Securing Wireless Infusion Pumps in Healthcare Delivery Organizations
Visualization of NIST SP 1800-8





Healthcare providers rely on network-connected devices, such as wireless infusion pumps, to treat patients more safely and efficiently.




But if not secured, these devices are vulnerable to tampering, intentional or not, and expose your organization and your patients to significant risk.




Is your hospital at risk?
The NCCoE has developed a free, comprehensive guide to help healthcare providers understand the risks associated with connected medical devices and guard against those risks.
While the NCCoE practice guide focuses on wireless infusion pumps, the cybersecurity principles and solution discussed can be applied to any network-connected medical device within a healthcare setting.
Find out more about the risks of unsecured network-connected medical devices.
Can't watch the video? Read our two-page fact sheet instead.

This practice guide explains which security controls and technologies can help secure wireless infusion pumps and other medical devices. The NCCoE recommends a risk-based approach.
Risk represents the potential for loss, damage or destruction of an asset, like a wireless infusion pump, as a result of a threat exploiting a vulnerability.
An effective risk assessment includes:
assets and their status
vulnerabilities and threats
users and systems and the level of access for each
For a comprehensive look at how to conduct a risk assessment, please refer to NIST SP 800-30, Guide for Conducting Risk Assessments.
NIST SP 1800-8 identified the following concerns in its risk assessment of a typical healthcare delivery organization.
For the complete risk assessment, see NIST SP 1800-8, Volume B.

Vulnerabilities
insecure network configuration
lack of an asset inventory
weak access controls
unpatched medical devices
Threats
targeted attacks
malware infections
disruption of services
Potential Risks:
If a malicious actor (threat) exploits a vulnerability in your network, the risks to your organization could include:
unauthorized access to critical systems
manipulation of infusion pumps (patient safety)
use of unsecured devices as a pivot point to other more critical systems (patient data/disruption of services)
Applying NIST Cybersecurity Framework
The NCCoE applied the NIST Cybersecurity Framework to determine which security controls could assist in mitigating these potential risks.
Asset Management
(ID.AM) – knowing what devices are
connected to your enterprise network and whether timely patches are
applied to limit vulnerabilities
Identity Management and Access Control
(PR.AC) –
knowing who and what systems can access devices and what those devices are being asked to do. This can limit
improper access and use of critical medical devices
Data Security
(PR.DS) – protecting sensitive data from improper access and manipulation
For the complete list, see NIST SP 1800-8, Volume B
Learn more about the five Functions of the NIST Cybersecurity Framework
Identify
This function protects and minimizes damage against a cybersecurity attack.
Some ways to identify risks include:
- Distinguish the devices, software, and data that a company will be using
- Share policies that cover roles and responsibilities of employees with access to sensitive data.
Protect
This function ensures the delivery of critical IT services throughout an organization.
Some ways to protect against risks include:
- Use software from trusted sources
- Conduct regular backups of critical data
- Perform timely updates to systems and software.
- Train employees to understand their roles in protecting private and company-wide data from cyber attacks.
Detect
This function ensures timely discovery of any cybersecurity events taking place.
Some ways to detect cybersecurity events include:
- Monitor unusual activities throughout your network, including by your employees.
- Investigate unauthorized access and connections to your network.
Respond
This function helps contain the impact of a detected cybersecurity event.
Some ways to respond to an attack or suspicious behavior:
- Have a detailed plan when facing an attack that includes steps for investigating and containing the attack while keeping operations up and running.
- Notify employees and customers who may be at risk from the cyber attack.
- Update training policies with lessons learned once the problem is resolved.
Recover
This function helps restore services that were impaired during the cybersecurity event.
Some steps to take when recovering from a cybersecurity event include:
- Restore equipment or areas of the network that were affected by the attack.
- Inform your employees on what happened and provide an explanation of your response to the attack.
NCCoE Solution: Defense in Depth
Firewall
VPN
Wireless Network Protection
Endpoint Protection/Intrusion Detection
Data Encryption
Asset Management
This NCCoE approach is modular and can be adapted to best fit your organization’s needs. One example detailed in this practice guide is network segmentation.
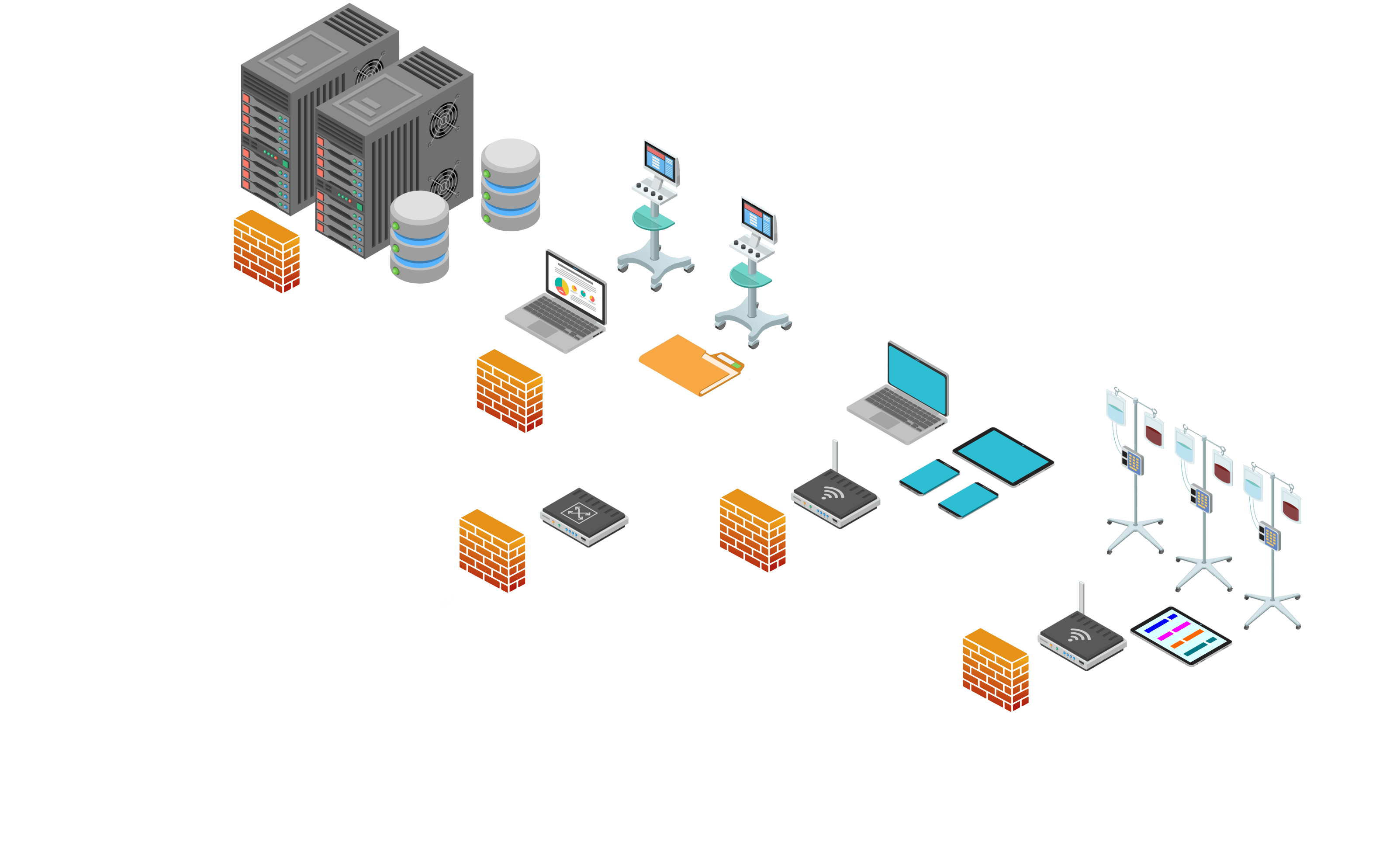
Network segmentation groups devices into zones that are protected by an internal firewall based on the function they serve for the Healthcare Delivery Organization (HDO). By limiting access from other, less trusted areas, firewalls can more effectively protect the enterprise network.

Controlling who or what systems access specific parts of the network is also part of this layered security approach. These layers of protection ensure the ecosystem is not vulnerable to a single point of failure.
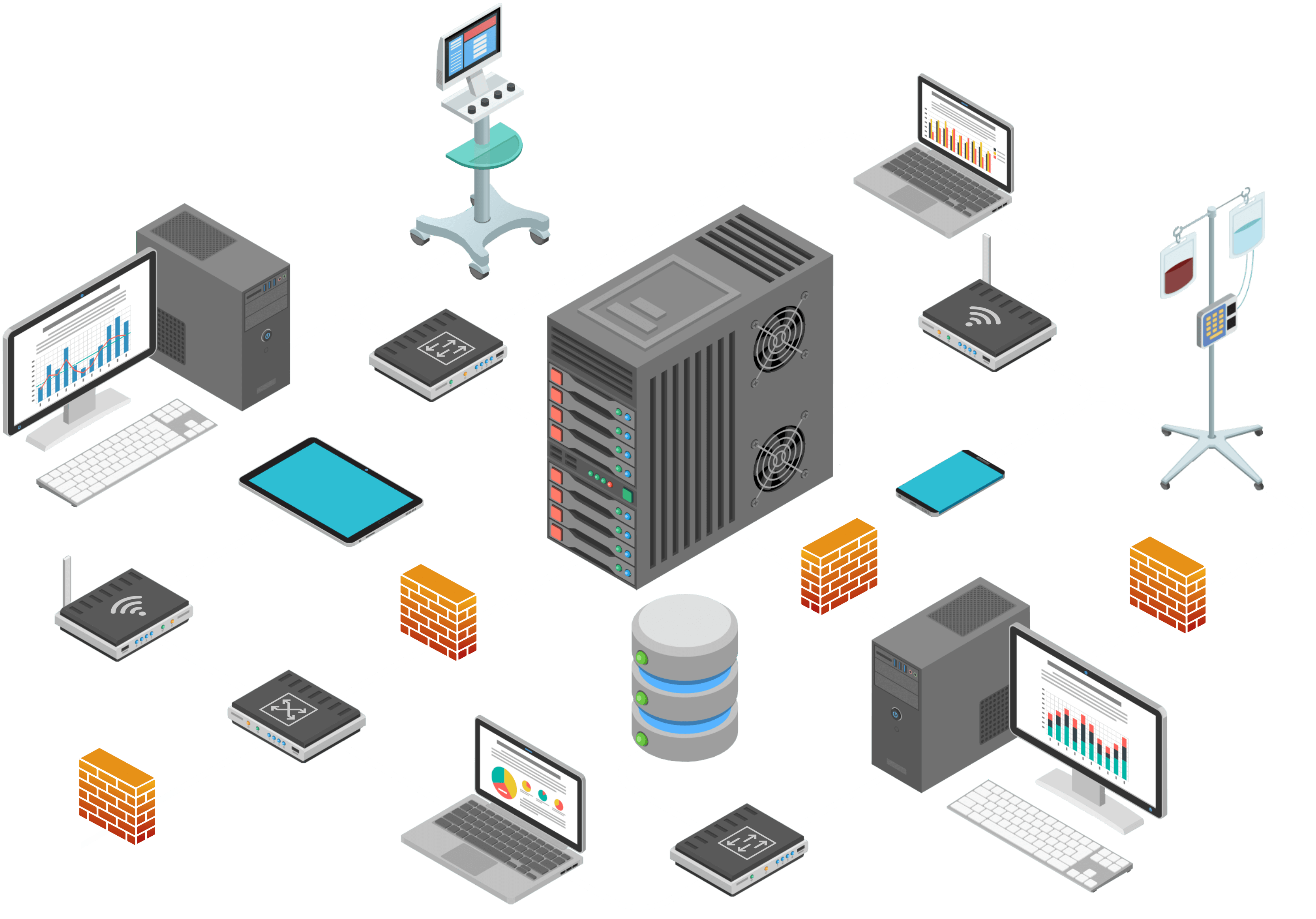
Technologies/Capabilities: Following are a sampling of technologies and capabilities deployed in the NIST SP 1800-8 practice guide to accomplish a defense-in-depth security solution.
Access Points/Wireless Local Area Network (LAN): authenticates and connects medical devices to a network and encrypts data in transit
Firewall/Router: provides network integrity protection
Switch: additional controls and enables network segmentation
Endpoint Protection: provides intrusion prevention, access controls, and application behavior controls.
Data Center Security: monitors network traffic for suspicious activity.
So how does the NCCoE solution come together to protect your organization’s network?
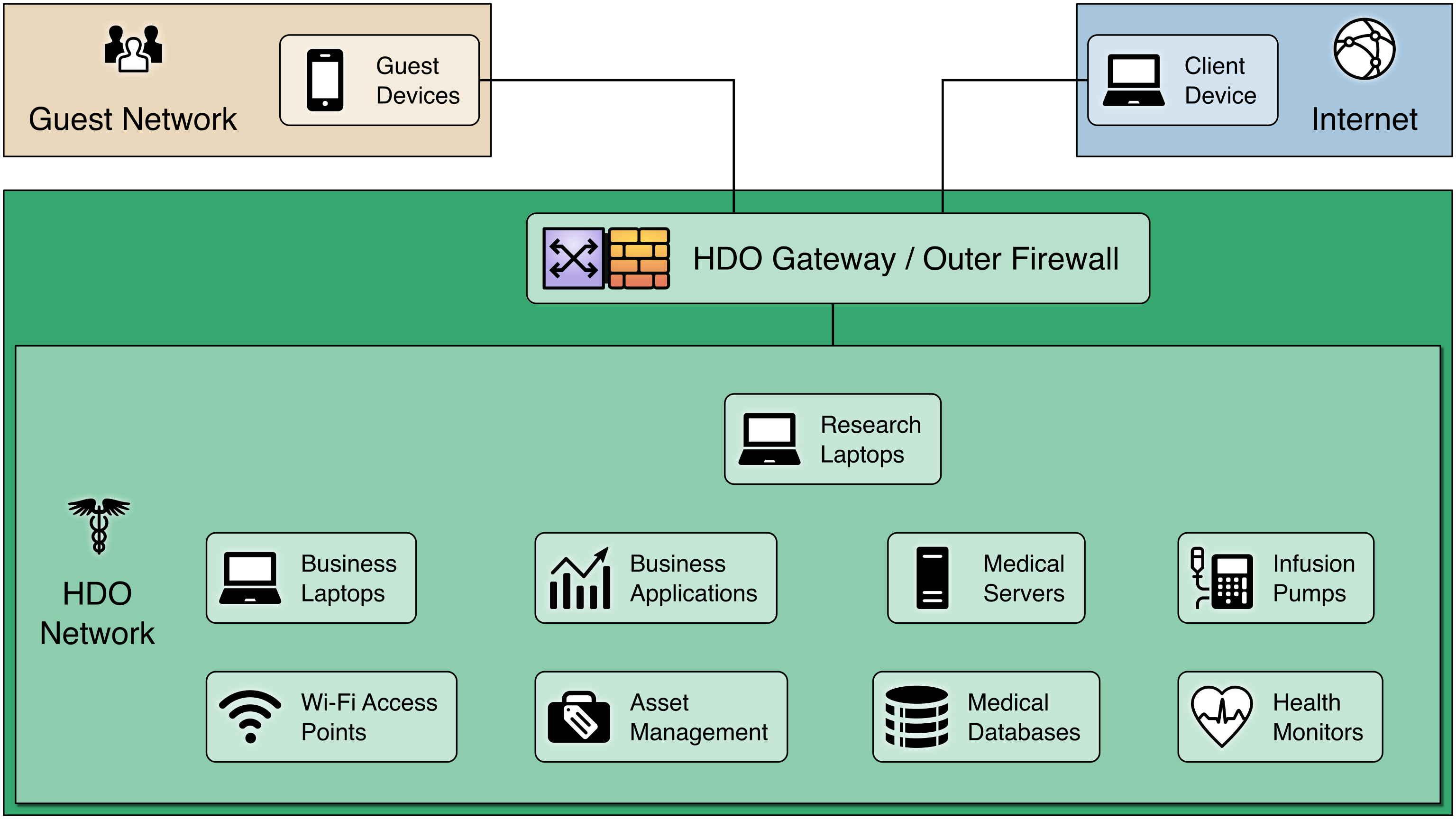
The following illustration offers a sample visualization of how network segmentation can be achieved to protect connected medical devices from external threats.
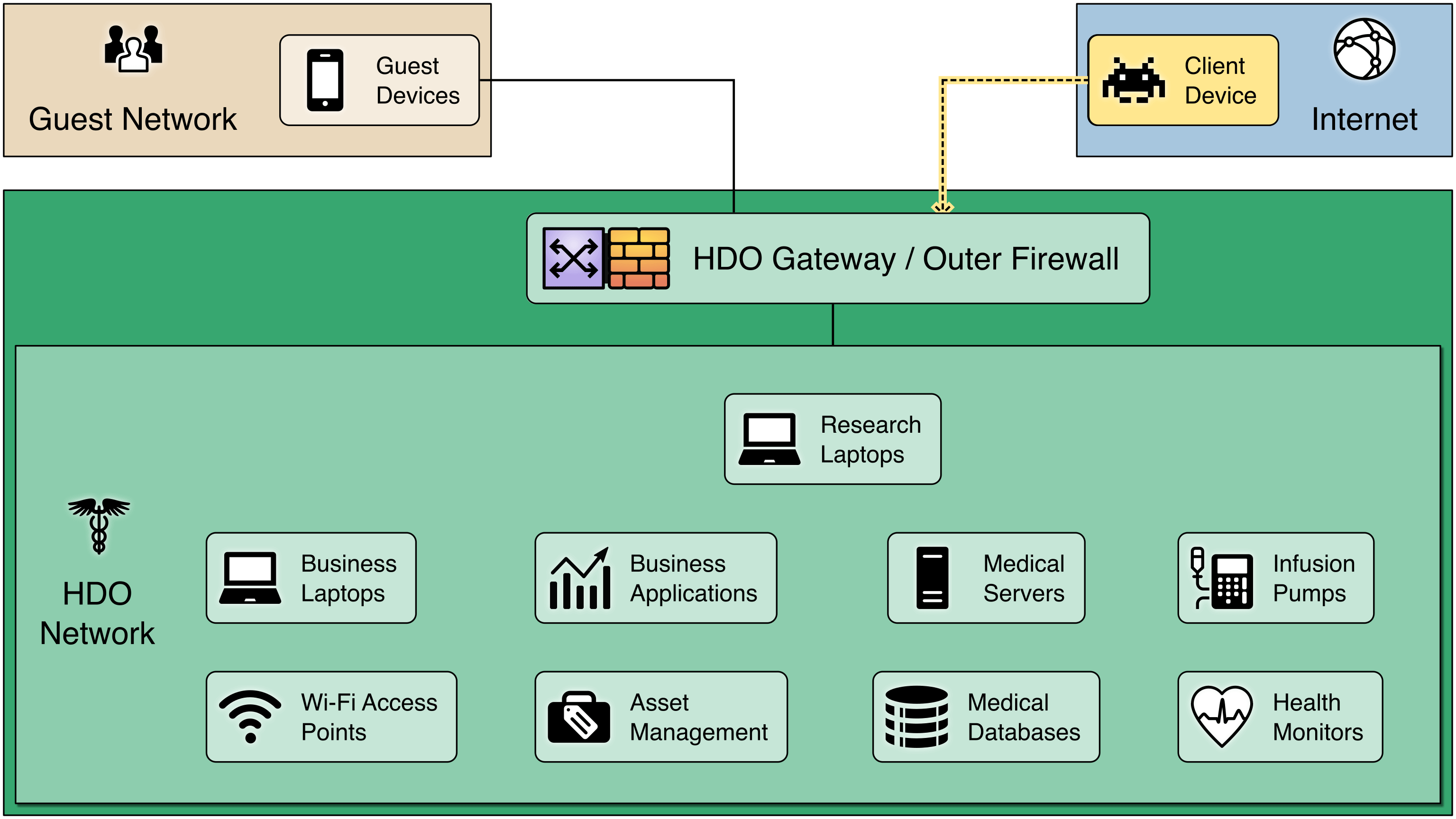
View of a Basic/Flat Network: Here is an example HDO network with a single firewall to protect it from external threats.
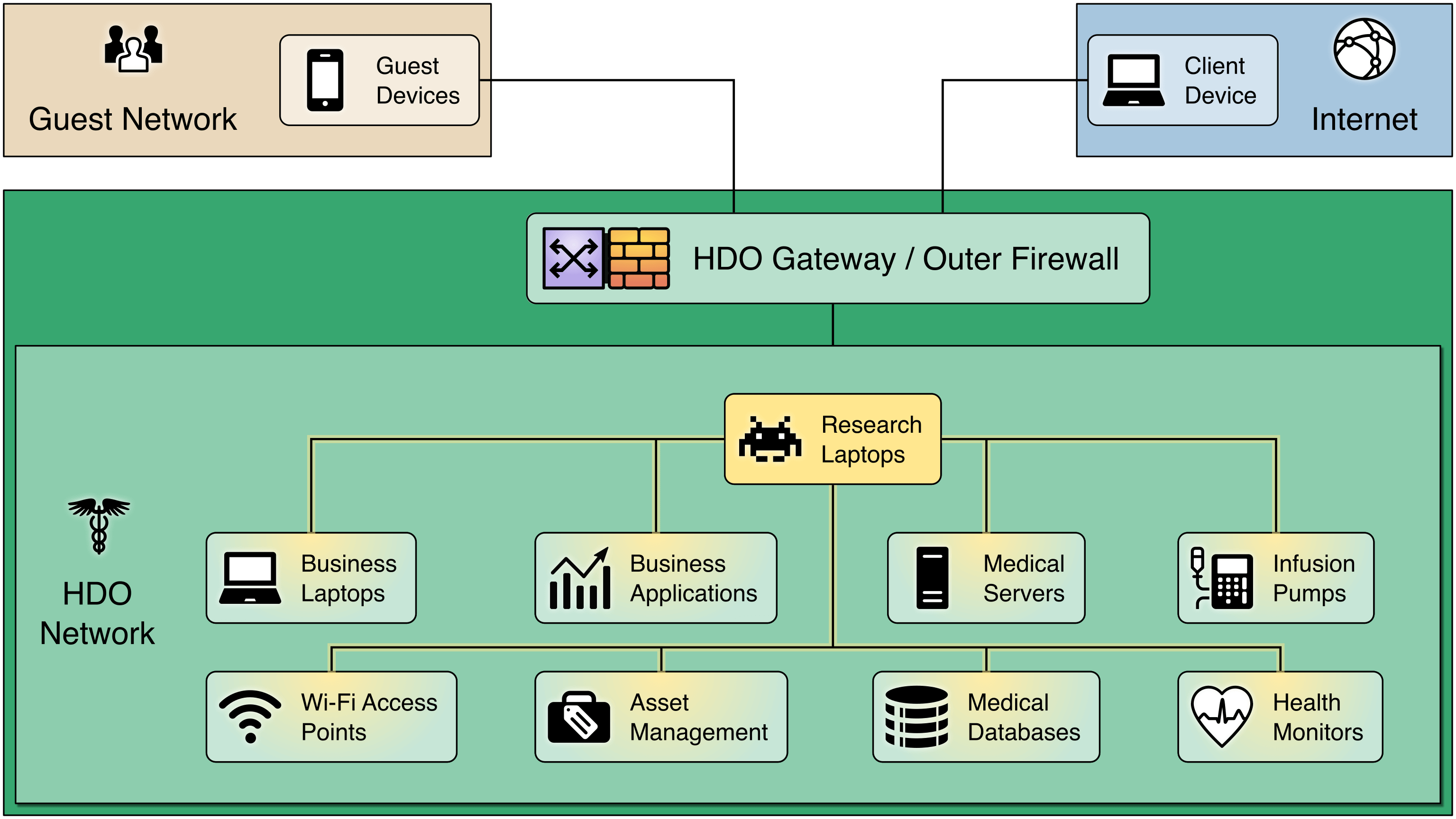
But once a device inside the HDO network is compromised, the firewall no longer helps.
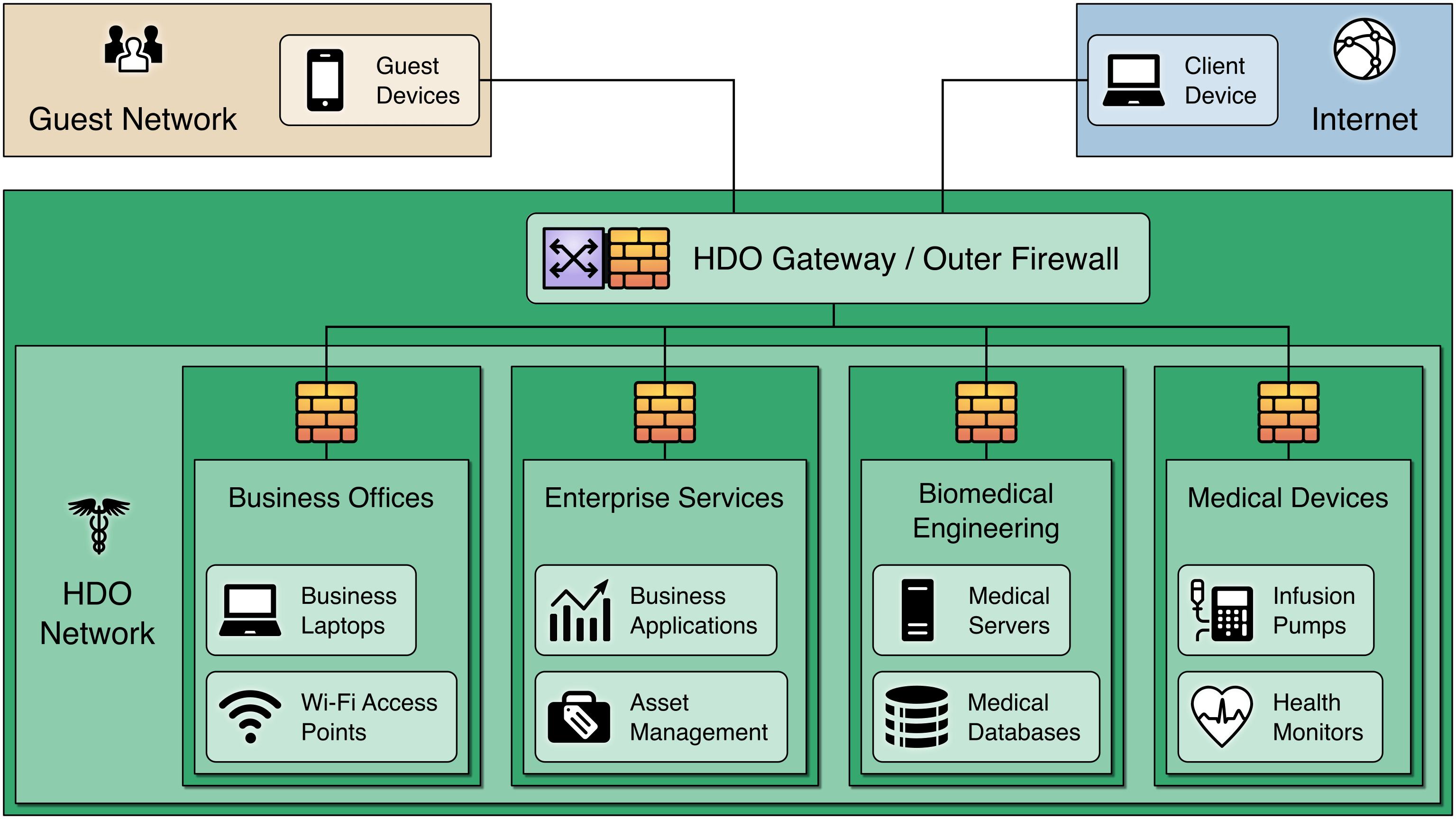
Segmenting the Network: Segmentation divides the network into multiple zones – each protected by its own firewall.
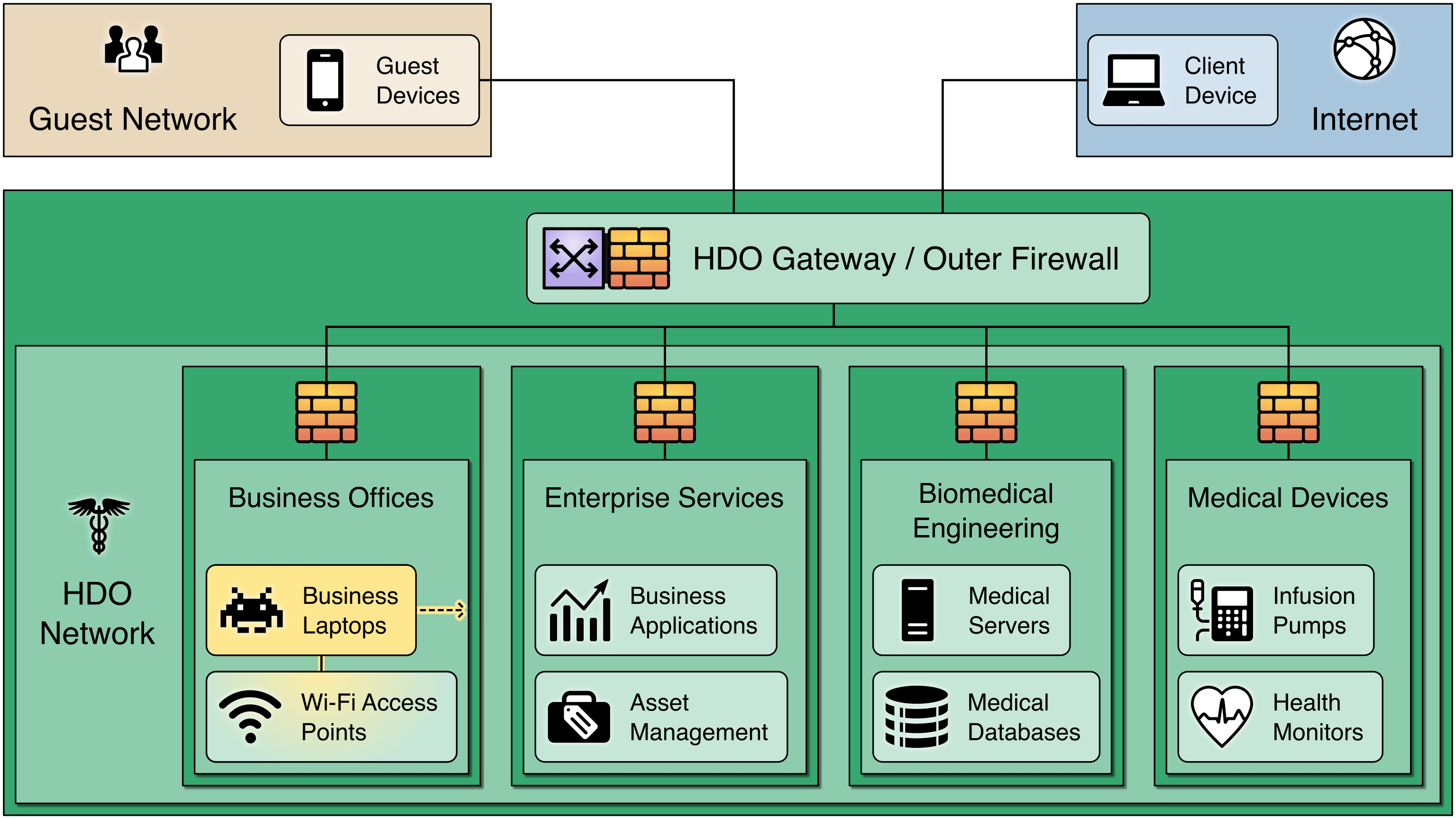
Firewalls can be configured to limit who or what devices can access various zones, preventing a breach in one zone from affecting other zones.
Segmentation is a single protective measure and should be combined with other techniques, such as:
multifactor authentication for authorized users
network monitoring
data protection efforts
For a comprehensive guide on security controls and technologies, see the practice guide.
Lifecycle Management
Establishing a product lifecycle management program is part of a holistic program for managing risks associated with
devices connected to your enterprise network. Each asset should be managed from introduction to retirement. Documenting
and tracking an asset’s life cycle will ensure the asset meet your organization’s mission and security goals.
Strategy
Identify the purpose of the asset and document interconnections to external systems and related security needs.
Plan
Evaluate security requirements for data processed by new assets. Develop a configuration management plan to maintain
security of these assets.
Design
Test asset capabilities and make necessary adjustments. Develop a deployment strategy for new assets.
Procure
The strategy, plan, and design phases should support the acquisition of assets that offer an appropriate combination of
security and functionality required for your organization’s needs.
Operate
Establish an onboarding process for all devices (e.g., asset tagging and inventory tracking). This
should include setting baseline security configurations and implement digital certificates to allow for device
authentication.
Maintain
Follow manufacturer recommended updates and ensure regular patching. Be aware of potential vulnerabilities and risks that they introduce into the enterprise, which could affect other
enterprise devices.
Modify
Over time, the operational environment may change, and those changes may require modifications to the asset. If
necessary, modifications should be in accordance to manufacturer recommendations and aligned to broader cybersecurity
plans of your organization.
Dispose
Develop plans for discarding system information, hardware, and software. Ensure the orderly termination of the system
and the preservation of vital information.

The NCCoE Practice Guide, NIST SP 1800-8, Securing Wireless Infusion Pumps in Healthcare Delivery Organizations, is a comprehensive resource that can help your organization implement a practical cybersecurity solution to protect your patients, business, and reputation. Read the guide today.
If you have any questions about this guide or about other NCCoE healthcare sector work, contact the project team at hit_nccoe@nist.gov.