Public Networks A.14.1.3 Protecting Application Services Transactions |
CSC 9 Imitation and Control of Network Ports, Protocols, and Services CSC 14 Controlled Access Based on the Need to Know CSC 15 Wireless Access Control CSC 18 Application Software Security |
OM-ADM-001 System Administrator OV-SPP-002 Cyber Policy and Strategy Planner PR-CDA-001 Cyber Defense Analyst OM-NET-001 Network Operations Specialist |
PR.PT-4— Communications and control networks are protected |
Access Control AC-4, AC-17, AC-18 Contingency Planning Policy and Procedures CP-8 System and Communications Protection SC-7, SC-19, SC-20, SC-21, SC-22, SC-23, SC-24, SC-25, SC-29, SC-32, SC-36, SC-37, SC-38, SC-39, SC-40, SC-41, SC-43 |
A.13.1.1 Network Controls A.13.1.3 Segregation in Networks A.14.1.3 Protecting Application Services Transactions |
CSC 8 Malware Defenses CSC 12 Boundary Defense CSC 15 Wireless Access Control |
OM-ADM-001 System Administrator OV-SPP-002 Cyber Policy and Strategy Planner OV-MGT-002 Communications Security (COMSEC) Manager SP-ARC-0001 Enterprise Architect PR-CDA-001 Cyber Defense Analyst SP-ARC-002 Security Architect OM-NET-001 Network Operations Specialist |
||
DE.CM-5— Unauthorized mobile code is detected |
Mobile Code SC-18, SC-44 System and Information Integrity SI-4 |
A.12.5.1 Installation of Software on Operational Systems A.12.6.2 Restrictions on Software Installation |
CSC 7 Email and Web Browser Protections CSC 8 Malware Defenses |
PR-CDA-001 Cyber Defense Analyst OM-NET-001 Network Operations Specialist |
||
Enterprise Mobility Management |
||||||
MobileIron Core Version 9.7.0.1 |
Enterprise Mobility Management |
ID.AM-1—Physical devices and systems within the organization are inventoried |
Information System Component Inventory CM-8 Information System Inventory PM-5 |
A.8.1.1 Inventory of Assets A.8.1.2 Ownership of Assets |
CSC 1 Inventory of Authorized and Unauthorized Devices |
OM-STS-001 Technical Support Specialist OM-ADM-001 System Administrator |
PR.AC-1—Identities and credentials are issued, managed, verified, revoked, and audited for authorized devices, users, and processes |
Access Control AC-1, AC-2 Identification and Authentication IA-1, IA-2, IA-3, IA-4, IA-5, IA-6, IA-7, IA-8, IA-9, IA-10, IA-11 |
A.9.2.1 User Registration and De-Registration A.9.2.2 User Access Provisioning A.9.2.3 Management of Privileged Access Rights A.9.2.4 Management of Secret Authentication Information of Users A.9.2.6 Removal or Adjustment of Access Rights A.9.3.1 Use of Secret Authentication Information A.9.4.2 Secure Log-On Procedures A.9.4.3 Password Management System |
CSC 1 Inventory of Authorized and Unauthorized Devices CSC 5 Controlled Use of Administrative Privileges CSC 15 Wireless Access Control CSC 16 Account Monitoring and Control |
OV-SPP-002 Cyber Policy and Strategy Planner OM-ADM-001 System Administrator OV-MGT-002 Communications Security (COMSEC) Manager OM-STS-001 Technical Support Specialist OM-ANA-001 Systems Security Analyst PR-CDA-001 Cyber Defense Analyst |
||
PR.AC-6—Identities are proofed and bound to credentials and asserted in interactions |
Access Control AC-1, AC-2, AC-3, AC-16, AC-19, AC-24 Identification and Authentication IA-1, IA-2, IA-4, IA-5, IA-8 Physical and Environmental Protection PE-2 Personnel Security PS-3 |
A.7.1.1 Screening A.9.2.1 User Registration and De-Registration |
CSC 16 Account Monitoring and Control |
OV-SPP-002 Cyber Policy and Strategy Planner OV-MGT-002 Communications Security (COMSEC) Manager OM-ADM-001 System Administrator |
||
PR.IP-1—A baseline configuration of information technology/industri al control systems is created and maintained, incorporating security principles (e.g., concept of least functionality) |
Information System Component Inventory CM-2, CM-3, CM-4, CM-5, CM-6, CM-7, CM-9 System and Services Acquisition SA-10 |
A.12.1.2 Change Management A.12.5.1 Installation of Software on Operational Systems A.12.6.2 Restrictions on Software Installation A.14.2.2 System Change Control Procedures A.14.2.3 Technical Review of Applications After Operating Platform Changes A.14.2.4 Restrictions on Changes to Software Packages |
CSC 3 Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers CSC 9 Limitation and Control of Network Ports, Protocols, and Services CSC 11 Secure Configurations for Network Devices Such as Firewalls, Routers, and Switches |
SP-ARC-002 Security Architect OV-SPP-002 Cyber Policy and Strategy Planner SP-SYS-001 Information Systems Security Developer OM-ADM-001 System Administrator PR-VAM-001 Vulnerability Assessment Analyst OM-NET-001 Network Operations Specialist OV-MGT-001 Information Systems Security Manager OM-STS-001 Technical Support Specialist |
||
MobileIron Agent Version 11.0.1A (iOS), 10.2.1.1.3R (Android) |
EMM/Endpoint Agent |
PR.DS-6—Integrity- checking mechanisms are used to verify software, firmware, and information integrity |
System and Communications Protection SC-1 System and Information Integrity SI-7 |
A.12.2.1 Controls Against Malware A.12.5.1 Installation of Software on Operational Systems A.14.1.2 Securing Application Services on Public Networks A.14.1.3 Protecting Application Services Transactions A.14.2.4 Restrictions on Changes to Software Packages |
CSC 2 Inventory of Authorized and Unauthorized Software CSC 3 Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers |
OV-SPP-002 Cyber Policy and Strategy Planner SP-ARC-0001 Enterprise Architect OV-MGT-001 Information Systems Security Manager OM-ADM-001 System Administrator OM-STS-001 Technical Support Specialist |
Trusted Execution Environment |
||||||
Qualcomm (Version is mobile device dependent) |
Trusted Execution Environment |
PR.DS-1—Data at rest is protected |
Media Downgrading MP-8 System and Communications Protection SC-12, SC-28 |
A.8.2.3 Handling of Assets |
CSC 13 Data Protection CSC 14 Controlled Access Based on the Need to Know |
OV-SPP-002 Cyber Policy and Strategy Planner PR-INF-001 Cyber Defense Infrastructure Support Specialist OV-LGA-002 Privacy Officer/Privacy Compliance Manager OV-MGT-002 COMSEC Manager OM-NET-001 Network Operations Specialist OM-ANA-001 Systems Security Analyst |
PR.DS-6—Integrity- checking mechanisms are used to verify software, firmware, and information integrity |
System and Communications Protection SC-16 System and Information Integrity SI-7 |
A.12.2.1 Controls Against Malware A.12.5.1 Installation of Software on Operational Systems A.14.1.2 Securing Application Services on Public Networks A.14.1.3 Protecting Application Services Transactions A.14.2.4 Restrictions on Changes to Software Packages |
CSC 2 Inventory of Authorized and Unauthorized Software CSC 3 Secure Configurations for Hardware and Software on Mobile |
OV-SPP-002 Cyber Policy and Strategy Planner PR-CDA-001 Cyber Defense Analyst SP-ARC-0001 Enterprise Architect OV-MGT-001 Information Systems Security Manager OM-STS-001 Technical Support Specialist OM-ADM-001 System Administrator |
||
PR.DS-8—Integrity- checking mechanisms are used to verify hardware integrity |
Developer Configuration Management SA-10 System and Information Integrity SI-7 |
A.11.2.4 Equipment Maintenance |
Not applicable |
OM-ADM-001 System Administrator SP-ARC-0001 Enterprise Architect |
||
DE.CM-4—Malicious code is detected |
System and Information Integrity SI-3, SI-8 |
A.12.2.1 Controls Against Malware |
CSC 5 Controlled Use of Administrative Privileges CSC 7 Email and Web Browser Protections CSC 14 Controlled Access Based on the Need to Know CSC 16 Account Monitoring and Control |
PR-CDA-001 Cyber Defense Analyst PR-INF-001 Cyber Defense Infrastructure Support Specialist PR-VAM-001 Vulnerability Assessment Analyst OM-NET-001 Network Operations Specialist PR-CDA-001 Cyber Defense Analyst |
||
Virtual Private Network |
||||||
Palo Alto Networks PA-220 Version 8.1.1 |
Virtual Private Network |
PR.AC-3—Remote access is managed |
Access Control AC-1, AC-17, AC-19, AC-20 System and Communications Protection SC-15 |
A.6.2.1 Mobile Device Policy A.6.2.2 Teleworking A.11.2.6 Security of Equipment and Assets Off-Premises A.13.1.1 Network Controls A.13.2.1 Information Transfer Policies and Procedures |
CSC 12 Boundary Defense |
OV-SPP-002 Cyber Policy and Strategy Planner OV-MGT-002 Communications Security (COMSEC) Manager OM-NET-001 Network Operations Specialist |
PR.AC-5—Network integrity is protected (e.g., network segregation, network segmentation) |
Access Control AC-4, AC-10 System and Communications Protection SC-7 |
A.13.1.1 Network Controls A.13.1.3 Segregation in Networks A.13.2.1 Information Transfer Policies and Procedures A.14.1.2 Securing Application Services on Public Networks A.14.1.3 Protecting Application Services Transactions |
CSC 9 Limitation and Control of Network Ports, Protocols, and Services CSC 14 Controlled Access Based on the Need to Know CSC 15 Wireless Access Control CSC 18 Application Software Security |
PR-CDA-001 Cyber Defense Analyst OM-ADM-001 System Administrator OM-NET-001 Network Operations Specialist |
||
PR.AC-6—Identities are proofed and bound to credentials and asserted in interactions |
Access Control AC-1, AC-2, AC-3, AC-16, AC-19, AC-24 Identification and Authentication IA-1, IA-2, IA-4, IA-5, IA-8 Physical and Environmental Protection PE-2, PS-3 |
A.7.1.1 Screening A.9.2.1 User Registration and De-Registration |
CSC 16 Account Monitoring and Control |
OV-SPP-002 Cyber Policy and Strategy Planner OV-MGT-002 Communications Security (COMSEC) Manager OM-ADM-001 System Administrator |
||
PR.DS-2—Data in transit is protected |
System and Communications Protection SC-8, SC-11, SC-12 |
A.8.2.3 Handling of Assets A.13.1.1 Network Controls A.13.2.1 Information Transfer Policies and Procedures A.13.2.3 Electronic Messaging A.14.1.2 Securing Application Services on Public Networks A.14.1.3 Protecting Application Services Transactions |
CSC 13 Data Protection CSC 14 Controlled Access Based on the Need to Know |
OV-SPP-002 Cyber Policy and Strategy Planner OV-MGT-002 Communications Security (COMSEC) Manager OV-LGA-002 Privacy Officer/Privacy Compliance Manager OM-NET-001 Network Operations Specialist |
||
PR.PT-4— Communications and control networks are protected |
Access Control AC-4, AC-17, AC-18 Contingency Planning CP-8 System and Communications Protection SC-7, SC-19, SC-20, SC-21, SC-22, SC-23, SC-24, SC-25, SC-29, SC-32, SC-36, SC-37, SC-38, SC-39, SC-40, SC-41, SC-43 |
A.13.1.1 Network Controls A.13.2.1 Information Transfer Policies and Procedures A.14.1.3 Protecting Application Services Transactions |
CSC 8 Malware Defenses CSC 12 Boundary Defense CSC 15 Wireless Access Control |
PR-INF-001 Cyber Defense Infrastructure Support Specialist OV-SPP-002 Cyber Policy and Strategy Planner PR-CDA-001 Cyber Defense Analyst OM-NET-001 Network Operations Specialist |
||